Currently Empty: $0.00
Information Collection with Recon-Ng: A Step-by-Step Guide

In the world of cyber security, information gathering is the basis for a successful attack or defence. Recon stands out as a powerful tool in this field. This open source intelligence (OSINT) framework allows security professionals to gather comprehensive information about target systems. Pre-installed on popular security distributions such as Kali Linux, Recon can be used in conjunction with other tools such as Nmap and Wireshark to provide an effective discovery process.
In this article, we will cover the step-by-step use of Recon-ng, starting from its installation. We will examine how to make API integrations through the tool and how to use resources such as Shodan and Google Dorks. We will also show how Recon-ng can be used in conjunction with complementary tools such as theHarvester and Burp Suite. This guide aims to teach security professionals and enthusiasts effective information gathering techniques with Recon.
What is Recon-ng and Why is it Used?
It is an open source information gathering framework. This powerful tool allows to collect and analyse data about targets. Thanks to its modular structure, it provides access to various information sources and automates the information gathering process of users. It has an interface similar to the msfconsole application of the Metasploit framework.
Key Features of Recon-ng
- Modular Structure: Customisable according to users’ needs.
- Data Collection: Collects information from various sources.
- Automatic Association: Makes connections between data.
- Data Analysis: Analyses the collected data.
- Reporting: Presents results in shareable reports.
Importance in the Information Collection Process
Centralises the process of collecting information in open networks. It combines and analyses data from different sources on a single platform. This feature enables security experts to obtain comprehensive information about target systems. It also helps to quickly detect critical connections thanks to its automatic association feature.
Recon-ng Installation and Configuration
It is a powerful web discovery framework written in Python language. The installation and configuration process is quite simple.
Installation in Kali Linux
To install Recon on Kali Linux, open the terminal and run the following command:
sudo apt install recon-ng
This command automatically installs Recon and the required dependencies. When the installation is complete, Recon is ready for use.
Basic Commands and Usage
To start it, the following command is used in the terminal:
recon-ng

Basic commands:
-w(workspaces): Create/install a workspace-r: Loading commands from source file-h(help): Display the help menu
Module utilisation:
use: Module selectionset: Setting module optionsrun: Running the module
Recon has an interface similar to the Metasploit Framework, which facilitates the learning process. Thanks to its modular structure, users can customise it according to their needs and access various information sources.
Information Collection Techniques with Recon-ng
It is a powerful framework designed for web-based discovery and information gathering. Equipped with independent modules and database interaction, this tool provides a comprehensive environment for conducting open source web-based discovery operations. It offers various modules for cyber security experts and information gathering professionals.
Using Modules
Recon’s modular structure allows users to analyse target networks, individuals and social media profiles. The basic commands for using the modules are:
search: To search for modulesload: To install a module (load modül_adı)use: To select a module (use modül_adı)show options: To display the options for the selected moduleset: To define optionskeys add: To add APIs of various applications
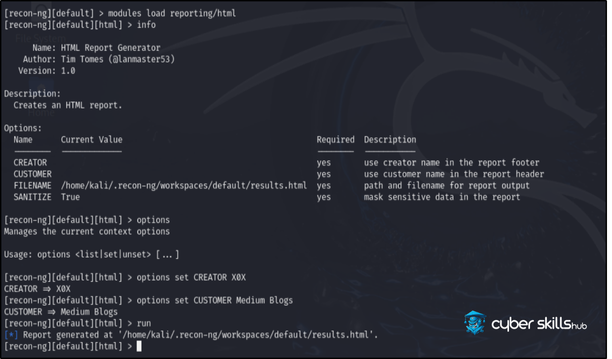
Data Analysis and Reporting
Recon provides powerful tools for analysing and reporting the collected data. An example report generation process:
recon-ng > load reporting/html_report
recon-ng [html_report] > set COMPANY CyberSkillsHub
recon-ng [html_report] > set FILENAME /var/www/cyberskillshub.html
recon-ng [html_report] > run
This process generates a comprehensive report on identified targets and helps to identify potential threats.
Conclusion
It has an important place in the information gathering process of cyber security experts. The modular structure and wide range of features of this powerful tool allow for comprehensive data collection on target systems. Its easy-to-use interface and compatibility with other tools make Recon an effective reconnaissance tool.
As a result, Recon-ng plays an important role in the field of cyber security. This tool helps security professionals identify potential vulnerabilities and develop defence strategies. The correct use of Recon-ng ensures that organisations are prepared for cyber threats and strengthens their overall security posture.
Frequently Asked Questions About Recon-ng
What is Recon-ng and what does it do?
It is a tool that helps us gather various intelligence information about a targeted website. This tool allows us to discover the target site’s subdomains, IP addresses and databases containing potential vulnerabilities. It also includes more than 100 different modules; however, these modules do not come initially installed.
What are the methods used for passive information collection?
Passive information collection is a process that is usually carried out without direct interaction with the target. These methods include reviewing WHOIS records, NETCRAFT tools, the SHODAN search engine, various archive sites, general search engines, location tracking tools such as CREEPY, THEHARVESTER email and domain information collection tool, and various career sites.







