Currently Empty: $0.00
What is a botnet? Dangers of Taking Control of Computers on a Network

Like the child who once destroyed a wasp’s nest, a hacker can make dozens of computers part of a botnet at the touch of a button. This digital nest becomes a chaotic space where information and security are compromised and vulnerable networks are invaded.
The danger of botnets is real.
Your sense of security is shaken as computer networks face a hidden and insidious enemy. This enemy is called a botnet, and it is unimaginable what it can do with the machines under its control.
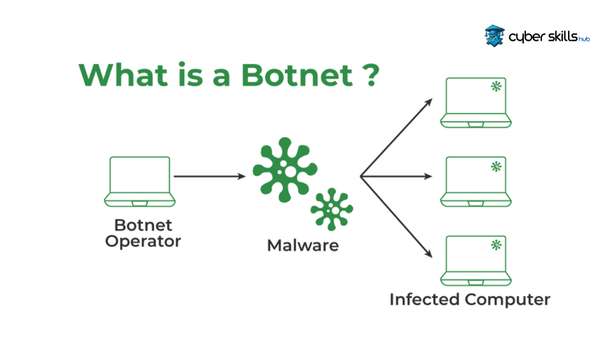
Basic Definition of Botnet
A botnet consists of networks of infected computers, controlled by a hacker, communicating with each other. These networks infect themselves with malware called “bots”.
This malware creates machines, often referred to as “zombie computers”, where users unwittingly lose control of them. Through this zombie network, hackers can launch various cyberattacks, such as spamming, DDoS attacks or data theft.
Botnets are one of the major threats to cybersecurity and are very difficult to detect and clean up.
Botnet Types
Botnets are often differentiated by their purpose. They range from sending spam emails to carrying out large-scale DDoS attacks. They are also used to exfiltrate sensitive data for specific targets.
Botnets with financial goals are equipped with malware such as trojans and keyloggers to steal user information. There are also types of botnets used for ad fraud and cryptocurrency mining.
Botnet infections are a constant threat that requires an immediate response to network security vulnerability.
Different types of botnets also vary in their emergence and distribution methods. Sometimes social engineering tactics are used to persuade users to download seemingly legitimate but malicious programs, while other times systems are infiltrated by exploiting security vulnerabilities. Diversity is a factor that makes botnets difficult to detect and block.
How do botnets occur?
Botnets are formed when individual computers are compromised by malicious software (malware). Malicious actors carry out the initial attack, usually by sending emails containing a malicious link or attachment.
The malware infiltrates and infects the system without user consent.
These infected machines are then connected to command and control (C&C) servers so that they can be remotely controlled. The botnet creator can then remotely direct these computers to carry out their malicious actions.
Compromised computers can be used to detect and infect other uninfected systems. Thus, the size of the botnet network increases exponentially. In addition, botnets are formed by exploiting vulnerabilities, using exploit kits and automated tools to create bot armies for actions such as denial of service attacks (DDoS) and data theft.
Role of Seized Computers
Compromised computers are often critical to the growth and sustainability of the botnet network. Under the attackers’ commands, these machines can be used to participate in spam, attack other systems or disrupt targeted services. In addition, attacks on these computers can be used to steal users’ personal information and engage in illegal activities such as cryptocurrency mining.
Each computer in a botnet acts as a vector that increases the power and impact of attacks. These infected machines act as pawns in the execution of complex attack scenarios under the control of attackers, which often requires more resources and expertise to overcome cybersecurity defenses.
To learn how botnet attacks happen and how you can protect yourself from such attacks, see Cyber Security:How to Defend Against Technological Threats?
DDoS Attacks and Botnet Relationship
DDoS (Distributed Denial of Service) attacks aim to render targeted systems dysfunctional by deliberately blocking their access. Botnets are the main power source in such attacks.
Botnets increase the intensity and scope of DDoS attacks by taking over a large network of computers. By using infected machines, attackers can create excessive traffic against targeted servers, halting services. This makes them more powerful and effective than attacks from a single point.
Each infected computer, called a “bot”, operates as part of a network that increases the severity of the attack. The size of the botnet is an important factor determining the success of a DDoS attack. Traffic that exceeds the capacity of the targeted services causes them to crash and become unavailable.
The botnets that are the source of the attack often have a global distribution, making it difficult to implement countermeasures. The large number of infected devices conceals the true origin of the attack and undermines tracing efforts.
In conclusion, botnets behind DDoS attacks occupy a special place among today’s cyber security threats. Considered as indispensable tools for systematic and directed attacks, botnets are constantly analyzed and monitored by cyber security experts. For more detailed information on how DDoS attacks are carried out and the effects of these attacks, you can read our article titled What is DDoS? This article provides comprehensive information on how DDoS attacks are carried out and how to protect yourself from them.
Spam and Malware Distribution
Botnets have the capacity to spread spam emails and malware quickly and efficiently over a large network.
- Phishing Attacks: Distribution of fake emails aimed at compromising user information.
- Malware Propagation: The distribution of malicious software such as viruses, trojans, worms, etc.
- Adware (Adware): The introduction of unwanted or harmful advertisements into user systems.
- Crypto Mining: The usurpation of users’ processing power to mine cryptocurrencies.
- Ransomware: Encrypting user data and demanding a ransom.
Spam and malware are the main reasons why botnets pose a serious threat to users and organizations.
Spam and malware distribution by botnets are among the actions that threaten general network security and can cause financial losses to users.
