Currently Empty: $0.00

Could prompt injection be one of the most obscure ways of a cyber attack?
Prompt injection attacks aim to bypass security filters by pushing logical boundaries. Attackers can use this method to intercept sensitive data.
Improved language models may in fact be vulnerable to unforeseen weaknesses. Promt injection refers to the abuse of these weaknesses.
Prompt Injection Basics
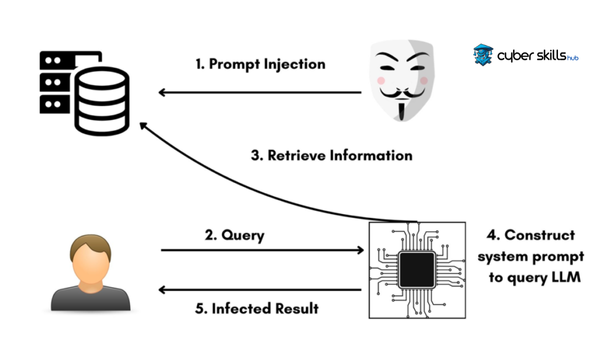
Prompt injection is a type of cyber attack that manipulates language processing models (LLMs) through specially crafted inputs, enabling the model to ignore previous commands or perform unwanted actions. From a cybersecurity perspective, these attacks can lead to leakage of sensitive information, unauthorized access or other security breaches. For example, an attacker could obtain unwanted information by using certain words or phrase patterns that could be caught by filters, causing the model not to recognize content as restricted or prohibited.
Description and Mechanism of Operation
Prompt Injection is a cyber attack method that allows language processing models to be manipulated with inputs. It can change the normal functioning of the model with specially prepared commands. These methods can cause the model to bypass its filters or exhibit unpredictable behavior.
Cybercriminals breach systems’ firewalls by detecting and exploiting vulnerabilities in the model’s tokenization and encoding mechanisms. These vulnerabilities can trick the model into taking actions such as disclosing sensitive information or showing prohibited content.
Prompt injection is a vulnerability that humans, not bots, find and exploit.
The attack is carried out through tailored requests (prompts) to push models to respond in a misleading context. This can lead to security breaches, such as leaking unwanted information or performing unauthorized operations. A well-designed prompt injection attack can be so realistic that even models cannot recognize it.
Place and Importance in Cyber Security
Prompt injection threatens one of the key components of a cyber defense system, namely language processing models. Such attacks offer important clues on how cybersecurity strategies will evolve.
- Ensuring Security: It is imperative to develop resistance to prompt injection to protect systems and data.
- Risk Prediction: Prediction of cyber attacks and understanding of potential threat vectors should be ensured.
- Sensitivity Reduction: It is necessary to determine methods to minimize the sensitivity of the systems and applications it may affect.
- Reacting: It is essential to have an effective and fast response mechanism in the event of an attack.
Anti-prompt injection measures should be at the center of a constantly updated security approach.
These attacks require cybersecurity professionals to be constantly vigilant and strengthen defense mechanisms.
Cybersecurity experts play an important role in the fight against Prompt injection attacks. For more information about cyber security expertise, you can check out our article titled‘What is Cyber Security Expertise?

Prompt Injection Threat Scenarios
Prompt injection attacks can manipulate data provided by users or systems, causing a trusted language processing model to perform unwanted or harmful actions. For example, an attacker could present carefully crafted instructions that cause the model to disclose sensitive information by circumventing censorship mechanisms. They could also use misleading context or tokens to cause systems to execute illegitimate commands. The prompt injection threat also comes into play when they override accepted instructions or disrupt real-time data flow. In this context, cybersecurity professionals need continuous monitoring and revision of security policies to quickly detect and prevent such behavior.
Causing Sensitive Data Leaks
Prompt injection attacks can breach cybersecurity privacy and lead to serious data leaks. Bypassing filters with skillfully designed prompts exposes sensitive data.
- Model Distortion: Manipulating the language processing capabilities of the model to reveal hidden data.
- Bypassing Filters: Disable content filters using specific language patterns or tokens.
