Currently Empty: $0.00

At a time when safe internet use is becoming increasingly important, tracking your IP address may worry you. Cybernetic attacks and threats of data theft make the importance of hiding your digital footprints even more apparent. This is a central concern for cybersecurity professionals, especially at the enterprise level:
Proxy servers play a critical role in hiding your real IP address by redirecting your internet traffic.
As one of the main tools to protect online privacy and provide anonymity, proxies can adapt to different needs and scenarios.
Proxy Themes
A proxy is an intermediate server that intervenes between two points exchanging information on a network, allowing the user to hide their real IP address. They are often preferred by individuals or businesses that aim to browse the Internet anonymously and bypass access restrictions. In essence, the proxy server acts as an intermediary between the user and the destination server, routing requests through its IP address. This offers the possibility to increase online privacy and security by hiding the user’s identity and location.
Proxy Function and Advantages
Proxy servers are intermediary systems that mask the user’s real IP address; they are important for increasing online privacy and providing anonymity.
Proxies not only provide anonymity but also have the potential to prevent data leaks.
The anonymity provided by the proxy protects users from risks such as cyber surveillance and monitoring, and is backed by layers of security such as traffic encryption and access control.
At the same time, it brings important advantages, such as access to geographically restricted content – overcoming geographical barriers and not being subject to local restrictions – and regulating the flow of information.
Different Proxy Types
Proxy servers are divided into different types according to their tasks and uses. Here are a few basic proxy types:
- HTTP Proxy: Designed to route web traffic and uses the HTTP protocol.
- HTTPS/SSL Proxy: A type of proxy that routes encrypted SSL traffic and provides a secure web experience.
- Sock4/Sock5 Proxy: Application-level proxies that can work with various protocols and offer more advanced security features.
- Transparent Proxy: Routes traffic without the user’s knowledge and is often used for content filtering or caching.
- Anonymous Proxy: Hides the user’s IP address but identifies itself as a proxy.
- Distorting Proxy: Gives a false IP address and thus anonymizes the user identity.
- High Anonymity Proxy (Elite Proxy): Hides the user’s IP address and does not reveal that it is a proxy.
Each type of proxy has unique features and should be compatible with your security and performance requirements.
When choosing a proxy, it is important to consider what suits your intended use and security needs. A reliable and correctly configured proxy service should be an obvious choice, especially if online anonymity and data security are your main priorities.
How to Hide Your IP Address
The primary way to hide your IP address is to use a reliable proxy service. A proxy can mask your real IP address by getting between the user and the destination server.
In addition, virtual private network solutions, or VPN services, create encrypted tunnels to protect your personal data by making you appear to be in a completely different geographic location. A VPN is a powerful option for speed and security.
The TOR network can also be an alternative option for anonymity by routing your internet traffic. TOR supports the protection of personal privacy through layered encryption.
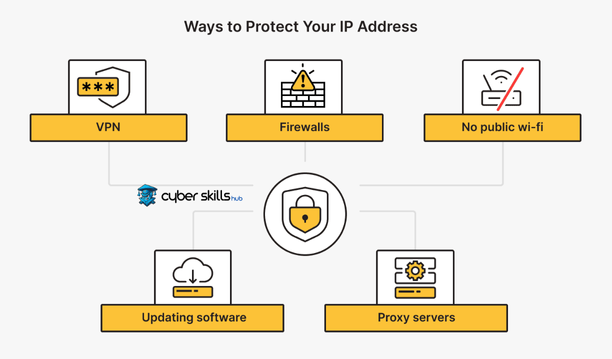
Impact of VPN Use on IP Privacy
VPN services are a critical tool for hiding users’ IP address. A VPN hides your real IP address by routing your internet traffic through a remote server.
- Each user’s traffic is securely transmitted within an encrypted tunnel.
- Users can overcome geographical limitations and access local content even from restricted areas.
- Various VPN services offer security options tailored to users’ needs.
- Thanks to its ease of use, almost everyone can easily configure VPN settings. If you would like to learn more about how VPN and proxy servers can be used effectively in cybersecurity, check out our article‘Cyber Security Training: Become an Expert in the Industry‘.
