Currently Empty: $0.00

Attack Surface Fundamentals
Attack surface is a term that covers all points where an organization can be exposed to cyber threats. These points range from external and internal networks, software, mobile devices, and the human factor. It is critical that this surface, which threat actors can exploit, is narrowed as much as possible by disabling unnecessary services and security controls.
A comprehensive security strategy should ensure that the attack surface is effectively managed. Patch management, security configurations, access controls and awareness training are some of the methods that should be put in place to enable this management. On the other hand, with the rise of cloud computing and agile development practices, the attack surface has become more complex, making security operations an area that requires a more dynamic approach.
For more information, see ‘Docker Security: Threats and Solutions‘ for more information.
Definition and Scope
The attack surface defines all information systems and assets of an organization that can potentially be exploited by cyber threat actors. These assets include network structures, software, devices and user interactions.
Keeping the attack surface, one of the central elements of risk management, as narrow as possible is critical to minimizing threat vectors. Information security policies and procedures create mandatory mechanisms to narrow this surface.
In protecting against cyber attacks, reducing the attack surface is essential.
Identifying and managing the attack surface is a continuous process. The integration of new technologies, system upgrades, changes in user behavior and business processes all contribute to the dynamic nature of this surface. Therefore, security teams need to continuously audit and develop adaptive security measures.
For more information on this subject, you can review our article titled ‘What is System and Network Expertise and How to do it’.
Attack Vectors and Methods
In cybersecurity, attack vectors refer to the ways in which threat actors can infiltrate or damage a system. These ways are often used to exploit system vulnerabilities.
Traditional attack methods include malware, phishing and social engineering. In addition, denial of service actions such as DoS/DDoS attacks are also common methods.
Today, attackers are developing more sophisticated attack methods against new technologies such as IoT devices and cloud services. API vulnerabilities and misconfiguration errors are particularly popular targets.
It is important for cybersecurity professionals to understand that each attack vector is aimed at a specific threat landscape or system vulnerabilities. Thus, specific protection strategies and risk mitigation plans must be developed.
In an ecosystem where attack vectors are constantly evolving and new methods are emerging, firewalls are only the starting point. Effective defense requires multi-layered protection strategies.
Risk Assessment and Management
Risk assessment is critical in the process of defining the attack surface. Defining the contribution of each asset and service to the threat surface is essential to focus protection efforts.
It should be remembered that the risk analysis on targeted systems and assets should be structured to cover both the current security situation and potential threats. This should include detailed information on the nature of the threats, the likelihood of attacks occurring and their expected impact.
Risk management is the process of continuously monitoring, prioritizing, mitigating or eliminating identified risks. This process forms the backbone of a comprehensive security strategy.
For more information on security strategies, read our article ‘Secure Development Process in Cybersecurity with DevSecOps’.
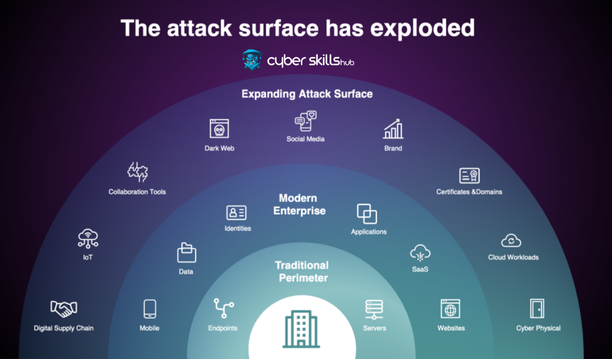
Methods to Narrow the Attack Surface
A reduced attack surface on systems is a critical factor in preventing security breaches. The smaller this surface, the fewer vulnerability points an attacker can target.
Typically, efforts to narrow the attack surface are supported by a variety of techniques such as shutting down unnecessary system services, implementing network segmentation, regularly applying up-to-date security patches and enforcing multi-factor authentication. In addition, strict access control policies should be implemented and unnecessary user permissions restricted. These steps significantly limit the scope of the attack surface.
The widespread use of integration and automation technologies ensures that security measures are effectively implemented and managed. The automated distribution of security patches and software updates reduces the need for manual intervention and contributes to narrowing the attack surface.
Finally, regular security audits and penetration testing also play a vital role in narrowing the attack surface. These audits evaluate the effectiveness of existing security measures and uncover system vulnerabilities. By simulating attack scenarios, vulnerabilities are proactively identified and remediated, allowing for continuous improvement and strengthening defense capabilities.
Continuous Safety Improvement
Cybersecurity is a continuous process, not a one-off operation. The rapid evolution of the threat landscape requires dynamic updates to security measures.
- Assessment and Analysis: Conduct continuous security situation assessment and identify vulnerabilities and threats.
- Training and Awareness: Training and raising awareness of personnel on safety reduces human error.
- Patch Management: Regular application of security patches and updates ensures that systems are protected against current threats.
- Access Control: Minimizing unnecessary access rights by restricting them narrows the attack surface.
- Automation: Automating security processes increases operational efficiency and speed of response.
Regular penetration tests should be carried out to measure the effectiveness of safety measures.
Promoting continuous improvement at the whole organization level by creating a culture of safety strengthens defense strategies.
Analyzing the Attack Surface
Attack surface analysis is the process of understanding potential threat vectors and vulnerabilities. This process forms one of the cornerstones of corporate security strategy and contributes to the development of threat models. The analysis starts with identifying the critical components of the system and assessing their risk level.
Risk analysis involves a detailed examination of security vulnerabilities, the motives of threat actors and the types of attacks. For an effective attack surface analysis, a realistic threat model should be created at the organizational level and continuously updated. Thus, the risks that the organization will face if a particular vulnerability is exploited are addressed from a holistic perspective.