- Misleading Context Usage: Obtaining sensitive data such as user credentials by misleading the model.
- Tokenization Vulnerabilities: Exploitation of vulnerabilities in LLM’s tokenization mechanisms.
Input validation and sanitization are essential to protect sensitive information.
Cybersecurity strategies must be alert to such threats and continuously evolve.
Unauthorized Access by Bypassing Filters
Cyber attackers use prompt injection tactics to bypass system filters. This can disable security mechanisms, leading to unauthorized access.
- Using Language Patterns: Overcoming filters with unique language patterns that the system cannot recognize.
- Token Manipulation: Misleading system filters using special tokens.
- Text Encodings: Bypassing system security measures using different text encodings.
Unauthorized access poses a serious threat, especially to internal networks and sensitive data.
Detailed log records must be kept and analyzed to detect and prevent attacks.
You can access sample LLM prompt injections from the link below: Sample Prompt Injection Attacks. These examples will help you better understand how prompt injection attacks work.
Detection and Prevention of Attacks
Proactive detection and prevention of prompt injection attacks requires the use of customized input authentication mechanisms and context-aware filtering systems. Cybersecurity professionals should be aware that despite the limited nature of LLM and predefined constraints, it can be vulnerable to manipulation attempts by attackers. Therefore, it is important to continuously analyze inputs, detect anomalies and dynamically adapt security policies.
For an effective defense, it is vital to train and update the LLM so that it has a better understanding of malicious inputs and edge scenarios. In addition, continuous monitoring of LLM interactions is a fundamental requirement to be able to detect and analyze potential prompt injection attempts. Such analysis plays a critical role in countering similar threats in the future.
Prompt injection attacks can be used to infiltrate spyware. For ways to protect yourself, read’Spyware:The Best 2024 Guide and Ways to Protect Yourself‘ article.
Secure Input Validation Methods
Input validation is the foundation of system security and is critical to preventing attacks such as command injection. User-supplied input to systems must be carefully validated and sanitized. These processes help to prevent the infiltration of malicious and manipulative commands.
Strict type validation of user input is the first step in minimizing potential threats. Checking the validity of input in terms of data type and expected format is vital to filter out ambiguous or harmful content. All user input must pass these checks and reject unexpected data structures.
A comprehensive and layered security approach provides extra protection against advanced prompt injection attacks. In particular, this approach should include multiple layers of security, such as input validation, type conversion, and character escape operations. In addition to security filters, the application of security rules specific to user inputs offers effective protection.
Understanding attack vectors is essential for designing the right security measures. It is important to be alert to malicious users’ attempts to bypass filters using different coding methods and language constructs. Developing security mechanisms that are dynamically updated and evolved against each new language pattern is an effective defense against such attacks.
Finally, secure input validation techniques should be integrated with the appropriate logging system. Any input validation needs to be monitored and logged in order to quickly detect and respond to potential security breaches. These records provide valuable information for configuring defenses against future threats.
Advanced cyber-attack methods such as prompt injection increase the importance of information security. For basic information and tips on this topic, see ‘ What is Information Security? Basics and Tips ‘ you can review our article.
Content Awareness and Filtering Techniques
In evolving artificial intelligence systems, the depth of meaning and content of inputs are of great importance. Therefore, security filters should analyze these elements correctly. The input structure, which is vulnerable to abuse by users, should be subjected to a detailed syntax analysis.
Filtering mechanisms must be constantly updated. The system should have a structure that constantly learns and evolves the language.
Especially in multi-layered security architectures, filters need to have individual sensitivity levels for each input. Using machine learning-based models, atypical malicious inputs or harmful content should be identified and blocked. This prevents malicious attempts from starting.
Ultimately, advanced language processing technologies are critical for semantic richness and accurate understanding of context. These technologies must be capable of interpreting text and inferring context, further strengthening the detection of sensitive content and intentions to prevent misuse of algorithms. Context awareness is indispensable for understanding and blocking modern threats faced by filters.