Challenges of Botnet Detection
Detecting such threats is a challenging process, as botnet activity often resembles ordinary network traffic. Malicious actors use sophisticated techniques to mask botnet traffic and can mislead analysis tools by encrypting traffic or connecting to command and control servers at irregular intervals. In addition, low-intensity attacks that resemble the normal behavior profiles of the network also tend to bypass detection systems. The multifaceted and evolving nature of botnets requires security experts to constantly develop new detection methods, keeping agencies and organizations in the cybersecurity ecosystem on constant alert.
Inadequacy of Traditional Security Software
Traditional security software is based on static signature-based detection methods. However, modern botnet attacks easily bypass such methods because botnets are dynamic and constantly evolving threat vectors. This means that traditional systems are slow to update their switchboards and therefore cannot keep up with current threats.
As attack vectors become more sophisticated, traditional antivirus solutions are falling behind. Their ability to recognize new threats in advance is limited.
High-level polymorphic malware and metamorphic threats cannot be detected using signature-based detection mechanisms. These threats change themselves, presenting a new digital identity with each attack, making them difficult to detect. This requires a fundamental rethink of the structure of traditional security software.
In today’s complex cyber-attack environment, traditional security software is inadequate. With each update, new zero-day attacks and unprecedented threat models emerge. This emphasizes the need for security systems to be equipped with continuous learning algorithms that constantly and automatically evolve and adapt. Static protection strategies are no longer sufficient; dynamic and proactive security mechanisms are needed against constantly evolving threats.

Monitoring Suspicious Network Activity
Botnet activity often manifests itself in traffic patterns that are often overlooked. This traffic should be subjected to detailed analysis by network security equipment.
A sudden increase in bandwidth usage can be an indicator of suspicious activity.
Epidemic malware infections create specific traffic spikes over time. These spikes can be detected based on concurrent actions taken by affected devices.
Detailed network monitoring and traffic analysis are critical for early detection of botnet activities. In this process, next-generation techniques such as anomalous behavior modeling and machine learning come into play. Monitoring and controlling the flow of unencrypted data over insecure protocols is additionally important. The biggest challenge for experts is to distinguish these anomalies from ordinary network traffic.
Prevention Methods and Safety Recommendations
To protect against botnet attacks, comprehensive security policies must be established and strictly enforced at all levels. Up-to-date antivirus software should be used for malware protection, and operating systems and applications should be updated regularly. Defense mechanisms such as firewalls and intrusion prevention systems (IPS) should be effectively configured to enhance network security.
Education and awareness programs play a critical role in making users aware of social engineering tactics and phishing attempts. Basic security measures such as not clicking on suspicious email attachments or links and using strong and unique passwords are important to protect against botnets.
For more information on how to deal with phishing attacks and social engineering tactics, see Social Engineering Attacks: Protection Methods. This article provides comprehensive information on how to recognize phishing attempts and how to take effective measures against such attacks.
Strong Passwords and Firewalls
Strong passwords are the foundation of a security strategy.
Strong passwords are a critical defense mechanism for protecting personal data. Consisting of a string of characters, they are difficult to crack due to their complexity and greatly increase the security of a user account. Length, numbers, symbols and capitalization are all necessary to maximize the password’s reliability.
Password strength is important, but it is not enough on its own.
Even the strongest password can be inadequate in the absence of firewalls. Firewalls act as a barrier that controls incoming and outgoing network traffic and protects the system against external threats by blocking malicious traffic and data exchange.
Firewalls provide a solid layer of protection.
The combination of strong passwords and firewalls provides effective protection against botnet threats. However, additional security measures such as two-factor authentication, regular software updates and the principle of low privilege are also crucial. These measures will be vitally important in the dynamic threat landscape in cybersecurity in 2024 and beyond.
Importance of Continuous Software Updates
Updates strengthen the software’s defenses.
As cyber attackers continually develop new methods, software vendors release regular updates to combat these threats. These updates are often designed to close new vulnerabilities, fix bugs and improve system performance. Updates are especially important when considering the types of attacks that target older software versions.
Outdated software carries risks.
Keeping software up to date is the most effective way to prevent malware like botnets from taking over your network. Skipping updates can compromise the entire system, not just a vulnerability, and can lead to cascading damage. This is a serious cybersecurity risk for both personal and organizational information security.
Staying up to date is the basis for protection.
Updating a software to the latest version may include security patches and improvements. By 2024, threats in cybersecurity are constantly evolving and software is being updated in parallel. Systems that do not keep up with the times become easy targets for potential threats and the risk of falling into the network of botnets increases.
The information provided in this article is a basic guide to cybersecurity threats. However, technological threats in cybersecurity are constantly evolving and becoming more complex. If you would like to learn more in-depth about this topic, read our article Cyber Security: How to Defend Against Technological Threats. This resource provides more information on advanced methods and strategies for dealing with cybersecurity threats.
Frequently Asked Questions About Botnet
What is a botnet?
A botnet is a system of infected computer networks controlled by a hacker. These networks can take malicious actions such as organizing cyber attacks, sending spam or stealing data.
How do botnets occur?
Botnets are formed when malware infects individual computers. Malicious actors usually carry out the initial attack through emails containing malicious links or attachments.
What are the dangers of botnets?
Botnets can use infected computers to launch DDoS attacks, spam emails, data theft and other malicious activities. This can lead to widespread security breaches and serious data loss.
How to detect botnet attacks?
Botnet attacks are difficult to detect because their activity is often similar to normal network traffic. Symptoms such as a sudden increase in bandwidth usage, suspicious network activity, etc. may indicate the presence of a botnet.
How to protect against botnets?
To protect against botnet attacks, up to date antivirus software should be used, operating systems and applications should be regularly updated, strong passwords should be used, and firewalls and intrusion prevention systems should be effectively configured for network security.







