Currently Empty: $0.00

The brute force attack is a basic one that hackers often use cyber attack the method is. This type of attack relies on the attacker guessing the account or system password by trial and error and can be prevented by encryption.
It is critical for security professionals to understand the effects of these attacks and develop countermeasures. Password policies and two-factor authentication provide effective solutions against such attacks.
Definition of Brute Force
A brute force attack is when an attacker systematically tries many different password combinations to gain access to the target system.
This type of attack can usually be successful on systems without strong security measures. The attacker constantly tries different combinations until he gains access to the target system.
Using a strong password is one of the most effective defenses against brute force attacks. Passwords consisting of random characters and long combinations make it very difficult for attackers to guess the correct password. At the same time, the fact that passwords are changed regularly and are unique also increases the level of security.
Brute force attacks are extremely effective, especially on systems where weak or simple passwords are used. Attackers can quickly try every possible combination using various software and algorithms.
However, this method requires time and computational power, as it involves a large number of unsuccessful attempts. Strong passwords and long passwords make brute force attacks difficult and ineffective.
Modern security methods use various defense mechanisms to detect and prevent brute force attacks.
Working Principle
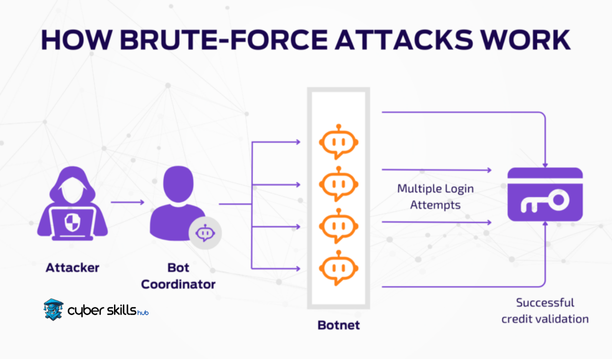
The basic working principle of brute force attacks is that an attacker systematically tries all possible password combinations. This process takes place by conducting random or sequential attempts according to certain rules and continues until the attacker gains access to the target system.
These experiments are usually carried out using automated software and powerful hardware components. Attackers aim to get quick results by focusing especially on weak and common passwords. Since modern brute force vehicles are capable of performing thousands of attempts per second, it is of great importance that these attacks can be effectively prevented.
Password Trial Methods
There are various techniques among Decryption methods, and each of them has its own unique features.
Using common passwords makes you vulnerable to brute force attacks.
One of the main methods is dictionary attack; in this method, attackers systematically try out a list of commonly used passwords.
You can protect against such attacks by using passwords of varying length and complexity. Taking additional security measures such as two-factor authentication (2FA) is also highly effective.

Computational Power and Difficulty
Computing power is a critical factor in carrying out brute force attacks. High processing power allows an attacker to perform millions of attempts per second.
Nowadays, modern CPUs and GPUs can easily handle this processing load.
However, increasing the difficulty ratings of cryptographic algorithms can significantly reduce the impact of these attacks, which is why cryptographic algorithms are so important.
For example, more powerful hashing algorithms such as SHA-256 extend the duration of brute force attacks.
In addition, the power of such attacks can be increased by using distributed computing systems, but this requires system administrators to constantly increase the level of difficulty.
As a result, high computational power can make brute force attacks more effective, but increasing the difficulty level using cryptography reduces this threat to a minimum. Strong encryption methods and additional layers of security make such attacks significantly more difficult
Advantages and Disadvantages
Among the advantages of brute force attacks, the most notable is that all combinations can be tried systematically.
In this method, the attacker can reach the target with sufficient time and resources only, without the need for any preliminary information, which is the biggest advantage of brute force.
But, “time” and “source” its necessity creates the most important disadvantages of brute force attacks.
Security Vulnerabilities
Vulnerabilities refer to weak points that can cause a system to be left unprotected.
- Insufficient Encryption: Weak or incomplete encryption methods can easily cause attackers to hijack data.
