Currently Empty: $0.00
What is IP Spoofing and How Does It Work?

IP spoofing, a major threat to Internet security, has become a common technique used by cybercriminals to hide their identities and carry out malicious activities. This method allows attackers to manipulate network traffic by spoofing another device’s IP address. In addition to compromising data security, IP spoofing has the potential to damage organisations’ reputation and cause financial losses.
In this article, we will discuss in detail what IP spoofing is, how it works and its different types. We will also examine effective measures such as VPN and HTTPS to protect against this threat. By also addressing related attack types such as DNS spoofing, we aim to ensure that readers gain a comprehensive understanding of network security. This information is important for strengthening security measures on a personal and organisational level.
What is IP Spoofing?
IP spoofing is a significant threat in the cyber security world. This technique is a method used by hackers to manipulate network traffic. IP spoofing can be translated into Turkish as ‘IP spoofing’ or ‘IP identity spoofing’.
Definition of IP Spoofing
IP spoofing is the creation of Internet Protocol (IP) packets using a spoofed source IP address. By modifying the header information of the IP packet, the attacker creates the impression that the packet comes from a trusted source. This technique began to be discussed in academic circles in the 1980s, and its practical applicability was proven when Robert Morris discovered a vulnerability in the TCP protocol.
Purpose of IP Spoofing
The main purpose of IP spoofing is to hide the identity of the attacker and gain unauthorised access. This technique is usually used for the following purposes:
- Masking the source of DDoS attacks
- Infiltrating target systems by posing as a trusted source
- Manipulating network traffic
- Bypassing filtering mechanisms
Dangers of IP Spoofing
IP spoofing poses serious security risks:
- Compromises data security
- Can damage the reputation of organisations
- May lead to financial losses
- May cause service interruptions by filling the capacity of target systems
- Makes it difficult to identify the source of the attack
Although IP spoofing is not used as frequently as it used to be, it is still an effective attack method. Although many Internet Service Providers (ISPs) try to prevent IP spoofing, it is very difficult to provide complete protection against this threat.
How Does IP Spoofing Work?

IP spoofing is essentially a spoofing technique. This attack method uses the structure of data packets and transmission protocols in internet traffic. Here is the working principle of IP spoofing:
Structure of IP Packets
Each data packet transmitted over the Internet contains the IP addresses of the sending and receiving machines. These packets are separated before being transmitted to multiple users and combined when they reach the destination. Data transmission takes place within the framework of the TCP/IP protocol. This protocol determines all traffic on the Internet, but has some security vulnerabilities.
Changing the Source IP Address
IP spoofing attack takes place in the following steps:
- The attacker changes the source IP address in the header of the IP packet.
- The changed address is shown as belonging to a trusted source.
- The receiving system cannot verify whether the packet actually came from the specified source.
- The parcel is accepted by the buyer as legitimate.
Attackers use various tools to change the IP address. This can be done via the ‘ifconfig’ command on Unix or via ‘TCP/IP properties’ on Windows.
Abuse of Trust Relationships
IP spoofing exploits trust relationships, especially on Unix-based systems. System administrators facilitate administration by establishing trust relationships between machines on the network. In these relationships, authentication is based on IP addresses. Attackers can infiltrate systems by abusing this trust mechanism.
Attacks are generally used in DoS (Denial of Service) attacks. The aim here is to cause service interruption by overloading the query traffic of the target system. Since the attacker does not care about getting a response, the use of fake IP is appropriate.
Cyber attackers carry out the attack by manipulating the TCP handshake process. They stop the handshake before the third stage of the three-way TCP authentication and send a fake acknowledgement. Thus, the receiver thinks that it has established a connection with the real sender.