Hiding your real IP address makes online tracking more difficult and increases privacy.
VPN services are also an effective way for users to reduce their digital footprint, but it is essential to choose the right VPN based on the level of usage.
Tor and Anonymity
The Tor network is free and open source software that allows you to browse the internet anonymously. Users’ information travels through a series of nodes operated by volunteers around the world and is protected by layered encryption (onion routing).
- The user first downloads and installs the Tor client.
- The client routes the user’s internet traffic through randomly selected Tor nodes.
- Each node decrypts the encrypted data one level at a time in a layered fashion before sending the traffic to the next node.
- The last node (egress point) accesses the internet as a normal user because the traffic is now unencrypted.
- This hides the user’s real IP address and location.
Anonymity is one of the cornerstones of the Tor network, making it difficult for individuals or organizations to determine the true identity and location of users.
One of the major problems Tor faces is slow network speed and performance issues. This is because traffic is passed through a large number of nodes and each node encrypts and decrypts the communication respectively. Nevertheless, it is a valuable solution for users seeking a high level of anonymity.
Place of the Proxy in Everyday Use
Proxy servers increase online privacy and provide access to banned sites by routing the users’ internet connection through an intermediary server. For example, a company employee or student can use this technology to bypass corporate network restrictions and browse the internet anonymously. Security measures such as personal data protection and IP address obfuscation become more effective with proxy services.
Many online platforms for education, business and entertainment purposes only allow access to certain content from certain regions due to geographical restrictions. The use of proxies overcomes such geographical restrictions, providing a global internet experience and allowing users to access information freely. This makes it a highly effective tool for international market research, analyzing regionally diverse digital content and overcoming cultural barriers.
Privacy and Securityon the Internet
Protecting personal data while browsing the internet is of fundamental importance, as it carries many risks, from identity theft to fraud. Proxy servers provide a line of defense against such threats by masking the IP address. Web proxy services offer effective solutions to anonymize your internet traffic and increase your online privacy.
Proxy services help you maintain security and privacy in the virtual environment by encrypting data and providing anonymity. They play a critical role in keeping users safe by making it difficult to intercept or trace personal information, especially when used on public Wi-Fi networks, unreliable or suspicious connections. Using a proxy in such environments strengthens one more layer of your personal data security. To further enhance your online privacy and learn how you can protect your digital footprints, check out ‘Protecting Your Digital Footprints: A Free Guide from CyberSkillsHub‘.
However, in addition to proxy servers for security and privacy, it is also important to use a VPN (Virtual Private Network) to provide multiple layers of security. While proxy servers usually hide only specific app or browser traffic, a VPN provides broader protection by encrypting your entire internet connection.
Finally, an effective internet privacy strategy should not depend solely on the use of one tool. Defenses such as using up-to-date antivirus software, creating strong passwords, and implementing multi-factor authentication, in combination with proxy and VPN technologies, are highly effective in protecting privacy and countering cyberattacks. Each layer of precaution plays an important role in minimizing the risks you face in cyberspace.

Overcoming Access Barriers
Proxy servers are an indispensable tool for providing access to various content that is subject to access restrictions. With proxy services, users can seamlessly access their favorite geo-restricted websites. Through these servers, anonymous access to blocked websites and services is possible. Using a proxy helps you bypass restrictions on access to your favorite websites.
Access barriers on the Internet may be created by regional restrictions or local network policies. Using a proxy allows you to temporarily bypass such restrictions, as well as to browse the internet anonymously while protecting your personal privacy. This is especially important for users who want to access content from different countries.
In some cases, organizations or schools may block access to certain sites, such as social media platforms, in order to improve network efficiency. In such scenarios, utilizing proxy services allows free access to information by overcoming these restrictions. For more information on the legal aspects of proxy and VPN use and its role in combating cybercrime, see ourarticle ‘Cybercrime: The Most Common Internet Crimes in Turkey‘ for more information.
Effective use of proxies requires proper configuration and vigilance against potential security vulnerabilities. However, when used to circumvent access restrictions for legitimate purposes, such as education, it can be an effective way for users to gain freedom from content access restrictions. Experts recommend that the use of such methods should always stay within legal boundaries and avoid malicious activity.
