Currently Empty: $0.00
What is Phishing? How to Protect Yourself?

Phishing attacks affect millions of people and organisations every year, causing huge financial losses. Cybercriminals use clever tactics over the Internet to steal identity and financial information.
This threat is one of the biggest problems in the digital world.
Nevertheless, with informed users and appropriate protection measures, a strong defence against these attacks can be built.
What is Phishing?
Phishing is a common type of cybercrime.
These attacks usually take place via email, social media or fake websites. The aim is to trick users in order to obtain their personal and financial information. Attackers trap their victims by creating messages or web pages that appear to be real. This technique can be quite effective, especially if you are not careful.
Users can share their information without realising it.
Phishing attacks can also be done by redirecting users to a fake website. Because these sites mimic real sites so well, users often cannot tell the difference.
This method used by cyber criminals poses a significant threat in the digital world. However, thanks to conscious users and advances in security technologies, effective solutions are being developed against such attacks. Modern security systems and awareness-raising trainings make users more resistant to phishing attacks.
Types of Phishing
There are different types of phishing attacks, each with different targets and methods. The main ones include spear phishing, whaling and vishing.
Spear phishing targets a specific person or organisation and usually includes personalised content. Whaling targets high-profile executives, while vishing is phishing attacks made by phone.
These kinds of can lead to users becoming victims if they are not careful.
Email Phishing
Email phishing involves sending fake emails with the intent to steal users’ personal information. These fake emails often appear to be from a trusted organisation and are designed to trick the recipient.
The emails encourage users to click on a link or share sensitive information. If the link is clicked, the user is redirected to a malicious site and their information is collected.
Today, millions of e-mail phishing attacks occur every day.
To protect yourself, you should be careful, do not open e-mails from unknown senders and do not click on suspicious links. In addition, additional security measures such as two-factor authentication should be used and security software should be kept up to date. These measures can greatly reduce the risk of phishing attacks.
Spear Phishing
Spear phishing are targeted and more personalised phishing attacks. Such attacks target specific individuals or organisations and often contain detailed information.
Attackers design their messages to reach the recipient by creating credibility with the information they collect from their targets’ social media accounts or the internet. Therefore, spear phishing attacks are more dangerous than ordinary phishing attacks.
In spear phishing attacks, attackers often create credibility by posing as messages from the target’s colleagues, managers or acquaintances. These messages encourage them to share sensitive information or download malware.
To protect against such attacks, it is crucial that users are especially wary of personalised messages and regularly review their information. In addition, in-house training and security protocols can raise awareness of spear phishing attacks.
As a result, spear phishing attacks can be more sophisticated and dangerous. Careful and conscious should be taken.
SMiShing (SMS Phishing)
SMiShing is an attempted fraud through SMS messages sent to users’ mobile phones.
- Fake notifications about sharing bank or credit card details
- Fake prizes or sweepstakes
- Password renewal or account activation requests
- Links hosting malware
The purpose of such SMS is to induce users to disclose their personal information or financial data.
Against SMiShing attacks, SMS from unknown numbers should be paid attention to and the specified links should not be clicked.
Vishing (Telephone Phishing)
Vishing is a type of phishing in which fraudsters attempt to obtain personal information through telephone calls.
- Persons presenting themselves as employees of an official organisation or company
- Those who request information by presenting urgent or frightening scenarios
- Calls requesting private information for authentication purposes
- Requests for credit card or bank details
In such attacks, fraudsters often use realistic and persuasive language.
It is very important not to share personal information without verifying who the incoming calls are from.
In order not to fall into these traps, care should be taken and suspicious calls should be reported to the relevant institutions.
How Do Phishing Attacks Work?
Phishing attacks are malicious acts designed to obtain personal information through fraud and deception. Attackers trick victims into disclosing their information.
These attacks are usually very convincing and professional looking.
Attackers attempt to steal usernames, passwords or credit card details of target individuals by sending fake emails, websites or social media messages. These messages often use the logo and language of a real organisation.