- SQL Injection: Malicious queries to databases can lead to unauthorized data access.
- XSS (Cross-Site Scripting): Injects malicious scripts into user browsers, which can lead to the theft of personal information.
- Update Shortcomings: Failure to update software and systems allows known vulnerabilities to be exploited by attackers.
- Insufficiency of Safety Inspections: The lack of effective controls results in the inability to detect existing weaknesses. The detection of security vulnerabilities should be ensured by security audits and tests.The implementation of regular security protocols is critical to reduce risks.
Protection Methods
Effective and careful methods should be adopted to protect against brute force attacks.
- Implementing Complex Password Policies: Create passwords that are both long and consist of random combinations.
- Using Two-Factor Authentication (2FA): Add a second verification method for accessing accounts.
- Setting the Entry Attempt Limit: Temporarily lock the account after a certain number of failed login attempts.
- CAPTCHA Apply: Prevent automated attacks by adding human verification controls to login forms.
- Setting Up IP Blocking Systems: Use IP tracking systems to detect suspicious IP addresses and block their access.These methods create an effective line of defense against brute force attacks.In addition, organize regular security awareness trainings to improve system security.
Backup strategies enable quick recovery in case of data loss.
Areas of Use
Brute force attacks are used for various purposes in different areas.
Cybercriminals use the brute force method to break the password of accounts by trial and error to gain unauthorized access. Such attacks create major ethical and legal problems, especially in systems hosting financial and personal information.
It is also used in operations such as ”password recovery“ and ”security testing”.
Password Cracking
Password cracking is an attack carried out with the aim of obtaining the password of a system or application. Usually, it is carried out using brute force methods, and people’s use of weak passwords increases the chances of success of such attacks.
In brute force attacks, password combinations are systematically tried.
In such attacks, commonly used password lists and powerful processors are used.
An attacker tries various password combinations sequentially and continues this process until he finds the correct password.
Software and special hardware are usually used to speed up the password cracking process. The fact that passwords are complex and long increases the resistance to brute force attacks.
As a result, password cracking, is a threat that requires cybersecurity experts to take serious measures. Strengthening passwords and using additional layers of security provide an effective defense against such attacks.
Safety Tests
Security tests are critical analyses performed to evaluate the security of systems.
These tests are designed to understand how a system will react in the face of internal and external threats. Penetration tests (Pentest), is widely used to identify security vulnerabilities. In addition, social engineering tests are applied to measure the security awareness of employees and identify points of vulnerability.
Vulnerability scans are performed with automated tools to detect known vulnerabilities in the system. These scans should be performed at regular intervals.
Cyber security experts, analyzing the results of these tests, they make recommendations to strengthen the security policies of the system. Security tests not only reveal problems, but also make systems more resistant to future attacks. Thus, businesses are protected from negative effects such as data loss, financial losses and reputation loss.
Frequently Asked Questions About Brute Force
What is brute force?
Brute force attack is a method used especially in password cracking attacks. In this type of attack, all possible password combinations are systematically tried. Therefore, attacks require high computational power and time. With this method, attackers can easily hijack passwords, especially weak or short ones. Stronger passwords take a long time to break, as they are created with more complex combinations. It is important to take additional security measures such as creating strong passwords and two-factor authentication to protect against brute force attacks. In addition, it is necessary to use end to end security solutions such as firewalls and intrusion detection systems to protect your systems from attackers. In this way, attacks can be detected and prevented earlier.
Is Brute Force reliable?
Brute Force attacks are quite troublesome and time consuming, especially in systems where complex passwords are involved. Its reliability is often the subject of debate. In brute force attacks, all possible combinations are tried to find the correct password. This method is quite costly both in terms of time and resources. This method is usually ineffective on systems with strong password policies because the length and complexity of passwords make it difficult to attack. Brute Force attacks become almost impossible, especially on systems with additional layers of security, such as two-factor authentication.







