Currently Empty: $0.00

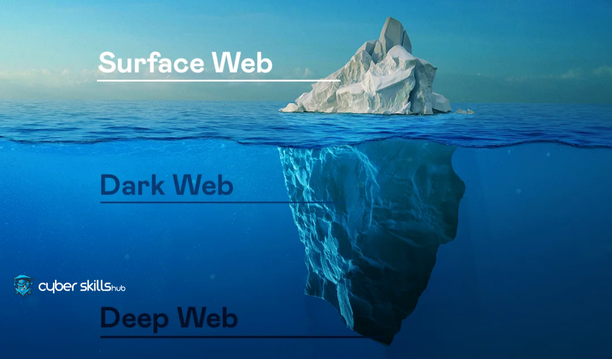
Like the mysterious world of the deep oceans, much of the internet is hidden from view. The websites we browse on the surface are only the visible part of the internet, the real depths are waiting to be explored.
Just the tip of the iceberg.
When looked at carefully, exploring the depths of the deep web reveals a rich ecosystem with millions of terabytes of information and resources. Security experts seek to unlock this information.
Definition of Deep Web
The Deep Web is the lower layer of the web, inaccessible from search engines on the surface of the Internet, offering anonymity and privacy to its users, often requiring special permissions and appropriate software. This layer includes services that cannot be viewed with standard browsers and search engines, such as private databases, archives and online banking. Security experts focus on securely exploring these mysterious parts of the internet, using specialized techniques and tools to reach these depths.
Surface Web and Deep Web Difference
The part of the internet that is easily accessed by users and displayed in popular search engines is called the Surface Web. This area includes the websites, news platforms and social media sites we visit on a daily basis. The Surface Web represents only part of the internet.
The Deep Web is the lower layer of the Internet that cannot be found with standard search engines and requires special access methods. For example, academic databases, private forums and information that governments keep off-limits are on the Deep Web. Therefore, the Deep Web is much larger than the surface and often contains more confidential information.
The size of the Deep Web is an estimated 400 to 500 times larger than the Surface Web.
The Deep Web, which is important for protecting information and ensuring anonymity, is mostly not for malicious purposes, but for legitimate uses with a need for privacy. This layer, which can be accessed using specialized tools and methods, can contain valuable data such as internal networks, research and development work. Exploration of this area is a specialty of cyber security experts.
Structure and Scope of the Deep Web
The Deep Web contains web pages that are not indexed by standard search engines. This is a huge pool of data that forms the other side of the internet.
- Need for Special Access: Accessing Deep Web content requires specialized browsers and knowledge of the right access points.
- Security and Anonymity: Encryption of communications and the concealment of user credentials are of utmost importance on the Deep Web.
- Valuable Data Repositories: Critical information such as research, private databases and internal networks are all within the scope of the Deep Web.
- Access Restriction: Governments and private organizations can store sensitive information on the Deep Web so that access is only possible by authorized persons.
The Deep Web can host sensitive information, such as research and development data, so it requires high security measures.
This layer of knowledge requires in-depth expertise in cybersecurity, as protecting and managing data in this environment requires professional know-how.
How to Access the Deep Web?
Access to the Deep Web requires specialized software and configurations. Specialized browsers, such as Tor, routes internet traffic through relays operated by volunteers around the world, ensuring the anonymity of users and opening the doors to the Deep Web. However, it is important to remember that there are dangerous areas of the Deep Web, so it is essential to take additional precautions for your safety. The use of Virtual Private Networks (VPNs) and antivirus software will minimize the risks you may face when navigating this area.
Required Software and Browsers
Access to the Deep Web requires the use of specific software and browsers. The most widely known browser is Tor Browser.
Tor Browser has a complex network structure that allows users to remain anonymous on the Internet. At the heart of this structure is the routing of user data through relays distributed around the world.
Another tool that provides anonymity is Virtual Private Network (VPN) technology. A VPN encrypts users’ activities on the Internet by hiding their real IP addresses, increasing security.
