Currently Empty: $0.00
Sigma Rules: Steps to Follow in Threat Hunting

Sigma rules are a cornerstone of threat hunting and play an important role in optimisation processes.
However, the effective application of alpha and sigma rules can be challenging.
For this reason, the correct application of sigma rules in threat hunting is of key importance. With a strong strategy, cyber threats can be detected and eliminated immediately.
It is important to follow the correct steps.
Definition of Sigma Rules
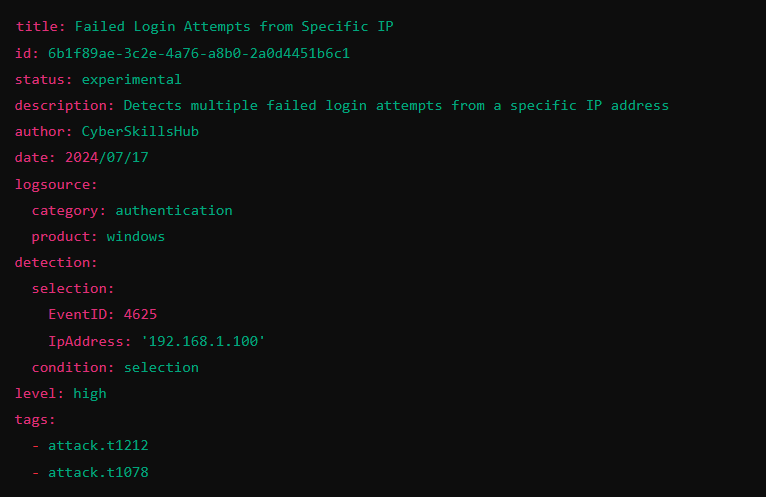
Sigma rules are specific rules used for threat hunting in the field of cyber security.
These rules are used to detect the network behaviour of attackers and evaluate it by statistical analysis.
Developed in 2016 by Florian Roth, the Sigma rules are written in a clear and understandable format.
They are similar in structure to other detection rules such as Yara and Snort, but are more flexible in format.
Thanks to this flexibility, Sigma rules can be easily used in different systems and platforms.
Importance of Sigma Rules
Sigma rules are a set of principles and methods that are vital to the success of threat hunting.
These guidelines provide standards that every information security professional should follow. They are essential to optimise the process of identifying, assessing and responding to threats. Sigma rules enable threat hunters to make more accurate and timely decisions; the right leadership increases the effectiveness of these decisions.
Sigma rules provide a robust framework for threat hunting. Thanks to this structure, threats are controlled more effectively, risks are minimised and security breaches are prevented.
As a result, sigma rules are the foundation for sustainable success in threat hunting. The rigorous application of these rules strengthens organisations’ security strategies and makes them more resilient to data breaches. Thus, companies can ensure their success by taking a proactive stance against security threats.
What is Threat Hunting?
Threat hunting is an advanced application within the framework of cyber security. It operates as an active defence mechanism.
This process includes proactive steps to detect and eliminate cyber threats. The focus is on identifying potential threats to security systems.
Threat hunters try to predict possible attacks by analysing current threats. However, they also optimise anomaly detection and incident response processes.
Threat hunting strengthens the security posture of organisations. By creating early warning systems, it ensures that threats are prevented before they grow, thus minimising cyber security risks.
This process requires continuous learning and development. Up-to-date knowledge and analytical skills are vital for effective threat hunting.
Click to learn more about threat intelligence tools and their uses.
The Role of Sigma Rules in Threat Hunting
Sigma rules are a critical component that increases the effectiveness and quality standards of threat hunting. It plays an important role in identifying threats.
Introduced in 2016, sigma rules have been recognised as a standard and open format in cyber security. These rules provide a universal language for monitoring cyber threats.
This helps threat hunters to consolidate data from different security systems. Thanks to sigma rules, threats can be detected more quickly and effectively.
Sigma rules reduce the burden of manual analysis in the threat hunting process. Thanks to these automated rules, threat hunters can work on more strategic tasks.
With Sigma rules, it is possible to catch threats at an early stage. This provides a great advantage in ensuring the security of organisations.
Sigma rules stand out as a critical component that increases the effectiveness and quality standards of threat hunting. If you would like to specialise further in this area, take a look at our Cyber Security Training Programmes for professional development.
Steps to Implement Sigma Rules
Implementing sigma rules effectively requires a strategy and planning. The first step is to identify the integration points of sigma rules by analysing existing threat hunting processes. Then, it is important to adapt the rules to the system and create appropriate filters. Training and continuous updates should ensure that teams use these rules effectively. Continuous improvements should be made in the monitoring and reporting processes of sigma rules, and the results should be evaluated regularly.
Threat Analysis
Sigma rules help to optimise the threat analysis process.
Accurate analysis of data enables early detection of security vulnerabilities and minimises risks.
A thorough examination of the data is critical when conducting threat analyses. In this process, sigma rules reduce errors with automated analyses and provide more accurate results.
In this context, threat analyses not only evaluate the current situation, but also take a proactive approach against potential threats that may occur in the future. This approach significantly strengthens the security posture of organisations.
Anomaly Detection with Sigma Rules
Sigma rules offer a reliable and systematic approach to anomaly detection.
- Data Collection: Data from the system needs to be continuously collected and analysed.
- Norm Determination: It is important to determine the normal distribution of the data and to draw the anomaly boundaries.
- Real-Time Monitoring: Real-time monitoring enables instant detection of possible threats.
- Alarm Systems: It is necessary to install and optimise alarm systems for anomaly detection.
- Regular Review: Sigma rules must be reviewed regularly to increase their effectiveness.
