Currently Empty: $0.00

How important is the stability of your network structure and features such as mac address filtering?
In high traffic and complex network structures, loops that may occur during data exchange between network devices can lead to disasters. Spanning Tree Protocol (STP Protocol) stands out as a basic solution mechanism that prevents these problems.
STP is a network protocol that detects and prevents loops on the network, thus preventing data packets from getting stuck on repetitive paths. Thanks to this structural continuity, it acts as an anchor that guarantees the smooth operation of the network and a stable flow of communication.
What is the mechanism of the Protocol?
STP (Spanning Tree Protocol) Basics
The STP protocol is a protocol that prevents ring formation in Ethernet networks and provides network flexibility through the cabling structure. After discovering all connection paths in the network, it prevents data packet collisions and network errors. To do this, it determines active and backup paths.
The determination of these paths depends on parameters such as priority values and bridge IDs. The protocol operates at Layer 2 (Data Link Layer) and uses switches as bridges that direct data traffic within the network. It detects loops within the network and selects the most appropriate path.
The primary objective of STP is to optimize data packet circulation in the most efficient manner. This prevents redundancy and confusion across the network and ensures reliable communication between devices.
Definition and Purpose
Designed to shorten convergence time, STP (Spanning Tree Protocol) is a protocol that prevents loops from forming in Ethernet networks, ensuring that data transmission is carried out regularly.
Without STP, networks may be at risk of failure due to cyclic paths.
This protocol is designed to prevent unnecessary collisions of data packets and the network traffic from becoming chaotic. Functionally, it detects and prevents loops from forming on the network, allowing data packets to flow through the most appropriate routes.
Use of the STP Protocol is vital for all nodes on the network to communicate seamlessly; it maximizes efficiency in the system by increasing network performance and reliability. Thanks to these algorithms, complexity in network management is significantly reduced, while resistance to failures increases.
Historical Development and Standards
Spanning Tree Protocol (STP) was first invented in 1985 by Dr. Radia Perlman. This protocol was developed as a loop prevention method for bridging operations in Ethernet-based networks.
The original STP, published in 1985, has been adopted as the IEEE 802.1D standard. This standard has been continuously updated in line with developments in network technology.
In 1990, Rapid Spanning Tree Protocol (RSTP), an improved version of STP, was introduced with the IEEE 802.1w standard. RSTP has a much faster reconfiguration than the original STP.
Another important development was the Multiple Spanning Tree Protocol (MSTP), which supports multiple spanning tree structures. MSTP emerged in 2002 as the IEEE 802.1s standard.
Today, research continues on new protocols such as Enhanced Spanning Tree (ESTP) to enable more efficient management and faster convergence processes in complex network structures. Such innovations are important for networks to be able to adapt quickly to evolving requirements.
For more information on modern network management techniques and tools, please read our article titled “Examples of Kafka Use in Cybersecurity.”
Finally, considering the different implementations of STP, the development of cabling techniques, and the diversity of expanding network structures, new standards continue to be created to ensure that these protocols work in harmony and provide reliable network performance.
Basic Terms and Concepts
Spanning Tree Protocol (STP) is a protocol designed to prevent loops within a network and ensure the stable transmission of data packets.
- Bridge Protocol Data Unit (BPDU): Control messages used for communication between switches on the network.
- Root Bridge: The main switch with the lowest unique ID in the network that acts as a central point for data transmission.
- Designated Port: The port that represents the lowest-cost path in each network segment and transmits frames.
- Non-Designated Port: A port other than a designated port that is blocked by STP.
- Port Cost: This shows how much it costs to get to the root bridge for a link and is used in the path selection process.
- Port Priority: This value is used to determine the priority order of ports.
- Port State: Indicates the permeability of a port; for example, listening, learning, forwarding, or blocking.
- Topology Change Notification (TCN): A signal that sends information to other switches when there is a change in the network topology.
STP’s robust structure and dynamic adaptation capability stand out as a fundamental security element in large-scale network structures. The decision-making mechanisms and convergence process underlying the STP algorithm are designed to produce fast and effective responses to changes in the network topology. This is one of the factors that directly affect the continuity and efficiency of the network.
