Currently Empty: $0.00
What is NTLM? Authentication Protocol Description

In the world of Internet security, authentication protocols are of great importance. The question of what is NTLM is frequently encountered in this field. New Technology LAN Manager is an authentication protocol developed by Microsoft and widely used in Windows networks. This protocol allows users and computers to securely authenticate themselves on the network.
In this paper, its basic features and working principles will be discussed. Furthermore, its relationship with encryption algorithms such as DES and AES will be analysed and compared with other authentication protocols such as Kerberos. Finally, the vulnerabilities of the NTLM authentication process and the measures that can be taken against them will be discussed. This information will help to gain a more comprehensive understanding of network security.
What is NTLM?
Definition
New Technology LAN Manager is an authentication protocol developed by Microsoft. This protocol is widely used in Windows-based operating systems and is designed to authenticate users and computers in network environments. NTLM is used for authentication in domain environments and works with the challenge-response method.
History
NTLM originated as a more secure version of an earlier authentication protocol, the LM (LAN Manager) protocol. It was first developed under the name NT (New Technology) and later merged with LM to become NTLM. Different versions of New Technology LAN Manager have been developed over time:
- NT: Initially developed version.
- LM: Developed for use with NT and for retrofitting.
- NTLMv1: It was developed due to the inadequacy of NTLM and is more secure.
- NTLMv2: It is the version of NTLMv1 with stronger hash values and is considered the most powerful version of NTLM.
Purpose of NTLM
The main purpose of New Technology LAN Manager is to provide secure authentication on Windows networks. This protocol is used to authenticate credentials such as username and password. It is still widely used, especially in cases where the domain controller is inaccessible or a client does not support the Kerberos protocol.
New Technology LAN Manager uses a three-step method to encrypt user passwords:
- The user is authenticated and a ticket request is generated.
- The ticket request is sent to the server, which authenticates the user and generates a session key.
- The server encrypts the user’s password using the session key and sends it to the user.
It offers a more secure authentication method than the LM protocol. However, it is still considered insufficient in terms of security because it does not use modern cryptographic methods. Therefore, Microsoft now recommends the Kerberos protocol instead of NTLM.
How Does NTLM Work?
Questioning-Response Mechanism
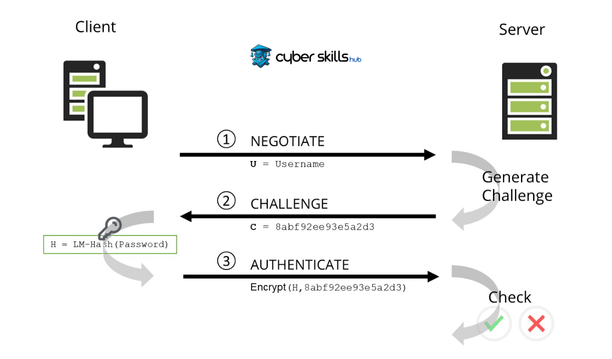
It uses the challenge-response protocol to perform authentication of network users. This process involves a series of steps between the client and the host. First, the client sends a username to the host. The host responds with a random number (challenge). The client generates a hash value using this number and the user’s password and sends it back in response. The host, knowing the user’s password, performs the same operation and compares the results. If the values match, the client is authenticated and granted network access.
Encryption Process
In the authentication process, the security of the user password is of great importance. During authentication, the client uses the MD4 hash of his password as the DES key to encrypt the query. A plaintext password is never used in this process. The encryption process includes the following steps:
- MD4 summarisation of the user password
- Adding 5 ‘0’ to the obtained 16 byte value and completing it to 21 bytes
- Separation of this value into 3 parts of 7 bytes each
- Using these 3 values as DES key and summarising the number of challenges
- Combining the resulting 8 byte values to obtain a 24 byte response value
Authentication Steps
The authentication process includes the following steps:
- The client wants to establish a connection by sending its username in the open state to the server.
- The server sends a 16 byte random number (challenge or nonce) to the client.