Choosing the Right Proxy
The main priority in choosing a proxy is the reliability of the service. A reliable proxy service is characterized by its data encryption capabilities and the degree of anonymity it provides. It is also important to evaluate technical criteria such as supported protocols, available bandwidth and response time. Particularly for enterprise use, the quality and continuity of the service provider’s customer support services are critical in the event of unexpected situations.
Another important factor when choosing a proxy service is its cost-effectiveness. Choosing providers that offer high quality services while minimizing the financial burden provides cost advantages, especially for continuous and long-term use. Therefore, making a balanced decision with budget in mind is an important consideration in the proxy selection process.
Tips for Personal and Corporate Use
Security is essential when using a proxy. While modern web applications facilitate our daily workflows, the use of proxies can make access to these applications more secure.
Corporate security networks often include layered defense strategies. For individual users, proxying is important to protect private information and keep online activities anonymous. Businesses can use proxies to protect the internal network and as an additional layer against cyber threats.
Anonymity is not always guaranteed.
Configuring the proxy with the correct settings is key to protecting your data and identity. The reliability of the proxy service provider affects the quality and continuity of the service and should therefore be examined in detail.
Proxy service selection should be made in line with the needs.
Different proxy types come with their own advantages and limitations. For example, SOCKS proxies are generally suitable for email or P2P (peer to peer) traffic, while HTTP/HTTPS proxies are more efficient for web browsing. Therefore, choosing the type of proxy that best suits your intended use is vital to ensure effective protection.
Free vs. Paid Proxy Services
While free proxy services may seem attractive, they can raise serious concerns about performance and security. There may be malicious actors behind these benevolent services, even leaking user information or monitoring traffic. For this reason, it is recommended to avoid free options for professional and security-oriented approaches.
Paid proxy services usually offer more reliable and stable service. Custom configured options can be available according to the user’s needs.
The limited resources, weak infrastructure and ad-supported models of free proxies often impose limitations in terms of speed and security. Basic security measures such as traffic encryption may be neglected or ignored altogether. In contrast, paid services offer advantages such as wide bandwidth, high-level encryption protocols and customer support.
If you want complete control over your privacy and security, it is recommended to opt for a paid proxy service. The high level of customization ensures a perfect fit for private and business users. Moreover, reliable services backed by payments offer the assurance of a predictable and regular quality of service for you, as well as protecting your online activities. It is therefore vital to consider the features on offer as well as the reliability and reputation of the service provider when making a decision.
Frequently Asked Questions About Proxy
What is a proxy?
A proxy is an intermediate server that intervenes between the user and the destination server to hide the user’s real IP address. It provides online anonymity and is used to bypass access restrictions.
What are the advantages of a proxy?
Proxy servers increase online privacy, provide anonymity and have the potential to prevent data leaks. Theyalso offer access to global content , bypassing geographical limitations.
What are the types of proxies and what are the differences between them?
Proxy types include HTTP, HTTPS/SSL, SOCKS4/5, Transparent, Anonymous, Distorting and High Anonymity (Elite) Proxy. Each is designed for different needs and security levels.
What is the difference between a VPN and a proxy?
A VPN provides anonymity by encrypting all internet traffic, while a proxy is usually only used for specific applications or browsers. A VPN offers stronger security and privacy overall.
What is the Tor network and how does it work?
The Tor network hides a user’s IP address and location by routing internet traffic with layered encryption through nodes operated by volunteers around the world. It enables anonymous browsing but can result in slow speeds.
What is the place of a proxy in everyday use?
Proxies are mainly used to bypass corporate network restrictions, access banned sites and increase online privacy. It is also preferred to overcome geographical restrictions on educational and business platforms.
What are the risks of free proxy services?
Free proxy services can pose security and performance risks. They can be operated by malicious actors, user data can be leaked and traffic can be monitored.
How to choose the right proxy?
When choosing the right proxy, factors such as the reliability of the service, supported protocols, bandwidth offered, response time and cost effectiveness should be considered. If security is of particular importance, a paid and reliable proxy service should be preferred.