For more information about the basic elements of network security, please refer to our article, “What is Network Security: A Simple and Informative Guide.”
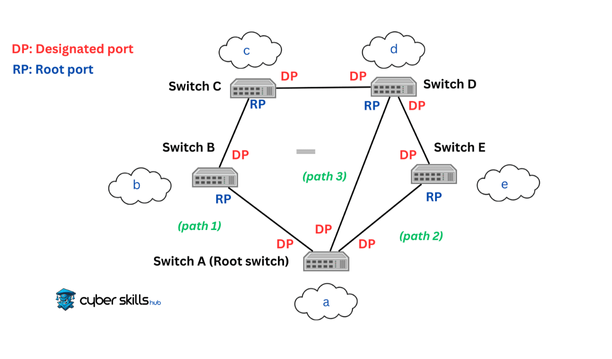
How the Spanning Tree Protocol Works
The Spanning Tree Protocol (STP) is designed to prevent potential loops in the network. All switches in the network automatically select a central switch called the “root bridge.” The root bridge is determined as the switch with the lowest ID number and forms the basis of the network. Each switch then determines the port that provides the shortest path to the root bridge, which is called the “root port.” Through comparisons between other ports, ‘designated ports’ are selected to represent each segment of the network. This established hierarchy ensures that data packets in the network reach the root bridge via the most efficient path, preventing potential loops and regulating network traffic. These processes and decisions are reflected in the continuous exchange of control messages called Bridge Protocol Data Units (BPDUs), enabling STP to quickly adapt to any changes or potential failures in the network and maintain a robust topology.
Detecting Topology Changes
STP detects changes in the topology.
When there is a change in the network topology, switches use BPDU (Bridge Protocol Data Units) packets to notify neighboring devices of this change. These packets contain information that reflects the current state of the network. They are sent at specific intervals and also enable switches to quickly communicate connection status to each other when there is a change in the topology.
These packages contain topology changes.
When topology changes are detected, the STP algorithm recalculates to determine the most appropriate routes. This ensures that data flows through the fastest and most efficient routes, maintaining network performance.
Perception is critical to reducing fluctuations.
This recalculation process reduces the likelihood of fluctuations and interruptions across the network. STP’s adaptability ensures that the network responds to constantly changing needs and remains reliable. For example, when a switch fails or a new device is added to the network, STP quickly analyzes the topology and makes the necessary adjustments.
New configurations enable network integration.
Detecting topology changes and enabling appropriate reconfiguration in response to these changes is critical to network continuity and stability. While providing this dynamism, STP also plays an important role in maximizing consistency and efficiency across the network. These aspects of STP require a deep understanding of network design and management on the part of network engineers.
Root Bridge Selection and Path Calculation
STP performs a root bridge selection process among all switches on the network. This selection is made based on the bridge priority value, and the bridge with the lowest value is designated as the root bridge.
Once the root bridge is determined, the other switches in the network calculate the most appropriate routes.
Other switches use BPDU (Bridge Protocol Data Unit) packets sent to determine the location of the root bridge.
These packets contain critical information about the network topology, including the identity of the root bridge and path costs.
The distance to the root bridge is the basic metric used to determine the most efficient paths, calculated based on path cost. Path cost is expressed as the sum of the costs of each network segment traversed.
Finally, each switch assigns roles to the ports it is connected to: root port, designated port, and blocked port. These roles are critical for preventing loops on the network.
Port States and Communication Blocks
Spanning Tree Protocol (STP) manages the state of ports to prevent false loops in the network. Each port plays a specific role in the operation of STP and takes different states.
The basic port states defined by STP are Disabled, Listening, Learning, Forwarding, and Blocking. The Disabled state means that the port is inactive and will not forward any network traffic. In the Listening and Learning states, the ports are not yet forwarding network traffic, but are gathering the information necessary to learn the topology of the network. These two states are necessary for the network to be stable.
Forwarding status refers to a situation where the port is ready to forward network traffic and enables data flow on the network. On the other hand, blocking status refers to a situation where the port blocks network traffic, thereby preventing loops from forming. This status is particularly important when there are multiple paths on the network and there is a potential for loops to form between these paths.
