Currently Empty: $0.00

One of the most important tools for detecting a cyberattack is the IoC (Indicator of Compromise).
You may notice that your system slows down unexpectedly or exhibits abnormal activity within the security framework being used.
In this case, it is critical to follow the traces identified by the attacker by identifying and analyzing IoCs.
What is IoC?
IoC (Indicator of Compromise) are indicators used to determine the traces of a cybersecurity incident. These indicators indicate the presence of abnormal or malicious activity in a system or network.
Examples such as malware traces, unauthorized access attempts, and unusual data traffic on the network are included in the IoCs. These indicators play a critical role in the process of detecting and analyzing a cyberattack.
IoCs are divided into two main categories as ”leading indicators“ or ”leading indicators”.
IOC’s Definition
IoC (Indicator of Compromise)—in Turkish, indicators of malicious activities—is detailed information used to identify the traces of a cyberattack.
IoCs enable early detection and response of cyber threats.
These indicators, files that have left traces of the attack, IP addresses, malware it includes various digital proofs such as. Security experts identify IoCs to determine whether systems have been hacked.
IoCs are a critical component of the cybersecurity ecosystem. Thanks to these indicators, the necessary defense mechanisms are activated by following the traces of the attackers and the damage is minimized.
Importance and Areas of Use
IoCs play a critical role in cybersecurity processes. With the correct detection and analysis framework, organizations can intervene quickly and effectively against attacks.
- Intrusion Detection: IoCs are used for early detection of current or potential attacks.
- Harm Reduction: Minimizes damages by providing guidance information for rapid intervention.
- Threat Analysis: It provides data to understand the methods and tools of the attackers.
- Recording and Monitoring: It is used to follow the traces of past attacks and prevent similar attacks.
- Awareness Raising and Education: It helps to raise the awareness of security personnel and end users.Thanks to IoCs, security teams can quickly identify and block possible threats.In addition, IoCs are at the center of the efforts to strengthen and continuously improve the security postures of institutions.
Finally, the effective use of IoCs provides a competitive advantage in the cyberwar environment.
Types of IoC
IoC types can be classified by attack vectors, intrusion methods, malware components and many other parameters. Common IoC types include IP addresses, file hashes, domain names and malware signatures.
These types are considered “tips” in the threat intelligence ecosystem. For example, a detected IP address allows for a timely response when it comes from a hostile source. Similarly, a specific file hash helps identify and quarantine malware.
Malware Indicators
Malware indicators (IoCs) are of critical importance in cybersecurity. Thanks to these indicators, threats are detected early.
For example, abnormal network traffic or memory usage may be clues to a possible malware attack. Such abnormal behavior may indicate the presence of malware on a system.
File hashes are one of the most common indicators of malware. Created with algorithms such as MD5 or SHA-256, hash values detect whether the original file has been modified.
Malware often uses specific patterns or signatures. These signatures can be recognized by cybersecurity software and help detect malware. Possible email phishing attacks are also indicators of malware.
Detecting malware indicators early increases the security of businesses and minimizes potential damage.
Network Traffic Indicators
Network traffic indicators are important IoCs that help detect abnormal activities on your network.
These indicators are usually manifested by symptoms such as intense data transmissions from a specific IP address, unexpected protocol usages, or sudden increases in network traffic.
Hackers can contain vulnerabilities in the network by using them, and they can try to collect or damage data in certain ways. Such attack attempts usually leave traces in network traffic.
Incidents such as abnormal DNS requests, attempts to connect to unknown external IP addresses, or suspicious data transfers within the container are common network traffic indicators. In such cases, analyzing the network flow plays a critical role in detecting cyber threats early.
With the right tools and analysis, potential threats can be quickly identified using network traffic indicators. This information allows cybersecurity teams to intervene immediately.
How is the IoC Detected?
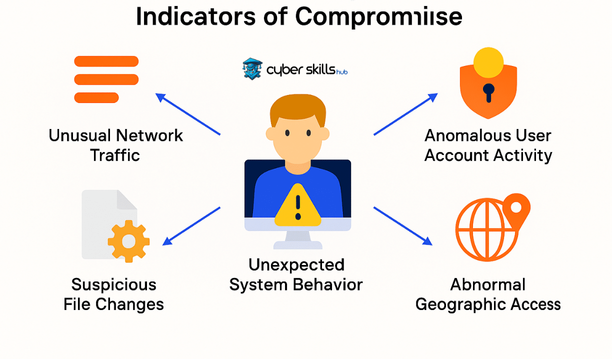
Detecting IoCs requires identifying abnormal activities using security tools and techniques. Indicators of attack these anomalies, known as, typically manifest themselves in the form of unexpected system behavior, memory anomalies, unusual network traffic, or suspicious file changes. Security information and incident management (SIEM) systems play an important role in identifying IoCs by analyzing large amounts of data and provide early warning of cyber threats.