While using Tor and VPNs is important, you also need a good antivirus program to ensure your complete security. This software protects against malware.
During access, it is critical that these tools are up-to-date and correctly configured to ensure a secure environment. For this reason, it is important to stay informed about the software used.
Security Measures for Access
Securely accessing the Deep Web requires careful preparation and the use of the right tools. In this context, the steps to be followed are outlined.
- Advanced Firewall Settings: The first step in protecting your access point against external threats. Enable advanced features of your firewall and continuously update it against potential leaks.
- Strong Encryption Protocols: Strengthen the encryption protocols of your VPN or Tor network; use strong algorithms like AES. To learn more about encryption, click here.
- Two-Factor Authentication (2FA) : Layer access to your accounts and the tools you use and enable 2FA as an extra layer of security.
- Regular Software and System Updates: Ensure that all relevant software and your operating system contain the latest security patches.
- Using an Anonymity-Focused Browser: Maximize your effectiveness by using security and anonymity-focused browsers such as Tor.
When building your security strategy, it is imperative that you thoroughly understand the importance of each of these steps and how to implement them.
In addition to these measures, it is vital to stay vigilant in the face of ever-changing cyber threats and keep your cybersecurity knowledge up to date.
In a world of increasing cyber threats, the secure discovery of complex internet layers such as the Deep Web is of great importance, especially for cyber security experts. In this context, taking Cyber Threat Intelligence Training can be a critical step in understanding the complex structure of the deep web and ensuring security in these areas. The training equips cybersecurity professionals against the dangers in this mysterious world and protects them as they navigate the hidden layers of the internet. Cyber Threat Intelligence Training helps security professionals improve their ability to gather information, analyze threats, and prevent potential harm in these deep and complex layers of the internet. With this training, you can have the necessary skills and knowledge before diving into the mysteries of the Deep Web.
What is Found on the Deep Web?
The Deep Web hosts information that is not indexed by the Internet’s search engines and therefore cannot be found with standard search engines. It is therefore possible to find a variety of resources that are not publicly accessible, such as private databases, archived documents, academic journals and government reports.
Secure communication services, especially those used by organizations whose data privacy is critical, are common elements of the Deep Web. There are also forums that protect the identities of their users, sites that make their content available only to specific individuals or groups, and various cryptographic services. Such resources are often located on the Deep Web due to their high security requirements and the need for anonymity.
Legal and Useful Content
The Deep Web is not only a place of illegal activity, but also home to many legal and beneficial resources.
- Academic Research and Articles: Scholarly works produced by universities and research institutions are generally available through databases in this area.
- Government Reports: Legal and official information, as well as legal documents that are often not publicly accessible, are available on the Deep Web.
- Library Archives: The digital archives of many libraries can be explored by accessing authors’ works and historical documents on the Deep Web.
- Specialized Software and Databases: Some proprietary and commercial software is offered on the Deep Web for limited user audiences or specialized areas that require functionality.
- Private Forums and Communities: Private groups related to specific professions or hobbies can conduct their discussions on the Deep Web, creating a freer and safer environment.
These resources take advantage of the structure of the Deep Web to provide user-specific information or quality content.
Access to this type of content is usually through specialized search engines or direct links, which guarantees that the information is used by the right audience.

Illegal Activities and Dark Spaces
In the labyrinth of the Deep Web is a section called the “Dark Web” or “Darknet”, where illegal markets and activities congregate. These areas are secluded, hidden corners of the internet.
In these dark corners, illegal transactions such as drug sales and arms trafficking take place. There are also markets and services for stolen data.
The Dark Web is based on private networks and encryption protocols that provide a high level of anonymity. These areas can be accessed through networks such as Tor (The Onion Router) and I2P (Invisible Internet Project). Shopping on these platforms is usually done in cryptocurrencies and is difficult to trace.