The success of STP depends on careful management of these port states. Switches communicate with other switches across the entire network via BPDU packets to determine which port should be in which state. This enables them to transition to port states that ensure the stable and loop-free operation of the network by establishing the necessary stable topology. In this context, the state of each connection point in the network is of critical importance to the overall health of the topology.
Types of Spanning Tree Protocols
The main goal of the Spanning Tree Protocol (STP) is to reduce the network to a single active topology and prevent loops. The first standard is known as IEEE 802.1D.
Developed in response to increasing network complexity, Rapid Spanning Tree Protocol (RSTP) offers improvements that enable faster convergence with the IEEE 802.1w standard. RSTP creates an active network topology faster than previous STP standards and prevents loops.
The IEEE 802.1s standard, known as Multiple Spanning Tree Protocol (MSTP), allows multiple spanning trees to be created on a single physical network, thereby enabling more efficient use of resources.
Comparison of STP, RSTP, and MSTP
STP (Spanning Tree Protocol), RSTP (Rapid Spanning Tree Protocol), and MSTP (Multiple Spanning Tree Protocol) are protocols designed to prevent bridge loops in networks, but they differ in terms of performance and flexibility.
- STP (IEEE 802.1D): This is the first protocol to emerge and provides reliable network operation by preventing loop formation. However, it has the disadvantage of responding slowly to changes in the network topology.
- RSTP (IEEE 802.1w): This is an improved version of STP and provides faster convergence, allowing it to adapt more quickly to changes in the network.
- MSTP (IEEE 802.1s): Supports multiple spanning trees, thereby reducing weak points and optimizing resource usage by creating multiple logical network topologies on a single physical network. RSTP offers a faster convergence time compared to STP, which is crucial for network stability and rapid recovery capabilities. MSTP builds on the advantages offered by RSTP, particularly in large and complex network structures, providing more effective load balancing and resource utilization. This provides network administrators with superior control mechanisms in terms of flexibility and scalability.
Enhanced Protocols and Innovations
In addition to the protocols mentioned above, there are many versions and improvements developed for the Spanning Tree Protocol (STP). These innovations are designed to increase the effectiveness of the protocol and adapt it to modern network requirements.
Accelerated STP modifications such as IEEE 802.1t and IEEE 802.1w improve the protocol’s response time. The ability to adapt quickly to dynamic changes in network topology is one of the most important contributions of these modifications.
As network topologies become more complex, protocols such as Rapid Spanning Tree Protocol (RSTP) and Multiple Spanning Tree Protocol (MSTP), which are enhanced versions of STP, come into play. These protocols significantly improve both the reliability and performance of the network with more efficient convergence times and high fault tolerance.
In addition, innovative protocols such as Shortest Path Bridging (SPB), known as IEEE 802.1aq, aim to address the shortcomings of STP. SPB stands out for its ability to optimize data flow by utilizing all paths in the network and creating a loop-free topology. These advanced techniques offer more flexible, scalable, and manageable solutions for existing data centers and complex network structures. These developments are evidence of experts’ ongoing quest to achieve “better” or “perfect” convergence.
Spanning Tree Protocol Configuration and Troubleshooting
The Spanning Tree Protocol (STP) is designed to ensure stable operation by preventing looped connections in the network. Correct configuration of STP is critical for network stability. At this stage, you must first ensure that STP is enabled and that network devices are configured with the correct parameters.
Configuration parameters such as priority values (Bridge Priority) and port costs (Path Cost) between interactive network elements are important during the STP process. Understanding the overall structure and traffic of the network is essential for optimizing these parameters. Bridges with low priority values are selected as root bridges, and network traffic is routed through these bridges; this selection directly affects root bridge placement and STP’s reconvergence time in response to topology changes.
When troubleshooting, problems experienced with protocols such as STP, which often cause interruptions and slowdowns in the network, are identified and analyzed in detail. During the STP troubleshooting process, in addition to physical and configuration errors in the network, it is also necessary to check whether bridged packets and topping messages are being received correctly.