Analysis Tools
Many analytics tools are used to detect IoCs, including container monitoring and analytics tools, which are invaluable in uncovering digital traces.
The first of these tools is Security Information and Event Management (SIEM) systems. SIEM analyzes a wide range of data to identify anomalies among various network activities and system behaviors. These anomalies enable early detection of cyber threats and enable rapid response by cyber security teams.
Another important tool is Network Traffic Analysis (NTA) solutions. NTA identifies suspicious activity by monitoring and analyzing data flows on the network. It is especially effective in revealing anomalous data by performing detailed packet inspection.
Finally, Endpoint Detection and Response (EDR) its systems monitor and analyze suspicious activity on endpoint devices. These systems detect events such as changes to system files or unauthorized access attempts, quickly revealing IoCs. Thanks to these tools, cybersecurity teams can be more proactive, respond instantly to attacks, and improve system security.
Frequently Used Methods
Let’s talk about the methods that are often used in IoC detection.
Log analysis it plays an important role in this context. Logs keep detailed records of network and system activities. Abnormal behaviors and suspicious activities are detected through the analyses performed on these records. In particular, SIEM systems can quickly identify IoCs by effectively analyzing log data.
Another important method is file integrity monitoring.
File integrity monitoring detects unauthorized changes to system files – this method is usually performed by checking file integrity with hash values. Thus, the IoC can be detected quickly in case of any interference.
Another method that is often used is network traffic analysis. With this method, abnormal traffic or unusual activity is detected by monitoring data flows on the network. Today, cyber security experts are performing network traffic analysis more effectively by using more advanced NTA solutions by 2023. These advanced methods provide protection against cyber attacks by quickly and accurately identifying IOCs.
IoC and Corporate Security
IOCs (Security Breach Indicators) are findings that indicate that a security breach or malicious activity is taking place on a network. They are at the center of corporate security policies. These indicators play a critical role in the early detection and response processes of cyber attacks.
By identifying and analyzing IoCs, enterprise security experts can detect potential threats in advance. These indicators include abnormal network traffic, unknown file changes, and suspicious user activity. Accurate monitoring and evaluation of IoCs allows institutions to develop a more proactive and effective defense mechanism against cyber threats.
Role of the IOC
The IoC (Indicator of Compromise) plays a critical role in detecting and preventing malicious activities. These indicators indicate that cybersecurity incidents have occurred or are highly likely to occur.
- Malware Detection: The IoC is used to determine whether malware has infected the system.
- Network Traffic Analysis: It is used to detect abnormal or suspicious network movements.
- Zero Day Deficits: It helps in discovering previously unknown vulnerabilities.
- Incident Response: It enables to respond to security incidents quickly and effectively.
- Security Intelligence: It allows proactive measures to be taken against future threats.
By providing traceable traces of a breach that has taken place, IoCs provide an important tool for continuously assessing the security status of systems.
Accurate interpretation of IOCs is essential for effective prevention of potential threats.
Monitoring and analysis of these indicators is indispensable for the success of cybersecurity strategies.
Implementation Strategies
The use of IoC plays a critical role in improving the effectiveness of cybersecurity strategies.
Therefore, the correct implementation of IoCs significantly increases the capacity of information security teams to identify and respond to threats. As a first step, IoCs need to be compiled from reliable sources and constantly updated. Up to date information should reflect the dynamic nature of the threat environment and be effective against changing threat vectors.
Then, the integration of IoCs into network monitoring and security information and incident management (SIEM) systems should be ensured. This integration makes it easier to quickly detect abnormal activities and take the necessary measures.
Finally, through education and awareness programs, it is necessary to increase the competence of team members in recognizing and interpreting IoCs. These strategic approaches maximize the effectiveness of security measures, while ensuring that potential attacks are detected and prevented in advance. In addition, organizations can re-evaluate IoC analyses on a regular basis and seize opportunities for continuous improvement.
To learn more about IoCs and to learn other important concepts in cybersecurity SANS Institute’s IoC Guide you can visit his page.
Frequently Asked Questions About the IoC
What does the IoC mean?
IoC, in the field of cyber security Indicator of Compromise so A Sign of a Threat means. This term refers to data that hints at the presence of a cyberattack or malicious activity on a particular computer system or network. These data are, log files, network traffic, file hashes it can be obtained from various sources, such as. IoCs provide cybersecurity professionals with critical information to detect attacks and initiate incident response processes. Phishing emails, malware file names or IP addresses objects such as fall within the scope of the IoC. These symptoms early detection, is of great importance in terms of increasing the security of systems and minimizing possible damages. So, The IoC’s using it correctly and effectively is one of the cornerstones of cyber security. In the consideration of cyber security strategies as a whole, The IoC’s identification and analysis play a critical role.