For a Cybersecurity professional to be effective in these murky waters, advanced tool knowledge and a firm moral compass are required. In addition, a detailed understanding of the field and a cautious approach are essential. Those operating in this dark world often have high technical capabilities and sophisticated defense mechanisms. Understanding and caution are vital for cybersecurity professionals in this arena.
Common Myths of the Deep Web
The Deep Web may only be seen as a hub of illegal activity, but this is only scratching the surface. In fact, much of the Deep Web is filled with legal and harmless content. Many useful services are available on the Deep Web, such as academic databases, specialized corporate pages, and forums to protect user privacy.
In general terms, it is misleading to equate the Deep Web with illegal activities. In reality, due to the technological infrastructure and anonymity of these networks, they are also preferred by groups such as civil society organizations, journalists and activists. The Deep Web is an important refuge for those seeking freedom and privacy on the Internet, even though it harbors some dangers.
Misperceptions and Realities
The Deep Web is often misconceived as a focus for illegal trade, but this perception is highly incomplete. In fact, the Deep Web hosts a lot of legal content that is not normally accessible.
Contrary to popular belief, the majority of the Deep Web does not consist of illegal activity. Large and diverse parts of the Internet are just below the surface.
While many people think that the Deep Web is only used for criminal activities, it has also become an indispensable resource for researchers, journalists and activists who respect privacy rights, as it enables the sharing and communication of confidential information.
While the existence of dangerous and illegal spaces is undeniable, it is not correct to assume that this face of the Deep Web reflects the entire network. The reality is that the Deep Web is also the home of legitimate services that enhance global information access and protect individual privacy, and labeling it as “dark” ignores its many facets and benefits.
Deep Web Culture and Its Reflections in the Media
The cultural impact of the Deep Web is huge.
Due to its dark and mysterious nature, the Deep Web is often represented in the media with a negative image. In fictional works, it is often portrayed as a hub of criminal organizations, a stronghold of smuggling. However, the positive uses of this space are often overlooked or not covered in the media.
The Deep Web has been the main subject of some movies.
When it comes to freedom of information and privacy – which are among the positives of the Deep Web – very few TV series or movies deal with these issues in an objective way.
When real-life use cases are compared to media over-dramatized stories, the positive and important contributions of the Deep Web come to the surface, and the media’s tendency to over-demonize this space is a trend that is still ongoing as of 2024. This should be taken into account when looking at society at large, so that a realistic perception is formed and people can understand the multi-layered and diverse nature of the Deep Web.
Frequently Asked Questions About Deep Web
What is the Deep Web?
The Deep Web refers to a large part of the internet that cannot be found with standard search engines. Requiring special permissions or software, this layer offers anonymity and privacy and often hosts legitimate content such as private databases and archives.
What is the difference between Deep Web and Surface Web?
The Surface Web is the websites that we use daily and that are visible to search engines. The Deep Web is a larger part of the internet that is not indexed by search engines and requires special access methods.
How to access the Deep Web?
Accessing the Deep Web requires special browsers and software. The most well-known example is the Tor Browser. This browser allows users to remain anonymous on the internet and enables communication over an encrypted network.
What is found on the Deep Web?
The Deep Web hosts a wide range of useful and legitimate information, from legal content to academic databases, private forums and research materials. It also includes areas such as the Darknet, which is used for certain illegal activities.
Is the Deep Web safe?
While some areas of the Deep Web may be safe, areas such as the Darknet carry a high risk. It is important to take security precautions (e.g. use a VPN, apply strong encryption techniques) and browse responsibly.
What are the legal uses of the Deep Web?
The Deep Web is home to many legitimate resources such as scientific papers, specialized databases, government reports and library archives. It is also an ideal environment for legitimate business and research activities that require confidentiality.
What are the common misconceptions about the Deep Web?
The most common misconception is that the Deep Web is full of illegal activity. However, the Deep Web is full of largely legal and harmless content and, due to its technological infrastructure, is also used by researchers and activists.