Configuration Steps and Recommendations
During STP configuration, it is critical to determine the priority values for root bridge selection. These values should be kept low to ensure that a reliable device is assigned as the root bridge at the center of the network. Assigning the wrong root bridge can negatively impact network performance.
Enabling the PortFast feature on all ports helps prevent slow connections. However, it should be used with caution as it can increase the risk of loops.
Path cost values should be determined intelligently based on the traffic of the existing network, and manual adjustments should be made when necessary. Dynamic adjustments are important in order to respond quickly to sudden traffic changes.
Enabling security mechanisms such as BPDU Guard and Root Guard during network topology changes can prevent unwanted changes. These protection mechanisms increase security against unauthorized bridge additions or malicious attacks.
The STP version (e.g., RSTP or MSTP) selection should be appropriate for topology change response times and network capacity. The appropriate version should be selected considering network scalability and changing needs.
Periodic network audits should be conducted to test and verify the correct configuration of STP. Change management and audit logging practices are important for quickly identifying and correcting potential errors.
Common Problems and Solutions
Problems encountered in Spanning Tree Protocol (STP) applications are usually caused by incorrect configuration or hardware errors.
- Incorrect Root Bridge Selection: Selecting an unexpected device as the root bridge on the network causes poor performance. To correct this situation, you can manually specify the root bridge or ensure that the bridge priority values are assigned correctly.
- Duplex Mismatches: Inconsistencies between half-duplex and full-duplex settings between devices can cause data collisions. Reviewing the duplex settings of all devices and making them compatible will resolve the issue.
- Convergence Times on Backup Paths: In STP, the time it takes for backup paths to become active can be long. These delays can be minimized by using protocols with faster convergence times, such as RSTP (Rapid Spanning Tree Protocol). Network outages following topology changes may occur as a result of the STP configuration not being updated correctly. When resolving STP-related issues, it is critical to ensure that network devices have the latest firmware versions and to perform regular network audits. This will enable early detection and intervention of issues.
In this blog post titled “What is STP (Spanning Tree Protocol) and How Does It Work?”, we explained the basic working principles and advantages of STP. However, for readers interested in more technical details and specifics, we recommend checking out Cisco’s Spanning Tree Protocols (STP, MST) article.
Frequently Asked Questions About STP
What does STP mean?
STP stands for Spanning Tree Protocol. This protocol is used to prevent loops in the network and ensure data transmission in Ethernet-based networks. STP works to prevent loops from forming in networks that use multiple switches. Loops in a network can cause network traffic to circulate endlessly within the loop, rendering the network inoperable. STP detects and prevents these loops.
What is STP and what does it do?
STP (Spanning Tree Protocol) is a protocol used to prevent loops in networks and regulate network traffic. Developed by IEEE in 2016, STP prevents loops in Ethernet networks and manages network traffic by selecting between multiple active paths. This makes data communication in the network more efficient and improves network performance. The primary purpose of STP is to prevent loops from forming between multiple paths in the network. If a loop occurs, a packet can circulate endlessly in the network, intensifying network traffic and reducing network performance. STP detects these loops, closes unnecessary paths, and activates backup paths to eliminate imbalances in the network. The working principle of STP is to select the best path among the switches in the network. To do this, it uses BPDU (Bridge Protocol Data Units) messages and communicates with the switches in the network to exchange information about the topology.
What is the purpose of STP?
STP (Spanning Tree Protocol) is a routing protocol used to prevent loops in networks. It is used in Ethernet networks to control connections between network devices and prevent loops from forming on the network. The primary purpose of STP is to prevent traffic chaos caused by loops in the network. It monitors the connections between bridges and switches in the network and temporarily disables certain connections when necessary. This ensures that data packets are transmitted properly and efficient communication is maintained across the network.
How is STP done?
STP (Spanning Tree Protocol) is a network protocol used to prevent loops from forming in Ethernet networks. STP ensures network stability by enabling all switches in the network to communicate with each other. STP is based on the communication between bridge devices in the network. Each bridge exchanges information with other bridges in the network to determine the topology. This allows STP to eliminate loops by selecting the shortest path in networks with multiple paths.