Nevertheless, careful and informed users can recognise these pitfalls. For example, if an unexpected email asks for an urgent action or requests personal information, it is important to be sceptical and verify the identity of the sender. With this careful approach, it is possible to avoid phishing attacks.
Symptoms of Phishing Attacks
Recognising the signs of phishing attacks keeps users safe and helps protect them from potential threats.
Firstly, one of the most common symptoms of a phishing attack is an emphasis on urgency. Attackers use fear or panic to force their victims to act quickly. For example, they may send fake warnings that your bank account will be frozen or that your credit card details have been compromised.
Another symptom is requests for personal information. Government organisations usually never request your username, password or personal information via email or text message. Such requests are usually signs of a phishing attempt.
In addition, language errors and strange URLs in emails or messages are also noteworthy. Phishing messages are often created in a hurry and may contain grammar and spelling errors. It is also important to check the URL before clicking on links, as attackers often use fake sites that look similar to real sites but with slight differences. This level of awareness is critical to protecting against phishing attacks.

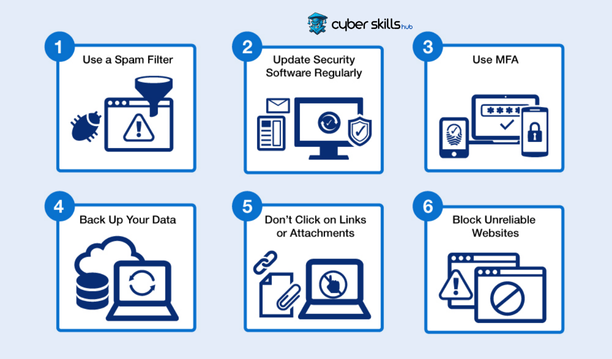
Protection Methods from Phishing Attacks
To protect against phishing attacks, users should adopt various security measures and make these measures part of their daily habits. Being aware, carefully examining any suspicious emails or messages, using authentication tools and keeping security software up-to-date are some of the most effective defences against such attacks. Participating in educational programmes and courses can also increase the awareness of individuals and employees about cyber security, so that collective protection can be achieved.
Using Security Software
One of the most effective ways to protect against phishing attacks is to use security software. Today, many security software are equipped with advanced threat detection algorithms.
This software makes users’ internet browsing safer and can detect potential phishing attacks early on. Antivirus programmes and firewalls are among the most widely used.
It is very important that security software is constantly updated. Software providers regularly release software patches and updates against new threats. These updates help protect users against the latest threats.
At the same time, phishing filters are also an important security measure offered by email providers and browsers. Email filters keep users’ inboxes clean by weeding out potentially dangerous emails.
By using security software effectively, users can protect themselves from phishing attacks to a great extent.
Set up Email Filters
Email filters are of great importance.
When the correct settings are made, these filters block fake e-mails. It ensures that only secure emails reach users’ inbox. To increase security, you can make adjustments using the filtering options offered by your email provider. Thus, your chances of protection from phishing attacks increase.
The filter settings should be checked regularly.
You can set up filters based on specific keywords or senders – so that only emails from trusted sources remain. It is also useful to activate the anti-spam and anti-phishing features of your e-mail provider.
You can get help from your email provider’s support department or online guides. As of 2024, many providers are updating and improving their filtering technologies to maximise the security of their users. By following these steps, you can ensure that only trusted communications are included in your e-mail box and prevent phishing attacks.
Avoiding Suspicious Links
It is important to avoid suspicious connections.
Always verify the source sharing the link. Confirming the identity of the sender and the authenticity of the link before clicking on the links in incoming e-mails or messages is one of the first steps to protect against phishing attacks. In addition, checking the URL and questioning its reliability increases the security of the user.
Browser extensions can help.
These extensions automatically analyse and warn you whether the websites you visit are safe or not. Especially if you frequently shop online, such security tools can be of great benefit.
If your goal is to stay safe, it is essential to be aware and careful. Avoiding suspicious links is an effective measure to avoid falling prey to phishing attacks. In addition, being careful when using social media and messaging applications plays an important role in protecting against such attacks. Always opening links from trusted sources increases your security.
