Currently Empty: $0.00
Web3 OSINT: Essential Investigation Techniques for Blockchain Security
OSINT, originally developed for military intelligence during the Cold War, has evolved into a crucial investigative framework for the complex world of Web3 and blockchain technology. Today, this intelligence-gathering approach helps combat cryptocurrency crime, track illicit funds, and investigate sophisticated digital asset hacks across decentralised platforms.
Security analysts and researchers use specialised OSINT techniques to conduct on-chain analysis, monitor wallet activities, and examine smart contracts for potential vulnerabilities. Furthermore, advanced OSINT tools, enhanced by artificial intelligence and machine learning, enable investigators to analyse social media sentiment, track malicious actors, and identify emerging threats in the Web3 ecosystem. This comprehensive guide explores the essential investigation methods, tools, and strategies for conducting effective Web3 OSINT operations, helping security professionals strengthen their blockchain security capabilities.
Web3 OSINT Tools and Technologies
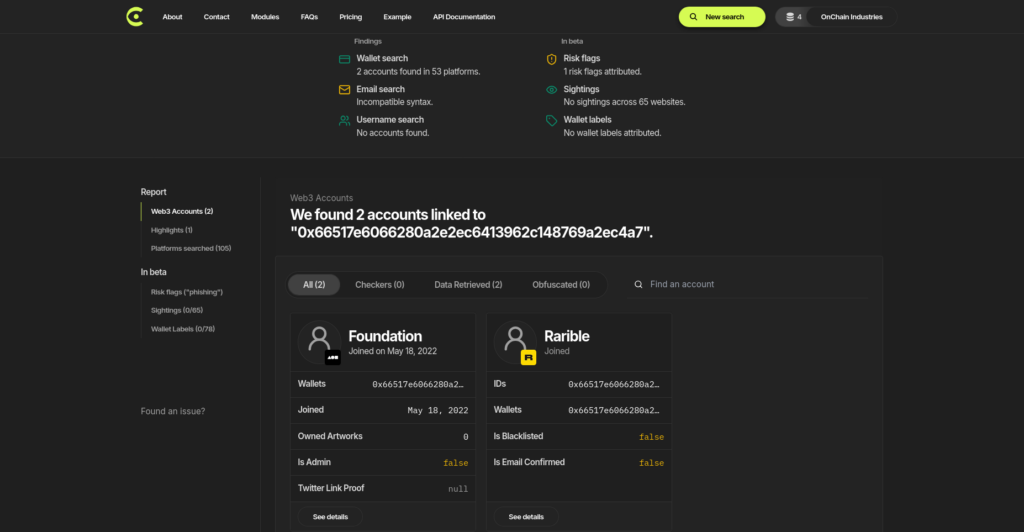
Modern blockchain investigators rely on specialised tools to conduct thorough investigations across decentralised networks. These tools form the backbone of effective Web3 OSINT operations, enabling investigators to track transactions and analyse complex blockchain data.
Blockchain Explorers and Analytics Platforms
Blockchain explorers serve as the primary gateway for investigating cryptocurrency transactions and wallet activities. Specifically, platforms like Etherscan, Polygonscan, and BscScan allow investigators to examine transactions, addresses, and smart contracts in detail. Additionally, advanced analytics platforms such as Chainalysis process more than 1 billion mapped addresses linked to real-world entities.
Smart Contract Analysis Tools
Smart contract analysis tools help identify vulnerabilities and potential security risks in blockchain applications. Particularly, tools like Slither offer extensive vulnerability detection capabilities with over 92 built-in detectors. These tools examine contract code for:
- Syntax and business logic errors
- Potential security vulnerabilities
- Gas consumption issues
- Reentrancy vulnerabilities
Data Visualisation Solutions
Data visualisation tools transform complex blockchain data into comprehensible formats for analysis. Consequently, these solutions help investigators reveal patterns of unusual activity hidden in high transaction volumes. Moreover, visualisation capabilities include:
- Network mapping of transaction flows
- Timeline analysis of blockchain events
- Interactive exploration of wallet relationships
- Pattern recognition in transaction data
Through clever filtering techniques, investigators can eliminate clutter and focus on specific value thresholds or time ranges. Similarly, these tools enable the export of annotated reports as high-resolution images or PDFs for team collaboration and case documentation.