- The client responds to the server by summarising this number with its private key (the digest of its password).
- The server requests authentication by sending the user name, the encrypted number, and the original version of the number to the domain controller.
- The domain controller summarises the number using the client’s private key and compares the result.
- The result is sent to the server and the server notifies the client of the response.
The result is sent to the server and the server sends the response to the client. This process allows New Technology LAN Manager to be used both as a storage (in the SAM file) and as a communication protocol. New Technology LAN Manager, as an authentication protocol used in Windows NT and later versions, offers a more secure method than the LM protocol. However, it is still considered weak by modern security standards and Microsoft now recommends the Kerberos protocol.

Vulnerabilities of NTLM
Although the New Technology LAN Manager authentication protocol is widely used in Windows networks, it has several security vulnerabilities. These vulnerabilities allow attackers to gain unauthorised access to systems and capture sensitive information. The most important vulnerabilities include Brute Force attacks, Pass-the-Hash attacks, and Relay attacks.
Brute Force Attacks
Brute Force attacks are one of the weak points of the New Technology LAN Manager protocol. In this type of attack, attackers try to find the correct password by trying all possible password combinations. This method especially targets accounts with weak passwords. Attackers often use automated programmes to quickly try a large number of passwords. These programmes may use a large pool of passwords, including popular words in different languages and cultures, and dates of birth.
In Dictionary Attack, which is a subtype of Brute Force attacks, attackers create a dictionary containing commonly used passwords. Using this dictionary, they try to decrypt the encryption algorithm of NTLM. This method poses a great risk especially for accounts that use simple and predictable passwords.
Pass-the-Hash Attacks
Pass-the-Hash (PtH) attacks are one of the most serious vulnerabilities of New Technology LAN Manager. In this type of attack, the attacker can authenticate using only the hash value without knowing the user’s password. After the attacker gains local administrator access on at least one computer, he can use this access to jump to other systems.
The basic steps of a PtH attack are:
- The attacker takes over a computer with local administrator access.
- Injects the hash value of the compromised account into its own session.
- It connects to other computers on the network using this hash value.
- If an attacker compromises a higher authorised account, such as a domain administrator, they can gain access to the entire Active Directory.
Relay Attacks
New Technology LAN Manager Relay attacks exploit a weakness in the design of the protocol. In this type of attack, the attacker places himself between the target and the authentication server and captures credentials. This attack, which is especially common in ‘Local Intranet’ areas, causes the user to unknowingly redirect New Technology LAN Manager credentials to a malicious proxy.
The basic stages of relay attacks are as follows:
- The attacker creates a fake proxy using an XSS vulnerability or an open share on the Intranet.
- The user visits the site where this fake proxy is located.
- Internet Explorer recognises this address in the trusted zone and performs NTLM authentication.
- The proxy transmits these credentials to another server, allowing unauthorised access.
These vulnerabilities show that the NTLM protocol is inadequate according to modern security standards. Microsoft therefore recommends the use of the Kerberos protocol instead of NTLM.
Conclusion
The NTLM protocol plays an important role for authentication in Windows networks. This protocol allows users and computers to securely authenticate themselves. However, NTLM has various security vulnerabilities. Brute Force attacks, Pass-the-Hash attacks, and Relay attacks are the main threats facing NTLM.
Because of these security risks, Microsoft now recommends using the Kerberos protocol instead of NTLM. Kerberos offers stronger encryption methods and better security features. Network administrators and security professionals should be aware of their vulnerabilities and consider switching to more secure alternatives whenever possible. This is important to improve network security and protect against potential attacks.
Frequently Asked Questions About NTLM
What exactly is the NTLM protocol?
NTLM is a challenge-response authentication protocol that uses three messages to authenticate a client in a connection-oriented environment, optionally adding a fourth message for integrity.
What is the Kerberos protocol and what does it do?
Kerberos is a computer network authentication protocol that allows resources communicating on an insecure network to communicate by authenticating themselves using tickets.