Best Practices and Strategies
First of all, it is essential to effectively validate and sanitize user-submitted prompts to protect against any prompt injection attempts. Robust input validation and sanitization protocols based specifically on user input should be adopted to increase the resilience of the system against potential manipulation. Security mechanisms based on machine learning should be continuously updated by feeding and training them with threat databases. This enables the algorithm to better understand and detect malicious inputs and edge cases. Furthermore, monitoring and logging prompt injection attempts is vital for detecting and analyzing attempts.
Large Language Model (LLM) Security Updates
Continuously updated and adapted protection mechanisms are vital for the security of LLMs. In this context, effective firewalls and sensitive data detection systems serve as the primary line of defense against damaging attempts; these systems are critical to prevent threats and minimize damaging interactions.
Being prepared for new threat vectors is a priority factor in LLM security strategies. In this context, the update protocols deployed provide a systematic response to this dynamic need.
Increasing technological advances require security protocols to be re-evaluated and improved. It is critical to increase the effectiveness of the developed algorithms against evolving attack methods, including prompt injection attacks.
The development of mechanisms to detect and censor sensitive content is essential to protect against the damaging effects of user input. These mechanisms should play an active role in preventing data breaches and unauthorized access by increasing the capacity to detect harmful content.
Continuous review and updating of LLMs by teams of experts in the field is a pioneering step towards minimizing security vulnerabilities. In this way, any weak points can be quickly detected and necessary arrangements can be made in line with security protocols.
Finally, the use of benchmarking and analytical techniques is crucial to improve the detection of cyber threats such as prompt injection. With these techniques, the threats faced by systems can be detected immediately and appropriate interventions can be carried out on a regular basis.
Effective Logging and Monitoring Systems
In cyber security, effective logging and monitoring systems play a vital role in detecting and analyzing possible attacks. In the fight against attacks such as Prompt injection, it is important that logs contain detailed and meaningful information. With these logs, experts can identify attack patterns and improve system security.
An effective monitoring infrastructure is an integrated part of complex systems that enable fast and accurate responses to cyber security threats. Log records systematically record events such as user activities, system errors and security breaches. This information is a critical factor in detecting and preventing prompt injection attempts and allows in-depth analysis of security vulnerabilities.
Advanced monitoring systems use advanced algorithms and AI-powered analytical tools to detect attack vectors in real-time. Detecting anomalous behavior is essential to maintain system health and be proactive against security breaches. These systems can prevent unexpected situations by constantly monitoring network traffic and user behavior.
Ultimately, implementing comprehensive logging and monitoring policies strengthens organizations’ cybersecurity defense capacity. These systems, which increase resistance to various cyber threats, including Prompt injection, enable early detection of data breaches and immediate response to incidents. Monitoring and logging solutions that minimize potential damages and protect the security posture of organizations are of strategic importance.
Frequently Asked Questions About Prompt Injection
Prompt injection nedir?
Prompt injection is a type of cyber-attack where language processing models (such as LLMs) are manipulated with inputs, resulting in the execution of unwanted or malicious actions. This attack can lead to leakage or unauthorized access to particularly sensitive information.
How do Prompt injection attacks work?
Cyber attackers mislead language processing models through specially crafted commands (prompts). These commands disrupt the normal functioning of the model, making it possible to access sensitive data or perform unauthorized operations without filters.
How can we protect against Prompt injection attacks?
Safeguards include strong input validation protocols, constantly updated firewalls and detailed log records. In addition, continuous training and security updates for LLMs can be effective in preventing such attacks.
Is it possible to detect prompt injection attacks?
Yes, it is possible to detect prompt injection attacks. Methods include detailed logs, anomalous behavior analysis and continuous system monitoring. These methods enable early intervention by identifying attack patterns.
What is the place of prompt injection in cyber security?
Prompt injection poses a serious threat, especially in systems using language processing models. This type of attack contributes to the evolution of cybersecurity strategies and requires constant updating of defense mechanisms. Cybersecurity professionals must constantly update their knowledge and skills and be vigilant against these new threats.