Advanced Chain Analysis Techniques
Blockchain analysts employ sophisticated techniques to track transactions across multiple networks and investigate suspicious activities. Indeed, investigators have linked over GBP 11.12 trillion worth of cryptocurrency transactions to real-world entities since 2014.
Privacy Coin Investigation Methods
Investigators face unique challenges when examining privacy-oriented cryptocurrencies due to their built-in anonymity features. Nevertheless, forensic analysis can uncover valuable artefacts from various sources, including volatile memory, network traffic, and system hard drives. Accordingly, investigators analyse transaction patterns, examine exchange interactions, and monitor wallet behaviours to identify potential illicit activities.
Cross-Chain Correlation Strategies
Cross-chain analysis has become essential as criminals increasingly utilise chain-hopping techniques to obscure transaction trails. Investigators track funds through:
- Exchange flows and deposit/withdrawal patterns
- Transaction frequencies and volumes
- Interactions with high-risk entities
- Smart contract usage patterns
Undoubtedly, these profiling techniques have proven effective, whereas investigators have successfully traced funds through mixers, cross-chain bridges, and complex smart contracts. Advanced algorithms continuously scan blockchains to detect irregularities and flag suspicious activities for further investigation.
Social Intelligence in Web3

Social intelligence (SOCMINT) plays a vital role in Web3 investigations, enabling analysts to gather crucial insights from online communities and digital interactions. Initially, investigators combine on-chain analysis with off-chain OSINT to build comprehensive understanding of blockchain activities.
Community Analysis Methods
Web3 community analytics translate blockchain data into digestible reports of user insights and activity patterns. Investigators utilise both passive and active OSINT approaches:
- Link analysis tools (Analyst’s Notebook, Maltego, Lampyre)
- Social media monitoring platforms
- Advanced search techniques (Google Dorks)
- Case management systems
Developer Activity Monitoring
Developer activity serves as a key indicator of project legitimacy and progress. Notably, tracking GitHub events provides better insights than commit counts alone. These events encompass:
- Code pushes
- Issue interactions
- Pull request discussions
- Repository modifications
Sentiment Analysis Techniques
Sentiment analysis, essentially opinion mining, evaluates public perceptions of cryptocurrencies through social media monitoring. Subsequently, investigators follow a structured process:
- Generate platform API keys
- Install required analysis packages
- Extract sentiment data
- Generate polarity scores
- Develop trading signals
The Natural Language Toolkit (NLTK) generally processes large volumes of social media data to determine sentiment patterns. Through these methods, investigators can identify potential risks, track market trends, and evaluate project legitimacy.
Threat Actor Investigation Methods

Threat actors in the Web3 space employ sophisticated techniques to execute attacks, essentially requiring investigators to develop comprehensive detection and analysis methods. Recent findings indicate that cryptocurrency heists have resulted in over GBP 9.53 billion in stolen digital assets since 2020.
If you’re interested in understanding the tactics of threat actors, you can learn more about the North Korean cybercrime group APT38 here, which has been involved in sophisticated cryptocurrency heists.
Attack Pattern Analysis
Investigators examine attack signatures through systematic approaches that focus on identifying common patterns. Altogether, threat actors often utilise various obfuscation techniques, including:
- CoinJoins for transaction amalgamation
- Mixer services for cryptocurrency scrambling
- Cross-chain bridges for asset transfers
- Nested exchanges for fund extraction
For a structured approach to identifying and analyzing attack patterns, security analysts can utilize the MITRE ATT&CK framework, which provides detailed mappings of adversarial tactics and techniques used by threat actors worldwide.
