Currently Empty: $0.00
What is Reaver? User Guide for Wi-Fi Hacking

The security of Wi-Fi networks has become a very important issue today. At this point, tools such as Reaver are of interest to both security experts and malicious people. Reaver is a software designed to crack wireless network passwords by exploiting weaknesses in the Wi-Fi Protected Setup (WPS) protocol. This tool can be used to test network security and identify weak points.
In this article, we will cover in detail what Reaver is and how it works. Furthermore, we will go through the installation steps and the Wi-Fi password cracking steps step by step. Finally, we will discuss the legal warnings and ethical issues related to the use of this tool. Understanding Reaver is an important step in improving network security and taking precautions against potential threats.
What is Reaver and how does it work?
Reaver is a powerful tool used to test the security of Wi-Fi networks and identify weak points. This software is designed to crack wireless network passwords using weaknesses in the Wi-Fi Protected Setup (WPS) protocol. Reaver is of interest to both security experts and malicious actors. If you want to learn more about cyber security vulnerabilities, we recommend that you review our cyber security tutorials.
Key Features of Reaver
Reaver attacks WPS-enabled routers to crack the WPS PIN and then obtain the real WPA key. This tool performs a brute-force attack against an 8-digit PIN. It attempts a total of 10^4 + 10^3 possibilities. Reaver does not require monitor mode to work, so it can also be used on Android devices.
One of the most remarkable features of Reaver is that it is fast and effective. Users can crack WPA/WPA2 passwords using this tool. The cracking process may vary depending on luck. In some cases, the password can be obtained within a minute, while this can take up to 8-9 hours at most.
WPS Protocol and Security Vulnerabilities
Wi-Fi Protected Setup (WPS) is a protocol designed to simplify wireless network setup. However, this protocol contains serious security vulnerabilities. Because many router manufacturers and Internet Service Providers (ISPs) leave WPS turned on by default, many routers are vulnerable to these attacks directly out of the box.
Reaver works by exploiting these weaknesses in the WPS protocol. In particular, it breaks the WPA/WPA2 password by performing brute-force attacks against WPS registrar PINs. Therefore, it is recommended to switch off the WPS feature to increase network security.
The use of Reaver can be an important tool for testing network security and identifying weak points. However, misuse of this tool can lead to legal and ethical issues. Therefore, it is important to stay within legal and ethical boundaries when using Reaver.

Reaver Setup and Preparation
Required Hardware and Software
To use Reaver, certain hardware and software are required. Firstly, a computer with a wireless network card is required. This network card must support monitor mode. On the software side, it is important to download the latest version of Reaver. You can use the following command to do this:
git clone https://github.com/t6x/reaver-wps-fork-t6xThis command will download an updated fork of Reaver. After the installation is complete, you will be ready to use Reaver.
Putting the Wireless Network Card into Monitoring Mode
To use Reaver effectively, it is necessary to switch the wireless network card to monitor mode. There are two different ways to do this:
- Configuration with Airmon-ng:
- First, terminate the conflicting processes by running the ‘airmon-ng check kill’ command.
- Next, put the network card into monitor mode using the ‘airmon-ng start wlan0’ command.
- When the process is complete, check the mode of the network card with the ‘iwconfig’ command.
- Configuration with ifconfig:
- Set the network card to monitor mode by running the ‘iwconfig wlan0 mode monitor’ command.
- Activate the network card with the ‘ifconfig wlan0 up’ command.
In both methods, verify that the network card is in monitor mode with the ‘iwconfig’ command.
To put the network card back into normal mode:
- If airmon-ng is used: Use the command ‘airmon-ng stop wlan0mon’.
- If ifconfig was used: Disable the network card with the command ‘ifconfig wlan0 down’.