IP Spoofing Types
It is a technique used by cyber attackers for various purposes. This technique can be used in different types of attacks and each has its own characteristics. Here are the most common types of IP spoofing:
DDoS Attacks
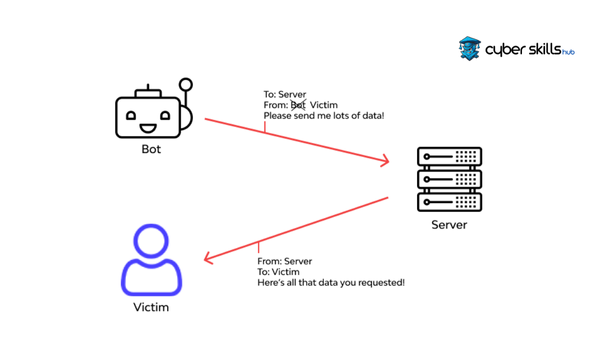
DDoS (Distributed Denial of Service) attacks are one of the most frequently used methods of IP spoofing. In these attacks, cyber hackers send a large number of data packets to target systems using fake IP addresses. This method allows attackers to hide their identity while at the same time slowing down or crashing the target website or network. DDoS attacks are usually carried out by devices infected with botnet worms. In this case, users with bots on their computers often do not realise that they are part of the cyber attacker’s private army.
Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) or Man-in-the-Middle attacks are another important type of attack using IP spoofing. In these attacks, the attacker intercepts the communication between two computers, modifies packets and forwards them without the knowledge of the original sender or receiver. MitM attacks are especially common in places like airports and cafes where Wi-Fi networks are not secure. The attacker can take advantage of IP spoofing to reroute the communication and intercept the entire data stream between the parties.
This type of attack can be used to intercept personal data, passwords and banking information or to impersonate one of the parties. Attackers can target public access points, messaging services or remote working applications. Using a VPN (Virtual Private Network) is considered an effective method to protect against MitM attacks.
Phishing Attacks
IP spoofing can also be used in phishing attacks. In this type of attack, attackers often pretend to be a trusted source in email or other communication channels. Phishing is a popular method among cybercriminals because it is easier to trick a person into clicking on a link via email than to break through the computer’s defences.
IP Spoofing Protection Methods
IP spoofing poses a serious threat to network security. However, there are various measures that can be taken against this threat. These measures should be implemented by network administrators and IT specialists.
Packet Filtering
Packet filtering is an effective defence against IP spoofing attacks. This method controls traffic in and out of the network. The gateway filters packets from outside the network, usually with a source address within the network. This prevents external attackers from infiltrating the addresses of internal machines.
Broad filtering is one of the best methods to prevent spoofed packets from infiltrating the network. These systems examine incoming IP packets and check their source headers. Thus, it blocks malicious packets sent by an attacker on the network using IP spoofing. At the same time, it ensures that packets have legitimate source headers by applying output filtering.
Firewall Usage
Firewalls are an important tool to protect against IP spoofing attacks. These systems help protect the network by filtering traffic containing spoofed IP addresses, authenticating traffic and preventing unauthorised access from outside the network.
It is important to create a firewall to protect data on both corporate and personal computers. However, it is important to choose products from trusted companies, as some firewall applications may themselves contain malware.
Strong Authentication
Using reliable authentication methods is an important line of defence against IP spoofing attacks. This should be implemented even between networked computers. Authenticating all IP addresses and using a network intrusion blocker increases security.
It is also important that trust relationships be carefully established and not used unless necessary. Instead of defining trust relationships to other machines when they install a new Unix machine, system administrators should establish and manage these relationships very carefully.
Finally, web designers are encouraged to migrate sites to the latest Internet Protocol, IPv6. This new protocol makes IP spoofing more difficult by adding encryption and authentication steps.
Conclusion
IP spoofing continues to pose a serious threat to network security. This technique allows cybercriminals to hide their identities and carry out various malicious activities. IP spoofing, which is used in different types of attacks such as DDoS attacks, Man-in-the-Middle attacks and phishing, has the potential to damage the reputation of organisations and cause financial losses as well as jeopardising data security.
Measures such as packet filtering, firewalling and strong authentication can be taken to protect against this threat. Additional layers of security, such as the use of VPN and HTTPS protocol, are also important. Network administrators and IT professionals can make their systems more secure by implementing these measures. In conclusion, awareness of IP spoofing and taking appropriate security measures are crucial to improve network security at the personal and organisational level.
Frequently Asked Questions About IP Spoofing
What is IP Spoofing?
IP spoofing is a method by which an attacker attempts to gain unauthorised access by masquerading as a trusted source. This is achieved by sending messages using fake or misleading IP addresses.
What is Spoof Server?
Spoof Server is a method of redirecting internet traffic from a legitimate website to a fake website by changing DNS records. This is often used to steal login credentials or spread malware.







