Currently Empty: $0.00
What is SSL Pinning and How Does It Work?

Today, internet security has become more important than ever. SSL stands out as a prominent technique in digital certificates and data encryption. This method is used to increase network security, especially in Android applications and other mobile platforms. SSL plays an important role in protecting sensitive information by strengthening the reliability of the Transport Layer Security (TLS) protocol.
In this article, we will take an in-depth look at what SSL pinning is and how it works. We will also discuss the advantages and possible disadvantages of this technique. We will also evaluate the role of certificate authorities and the contribution of SSL pinning to application security. Finally, we will look at the potential future uses of this technology.
What is SSL Pinning?
SSL pinning is an important technique used to enhance security in applications and websites. This method is used to authenticate client-server connections, especially in the context of secure communication over HTTPS.
Definition of SSL Pinning
It is a security mechanism that enables an application or website to trust only predetermined and trusted certificates or public keys. This method takes trust verification one step further by reducing reliance on certificate authorities (CAs).
Purpose of SSL Pinning
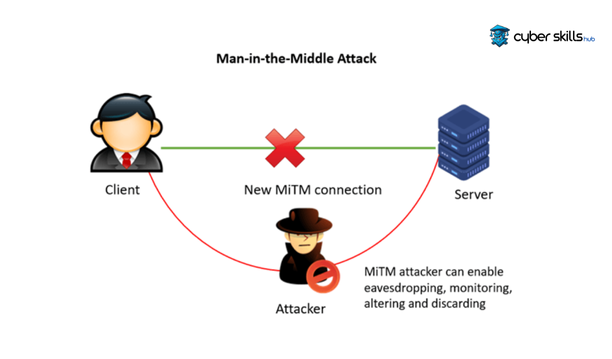
Its main purpose is to prevent man-in-the-middle (MITM) attacks and improve data security. This technique helps to prevent sensitive data of applications or websites from falling into the hands of others. Especially in mobile applications, it is used to ensure secure communication with the server.
SSL Pinning Types
There are two main methods:
- Certificate Pinning: In this method, certain byte codes of the SSL certificate are added to the application code. The application checks these codes when it establishes a connection with the server. If the codes do not match, an SSL certificate error occurs.
- Public Key Pinning: In this method, the public key of the server is pinned to the client. The client verifies the security of the connection by using this key each time it connects to the server.
| SSL Pinning Method | Description |
|---|---|
| Certificate Stabilisation | Byte codes of the SSL certificate are added to the application |
| Joint Key Fixing | The server’s public key is pinned to the client |
Although it provides significant advantages in terms of security, it also brings some challenges. For example, certificates or keys need to be updated regularly. It can also cause implementation difficulties in dynamic and cloud-based environments. However, SSL pinning significantly increases the security of applications and websites by creating a strong line of defence against cyber attacks.
How Does SSL Pinning Work?
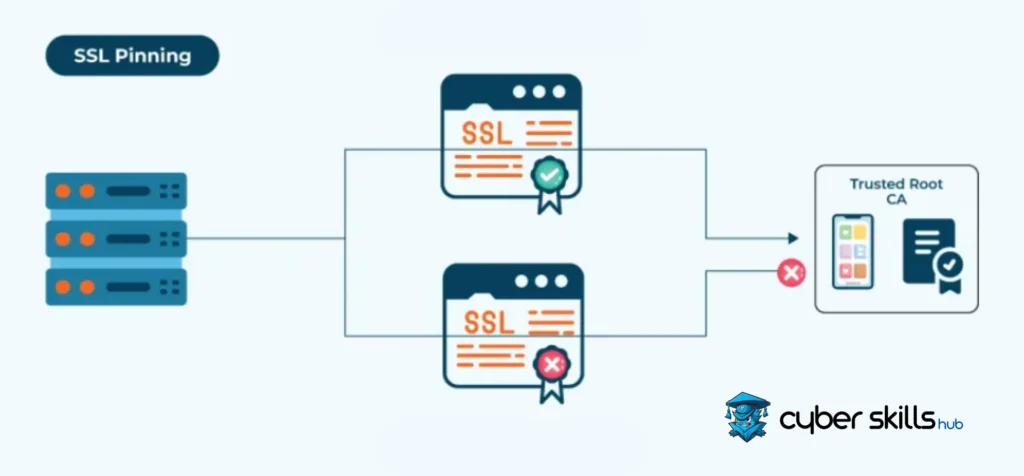
SSL is a security process that associates a device with an X509 certificate or public key. This allows applications to trust only a recognised or valid certificate. Here are the details of how SSL pinning works:
Certificate Validation Process
SSL pinning takes the standard certificate validation process one step further. In a typical TLS handshake, the server presents its digital certificate to the client. The client checks that this certificate is signed by a trusted Certificate Authority (CA), has not expired, and has not been revoked. SSL further strengthens this trust verification.
The client application or device has a preconfigured list of public keys or certificates. This list contains certificates that the application can trust. When establishing a connection, the certificate offered by the server is compared against this list. If a match is made, the connection is trusted and continued. Otherwise, the connection is rejected.
Secure Connection Setup
Setting up a secure connection with SSL includes the following steps:
- The application attempts to connect to the server.
- The server sends the SSL certificate to the application.
- The application compares the received certificate with predetermined trusted certificates.
- If the certificate matches, a secure connection is established. If it does not match, the connection is rejected and an SSL certificate error occurs.
Technical Details of SSL Pinning
Different methods can be used to implement SSL:
- Certificate Pinning: Specific byte codes of the SSL certificate are added to the application code. This method validates the entire certificate.
- Public Key Pinning: The server’s public key is pinned to the client. This method is more flexible and does not require updates in case of certificate changes.
- Hash Stabilisation: The hash of the public key of the server certificate is kept. It is compared with the hash of the certificate received during connection.
| SSL Pinning Method | Advantage | Disadvantage |
|---|---|---|
| Certificate Stabilisation | High security | Requires frequent updates |
| Joint Key Fixing | Flexible, low update | Increases application size |
| Hash Stabilisation | Compact, safe | Complex application |
SSL pinning is an effective method to increase security in mobile applications and websites. However, it should be noted that the application should be updated regularly and certificate changes should be followed.
Conclusion
SSL stands out as an important step in the field of secure communication and data protection. This technique has a great impact on increasing the security of applications and websites. Especially on mobile platforms and Android applications, the use of SSL creates a strong line of defence against cyber attacks.
In conclusion, while the implementation of SSL pinning offers significant advantages in terms of security, it also brings some challenges. Certificates and keys need to be updated regularly, which requires additional effort. Nevertheless, SSL pinning is becoming an indispensable tool in today’s digital world to protect sensitive data and ensure secure communication.
Frequently Asked Questions About SSL Pinning
What is SSL Stabilisation?
SSL Hardening is a security method commonly used in mobile and other client applications. This method is used to verify the authenticity of the SSL certificates that the application uses when communicating with the server.
How can you tell if a web application is secure?
If the URL of the web application starts with HTTPS instead of HTTP, it indicates that the application is secured with an SSL certificate. Secure sites have a closed padlock icon and you can access security details about the site by clicking on this icon. The most secure sites have a green padlock icon in the address bar.
What kind of problems can occur without an SSL certificate?
User information can be compromised on sites without SSL certificates, especially when sensitive data such as credit card information or personal information is transferred. In addition, modern web browsers notify users entering sites without SSL certificates with a security warning.