These steps increase the efficiency and accuracy of the anomaly detection process.
By applying Sigma rules, threat hunting processes can be more secure and proactive.
With this method, organisations can reduce operational risks by minimising security vulnerabilities.
Risk Assessment
Risk assessment is a critical step in threat hunting processes. This step enables organisations to anticipate potential hazards and take precautions.
- Threat Identification: Identification and cataloguing of potential threats.
- Influencing Factors: Analysing the internal and external factors affecting the occurrence of threats.
- Analysing Impacts: Assessing the impacts that may occur if threats are realised.
- Prioritisation: Ranking of threats according to their potential impact on the organisation.
- Preventive Measures: Planning preventive measures to be taken against possible threats.
With these steps, organisations can take a proactive approach to threat hunting.
Risk assessment should be carried out in parallel with sigma rules.
This integration leads to more effective and faster results in detecting security anomalies.
Creating an Action Plan
The action plan is a critical element for the success of the threat hunting process. Sigma rules also play an important role here.
- Identification of Objectives: Clear and unambiguous definition of the security objectives to be achieved.
- Identification of Requirements: Determining the resources and competences required to achieve the objectives.
- Establishment of Incident Response Teams: Formation of competent teams and clarification of roles and responsibilities.
- Establishing Protocols: Determining the procedures and steps to be followed when threats are realised.
- Training and Awareness Activities: Training and awareness raising of all personnel on threat hunting processes.
Through these steps, organisations can develop a proactive defence mechanism against potential threats.
Continuous updating and refinement of the action plan ensures a dynamic approach to threat hunting.
Application Tools and Software
Security is strengthened when it meets technology.
Threat hunting within the framework of Sigma rules requires the use of the right tools and software. Application tools and software used in this process provide important support to detect, analyse and react to security vulnerabilities. In particular, big data analysis tools, machine learning algorithms and artificial intelligence-based technologies are among the most critical components of the sector.
The selection of tools and software should be done with care.
The application tools and software used for threat hunting – where success is heavily influenced – should be carefully evaluated. For example, SIEM (Security Information and Event Management) solutions are very useful in threat hunting.
A well-structured toolset guarantees successful results in threat hunting. In today’s world where technology is constantly evolving, businesses can always be one step ahead by keeping themselves up-to-date in this field. Thus, they can keep their defences against security threats at the highest level.
You can find the best free and paid cyber security tools for threat hunting here.
Adaptation and Optimisation of Sigma Rules
The adaptation of Sigma rules improves the efficiency of processes.
Effective implementation of these rules not only strengthens threat hunting processes, but also improves the overall security posture. Optimising sigma rules improves organisations’ threat hunting performance and minimises false positive rates. This process is complemented by continuous evaluation and improvement cycles, thus ensuring protection against the latest threats.
Improves efficiency and accuracy.
Users should increase flexibility in the adaptation of sigma rules and regularly review their rules. By doing so, they can quickly integrate updates that incorporate the latest threat intelligence. Furthermore, the integration of machine learning algorithms and big data analysis plays a major role in optimising sigma rules.
Continuous optimisation of Sigma rules encourages proactive approaches in threat hunting processes. This enables businesses to be better prepared for potential threats and strengthens their security infrastructure. New methods to be developed for 2024 and beyond are critical for businesses to maintain their competitiveness in this challenging environment. Therefore, organisations that regularly review and optimise their sigma rules can successfully sustain their digital security strategies.
If you would like more information and training on this topic, you can join our cyber security courses from beginner to expert.
Success Stories and Case Studies
The application of Sigma rules in threat hunting has enabled many businesses to achieve great success in the field of cyber security.
One of these success stories belongs to a global e-commerce giant.
The company has significantly reduced data breaches by actively using sigma rules.
As a result, it regained customer confidence and increased sales.
Another example is the practices of an organisation operating in the health sector; thanks to sigma rules, they have prevented cyber attacks to a great extent.
These and similar success stories demonstrate how effective sigma rules are in threat hunting.
You can visit the SigmaHQ GitHub page to learn more about sigma rules and access existing rule sets. This resource explains how sigma rules provides comprehensive information on how to write and implement.
Frequently Asked Questions About Sigma Rules
What are the Sigma rules?
Sigma rules are statistical methods used in threat hunting processes. These rules are used to detect abnormal behaviour and to identify security threats in advance. Sigma rules determine deviations by analysing the normal distribution of data and identify threats based on these deviations. In this way, security teams can take proactive measures against potential threats.
Why are sigma rules important?
Sigma rules offer a systematic and efficient approach to threat hunting processes. These rules ensure that potential threats are detected early and managed effectively. It also helps security teams to be more proactive and minimise potential risks. Sigma rules increase the success of security operations by providing a standardised methodology in threat hunting.
How are Sigma rules applied?
Sigma rules are applied by following certain steps in threat hunting processes. Firstly, threat scenarios are defined and appropriate rules are created for these scenarios. Then, these rules are integrated into security information and event management (SIEM) systems. Finally, the effectiveness of the rules is evaluated and optimised through continuous monitoring and updates.
Who developed the Sigma rules?
The Sigma rules were developed by security experts Florian Roth and Thomas Patzke. These rules were created to standardise threat hunting and incident detection processes. As an open source project, Sigma is continuously being developed with contributions from the worldwide security community. This facilitates collaboration and information sharing between different security teams.
In which sectors are Sigma rules used?
Sigma rules are used in many sectors such as finance, healthcare, energy, telecommunications and government. These rules can be adapted to detect and manage the unique threats in each sector. Especially in industries with high security requirements, Sigma rules make threat hunting processes more effective. Thus, organisations increase operational security by minimising cyber security risks.