A comprehensive attack surface analysis facilitates prioritization by classifying vulnerabilities. Based on the results of the analysis, organizations can be more effective in taking proactive security measures and increase their defense capabilities.
Identifying Security Vulnerabilities
Vulnerabilities open the door to threats.
Identifying vulnerabilities in the cybersecurity ecosystem is a complex and multi-layered analysis process. It makes it possible to isolate potential risk factors through extensive assessments of sensitive information, systems and network structures. This process is key to developing a proactive protection strategy against current and future threats.
Vulnerabilities open your systems to unexpected attacks.
The process of finding a security vulnerability should always be systematic. Businesses identify potential vulnerabilities in their systems using methodologies such as automated scanning tools, penetration tests and regular security reviews. This approach contributes to maintaining business continuity by minimizing operational risks.
Prioritize the most critical vulnerabilities and address them quickly.
Identifying security vulnerabilities plays a key role in protecting information systems. Using modern threat intelligence and risk assessment methods, vulnerabilities are identified and ranked for a fast and effective response. This approach has become one of the critical cybersecurity trends of 2024 and one of the best practices.
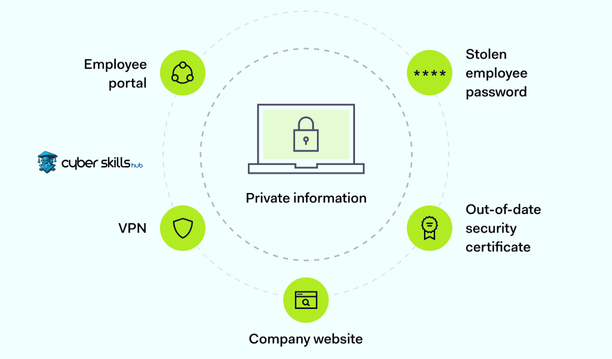
Protecting Critical Systems
For cyber security experts, protecting critical systems is one of the most important measures to be taken. These systems stand out as structures that sustain the basic functions of organizations and host valuable information.
- Isolating Systems through Segmentation: Make your network more secure by segmenting it with different levels of security.
- Perform Up to date Vulnerability Scans: Detect potential threats early by performing regular vulnerability scans on all systems.
- Tighten Access Controls: Strengthen access controls by managing in detail who can access who, when and what resources.
- Implement Data Encryption: Minimize the impact of a potential leak by encrypting all critical data transferred and stored.
- Firewalls and Intrusion Prevention Systems: Optimize and continuously update the network’s layers of protection against external threats.
These protection measures are vital to narrow the attack surface and strengthen defense mechanisms.
In addition to technical security controls, trained personnel and a strong security policy also play an effective role in protecting critical systems. High awareness provides protection against threats such as social engineering and minimizes human error.
Best Practices and Strategies
Continuous Training and Awareness Raising: As cybersecurity threats are constantly evolving, keeping the training of security personnel regularly updated is important in understanding and mitigating the attack threat surface. Training programs should be made part of daily workflows to encourage staff to be proactive against threats and security breaches.
Optimizing Risk Assessment Processes: An effective cybersecurity strategy should be based on in-depth risk assessment processes. Analyzing and prioritizing potential threats is a critical step in determining response strategies against specific attack vectors.
Safety Training and Awareness
Cybersecurity awareness is as important as protective strategies because the human element is often a weak link.
- Understanding Corporate Security Policies: Employees should have a comprehensive understanding of the organization’s security policies and procedures.
- Regular Training Programs: Cybersecurity training should be provided on an ongoing basis to improve employees’ ability to recognize threats and react appropriately.
- Simulation and Scenario Based Trainings: Learning effective response methods against cyber threats that may be encountered in real life should be encouraged.
- Continuous Updating and Innovation: Regular updating of training materials is critical to keep pace with evolving threats.
During the training process, employees should be encouraged to practice cyber security as part of their daily work routines.
Finally, strengthening the capacity of employees to respond to and manage cyber incidents is important for embedding a security culture throughout the organization.
Role of Technological Security Tools
Threat detection and response systems play an important role in narrowing the attack surface. They proactively detect anomalous behavior and potential vulnerabilities by continuously monitoring suspicious activity on computer networks.
Firewalls and antivirus programs are the first line of defense against malware. These tools help filter and isolate known pests.
Intrusion detection/prevention systems (IDS/IPS) and endpoint security solutions play a critical role in detecting and preventing threats inside and outside the network. These systems enrich cybersecurity defense mechanisms and make security dynamic, thus supporting efforts to minimize the attack surface.
In addition, security management tools and automation technologies provide the comprehensive visibility needed to effectively manage cybersecurity operations. With these tools, security teams can coordinate and streamline threat hunting, incident response and crisis management. As a result, these technological tools are indispensable for continuously improving the cybersecurity posture and proactively addressing potential vulnerabilities.
Frequently Asked Questions about Attack Surface
What is the attack surface?
The attack surface refers to all points where an organization can be exposed to cyber threats. These include external and internal networks, software, mobile devices and the human factor.
What is the importance of narrowing the attack surface?
Narrowing the attack surface reduces the potential points of vulnerability that threat actors can exploit, thereby significantly reducing the organization’s security risks.
How is attack surface analysis performed?
Attack surface analysis examines all information systems and assets of the organization, identifying potential threat vectors and vulnerabilities. This process helps to develop threat models and implement risk management strategies.
Which techniques are effective in narrowing the attack surface?
Effective techniques include shutting down unnecessary system services, network segmentation, applying up to date security patches and multi-factor authentication. These techniques limit the scope of the attack surface.