After completing these steps, you will be ready to use Reaver. An example Reaver command is as follows:
reaver -i wlan0mon -b E0:3F:49:6A:57:78 -vv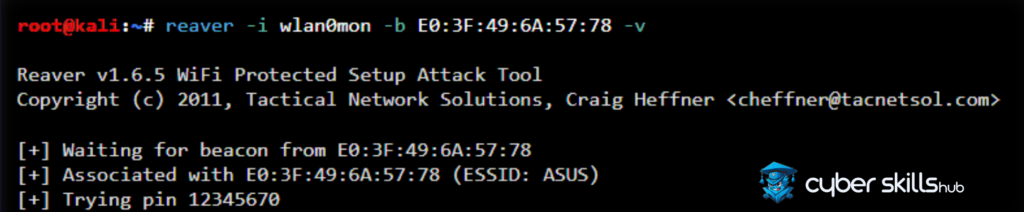
In this command, the ‘-i’ parameter specifies the network interface in monitor mode, the ‘-b’ parameter specifies the MAC address of the target network, and ‘-vv’ specifies the detailed output.
When using Reaver, it is important to stay within legal and ethical boundaries. Use this tool only in your own networks or networks for which you have permission.
Steps to Crack Wi-Fi Password with Reaver
Reaver is an effective tool for cracking WPA/WPA2 passwords using weaknesses in the Wi-Fi Protected Setup (WPS) protocol. In this section, we will discuss in detail the steps to crack Wi-Fi passwords using Reaver.
Target Network Identification
Before you start using Reaver, it is important to identify the target network. This step requires putting the wireless network card in monitor mode to scan the surrounding WPS-enabled networks. The following points should be considered when determining the target network:
- The signal strength of the network should be at least 85%. High signal strength increases the chances of success.
- Make sure that the WPS feature of the target network is switched on.
- It may be easier to work on older models, because WPS attacks on new modems are usually not effective.
Initiating a PIN Code Attack
Once the target network is identified, a PIN code attack can be initiated with Reaver. The following steps are followed for this process:
- Open Terminal and enter the Reaver command. An example command is as follows:
reaver -i wlan0mon -c 1 -b 14:5F:94:48:F7:04 -vv -L -N -d 15 -T .5 -r 3:15 - The meaning of the parameters in this command is as follows:
- -i: Network interface to use
- -c: Channel number of the destination network
- -b: MAC address of the destination network
- -vv: For detailed output
- -L: To ignore lock states
- -N: To block NACK messages
- -d: Test interval (in seconds)
- -T: M5/M7 timeout time
- -r: Waiting time after a specific PIN attempt
- When the command is executed, Reaver will automatically attempt to crack the WPS PIN.
Monitoring the Password Cracking Process
When the reaver is running, it is important to monitor the progress of the process. The following points should be considered at this stage:
- Follow the output that appears on the terminal screen. It will provide information about successful attempts and remaining PIN combinations.
- Keep the computer stationary and do not move it during the operation. This is important to maintain signal quality.
- In some cases, the process can be completed in a few minutes, but sometimes it can take hours.
- When the password is successfully cracked, Reaver will display the WPA/WPA2 password on the screen.
- Remember to make a note of the resulting password and the relevant network information (modem ID, name, PIN used).
By following these steps, it is possible to crack the passwords of Wi-Fi networks with WPS support with the Reaver tool. However, keep in mind that this process should only be performed on your own network or on networks for which you have permission. Unauthorised access can lead to legal consequences.
Conclusion and Legal Notices
Reaver is a powerful tool for testing the security of Wi-Fi networks and identifying weak points. This software is designed to crack wireless network passwords using weaknesses in the WPS protocol, attracting the attention of both security experts and malicious people. The use of Reaver is seen as an important step to increase network security and take precautions against potential threats.
In conclusion, understanding and properly using Reaver is of great importance for network security. However, the use of this tool should remain within legal and ethical boundaries. Reaver should only be used on personal networks or networks with permission. In this way, it will be possible to use Reaver as an effective tool to strengthen network security.
Frequently Asked Questions About Reaver
Is the use of Reaver legal?
Reaver is legal when used to test network security, but gaining access to unauthorised networks is illegal and can lead to serious legal consequences.