Infrastructure Mapping
Blockchain forensics experts map criminal infrastructure by analysing on-chain and off-chain data sources. Straightaway, investigators utilise specialised tools to track transactions across multiple blockchains, with law enforcement agencies successfully seizing almost GBP 7.94 billion worth of cryptocurrency through these methods.
Attribution Techniques
The process of attributing blockchain activities to real-world entities requires a multi-faceted approach. Soon after detecting suspicious activities, investigators follow these essential steps:
- Analyse blockchain transaction patterns
- Examine exchange interactions
- Monitor wallet behaviours
- Track cross-chain correlations
- Investigate social media footprints
Otherwise, threat actors might employ sophisticated evasion techniques, making attribution more challenging. For instance, criminals often create realistic websites and social media profiles using AI-generated content to increase credibility. Through meticulous analysis of these digital footprints, investigators can uncover valuable evidence linking pseudonymous addresses to real-world entities.
The implementation of visual mapping expedites the recognition of intricate patterns commonly employed in money laundering, enabling investigators to identify complex transaction flows. Advanced algorithms continuously scan blockchains to detect irregularities, flagging suspicious activities that warrant further investigation.
Conclusion
Web3 OSINT has emerged as a critical framework for blockchain security investigations, transforming how analysts track cryptocurrency crime and protect digital assets. Through specialised blockchain explorers, smart contract analysis tools, and advanced visualisation platforms, security professionals now possess powerful capabilities for thorough investigations across decentralised networks.
Advanced chain analysis techniques enable investigators to track over GBP 11.12 trillion worth of cryptocurrency transactions, while social intelligence methods provide crucial insights into community behaviour and project legitimacy. These comprehensive approaches help security teams identify suspicious patterns and attribute pseudonymous addresses to real-world entities.
Threat actor investigation methods continue advancing alongside criminal techniques, as demonstrated by successful law enforcement operations seizing GBP 7.94 billion in cryptocurrency assets. This cat-and-mouse game drives constant innovation in detection and analysis approaches. Security analysts must stay current with these evolving investigation techniques while maintaining rigorous standards for evidence collection and analysis.
The combination of sophisticated tools, cross-chain correlation strategies, and social intelligence creates a robust framework for blockchain security investigations. These methods equip investigators with the necessary capabilities to combat cryptocurrency crime effectively and protect the growing Web3 ecosystem.
FAQs About Web3 OSINT
What is Web3 OSINT and why is it important for blockchain security?
Web3 OSINT is an intelligence-gathering approach used to investigate cryptocurrency crime, track illicit funds, and examine digital asset hacks across decentralised platforms. It’s crucial for blockchain security as it helps analysts conduct on-chain analysis, monitor wallet activities, and identify potential vulnerabilities in smart contracts.
What are some essential tools used in Web3 OSINT investigations?
Essential tools for Web3 OSINT investigations include blockchain explorers like Etherscan and Polygonscan, analytics platforms such as Chainalysis, smart contract analysis tools like Slither, and data visualisation solutions. These tools helpinvestigators track transactions, analyse blockchain data, and identify patterns of unusual activity.
How do investigators handle privacy coins in their analyses?
Investigators use specialised techniques to examine privacy-oriented cryptocurrencies, including analysing transaction patterns, monitoring wallet behaviours, and examining exchange interactions. They also employ forensic analysis on various sources such as volatile memory, network traffic, and system hard drives to uncover valuable artefacts.
What role does social intelligence play in Web3 investigations?
Social intelligence is vital in Web3 investigations as it allows analysts to gather crucial insights from online communities and digital interactions. This includes community analysis, developer activity monitoring, and sentiment analysis techniques. These methods help investigators identify potential risks, track market trends, and evaluate project legitimacy.
How do investigators attribute blockchain activities to real-world entities?
Attributing blockchain activities to real-world entities involves a multi-faceted approach. Investigators analyse blockchain transaction patterns, examine exchange interactions, monitor wallet behaviours, track cross-chain correlations, and investigate social media footprints. They also use visual mapping and advanced algorithms to detect irregularities and flag suspicious activities for further investigation.