Conscious Internet Use
Conscious internet use is of great importance.
Everyone surfing the internet needs to be careful and conscious. This can help protect against cyber attacks such as phishing. Conscious internet use includes not only visiting trusted websites, but also creating strong passwords and following regular updates. Individuals should take the necessary precautions to protect themselves and their information.
Your safety is in your hands.
In particular, you should treat messages from unfamiliar sources with great care. Always be careful when sharing personal information and use additional security measures such as two-factor authentication. This will further strengthen your security.
Today, with the widespread use of the internet, education also plays a major role. It is possible to use the internet more securely with seminars and trainings that raise awareness about cyber security. Such trainings will continue to increase in 2024. By constantly improving yourself, you can be more prepared for possible future attacks. You can become more conscious by learning about the Role of Social Media Intelligence (SOCMINT).
Phishing Cases and Examples
Phishing is a type of attack that aims to deceive users to obtain their personal information. In recent years, many large companies have also been the target of such attacks.
For example, in 2020, the giant phishing attack on Twitter caused great repercussions.
Attackers committed Bitcoin fraud by hacking the accounts of famous people.
In another example, the email addresses of Dropbox users were compromised by cyber attackers in 2016.
Phishing attacks with fake e-mails against Gmail users have caused many users’ Google account information to be stolen.
These examples show how dangerous phishing attacks can be; careful and informed use of the Internet is the strongest defence against such attacks.
What Should You Do When You Are Under Phishing Attack?
When you are attacked by phishing, it is most important not to panic and take quick steps.
Firstly, if you realise that you have been hacked, you should immediately check your relevant accounts and change your passwords. If you have been attacked with banking information, you should immediately contact your bank and report the situation. These steps will be your first line of defence against the attacker.
However, to minimise potential damage, you should conduct a flexible and rigorous assessment process to determine the extent of the attack. If you work in a corporate environment, you should immediately notify your IT department and report the incident. This is a vital step for organisation-wide action.
Finally, you should not neglect to get professional support after the attack. With the help of an expert cyber security team, you can re-secure your system and make it more resistant to future threats. In this process, it is also of great importance to receive training on ways to protect against such attacks. Trainings will increase your awareness and make you more prepared for possible future attacks.
Frequently Asked Questions About Phishing
What does Phishing mean?
Phishing is one of the cyber attacks to steal sensitive information of internet users. It is usually carried out via e-mail, fake websites and messages. Attackers trick their victims into sharing personal information. This information includes credit card numbers, passwords and credentials.
What is a Phishing penalty?
In the Turkish Criminal Code, phishing attacks are classified as serious offences. Such offences are subject to serious penalties due to the misuse of information and technology. Although the punishment may vary depending on the details of the offence, there are usually heavy prison sentences and high fines. If the offence is proven in judicial processes, criminals can be sentenced to imprisonment from 3 to 7 years according to the Turkish Penal Code. In addition, if the offence is committed through information systems, the penalty may be increased.
Phishing or Fishing?
Although the terms phishing and fishing seem very similar, they actually have completely different meanings. Phishing is one of the online fraud methods. It is used to capture personal information of individuals. It is a type of cyber-attack, especially via e-mail, social media and even phone calls. Fishing, on the other hand, means fish catching activity and is directly related to nature.
How does a phishing attack work?
Phishing attacks are organised by cyber criminals using various methods. Attackers use fake emails, messages or websites to capture their victims’ information. Users can be fooled by these communication tools that appear to be reliable, but are actually crafted with malicious intent. The danger begins when a victim clicks on a link in a fake email they receive. These fake links usually ask the user to enter personal information, passwords or credit card details.
Additional Resources
You can visit the following resources to learn more about phishing attacks and get detailed information about protection methods:
It is of great importance to be conscious and take the necessary precautions to protect against phishing attacks. Remember, cyber security is everyone’s responsibility.







