Currently Empty: $0.00

Log4j vulnerability created a major crisis in the cyber world. Most IT professionals had to contend with this critical Apache vulnerability, known as cve-2021-44228, which created a broad attack vector as the year drew to a close.
Penetration testing plays a critical role in detecting such vulnerabilities at an early stage. Cyber security experts regularly perform penetration tests to evaluate attack vectors and identify potential vulnerabilities in systems. These tests simulate real-world attack scenarios and evaluate the security level of systems and defence mechanisms against vulnerabilities.
One morning, the administrator of a large e-commerce site realised that user data had been exposed by an attacker gaining unauthorised access via LDAP. This vulnerability, which affected millions of systems worldwide, posed a serious threat to companies using the Log4j library in their systems. This rapidly spreading problem attracted the attention of cyber security experts and intensive solutions were sought.
What is Log4j?
Log4j is a logging library widely used in Java-based applications. Developed by the Apache Software Foundation, this library allows application developers to monitor and debug their applications. Basically, by recording events that occur in the software, it allows developers to understand system behaviour and detect problems.
This library is very popular as it has been used in various projects for many years and offers a number of advanced features. It meets the needs of developers with its flexible structure and configuration options. However, this widespread use also has the potential to pose a great risk if vulnerabilities such as cve-2021-44228 occur. In recent years, especially the vulnerability called Log4Shell has once again emphasised the security importance of this library.
Features of Log4j
Log4j offers highly efficient logging capabilities as well as being widely used in Java-based applications. Thanks to detailed logging, it is possible to monitor system behaviour and diagnose problems.
This library provides developers with flexible configuration options. For example, it supports configurations in XML or JSON formats, which offers a great advantage in terms of adaptability.
Log4j is a scalable logging solution and enables effective use in large-scale systems.
Another prominent feature is that Log4j can perform asynchronous logging. In this way, it can handle high processing loads with minimal impact on system performance. It also offers detailed control with various log level (DEBUG, INFO, WARN, ERROR) configurations.
Common Areas of Use
Log4j is widely used in various industries and applications. The main reasons for this are flexibility and performance advantages.
- Web applications: Log4j is used to monitor errors and events that occur on the server side.
- Enterprise software: Plays an important role in tracking business processes and error management.
- Big data analysis platforms: Fulfils logging needs in systems such as Hadoop and Spark.
- Mobile applications: Can be integrated to manage event recording in Android applications.
- Game engines: Used for error and performance monitoring on platforms such as Unity or Unreal Engine.
Log4j offers different configuration options, making it suitable for various application requirements.
Furthermore, the scalable nature of this library provides an efficient solution for large-scale systems.
It allows developers to perform high-volume logging with minimal impact on system performance.
Log4j Vulnerability
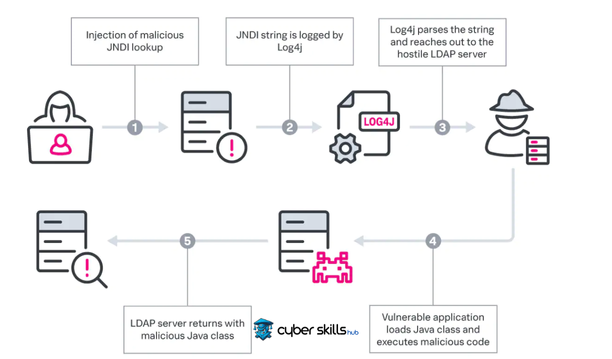
Log4j Vulnerability is a vulnerability in the widely used Log4j library. This vulnerability is a critical security issue that allows attackers to execute arbitrary code. In particular, it occurs by manipulating JNDI (Java Naming and Directory Interface) and LDAP references.
This log4j vulnerability can compromise software systems used in many industries and needs to be addressed quickly. It is vital to protect systems by applying updates and security patches.
Vulnerability Definition
Log4j Vulnerability is a vulnerability in the Apache Log4j library. This vulnerability can put systems under serious threats.
- Random Code Execution: Malicious actors may find the opportunity to execute code remotely.
- JNDI Abuse: The attack involves inserting malicious references via JNDI.
- Wide Dissemination Capacity: Can affect a large number of systems.
- Vulnerability Score: It received a high score on CVSS (Common Vulnerability Scoring System).
It is possible for attackers to carry out malicious activities using this vulnerability.
It is therefore important for system administrators to apply security patches immediately.
For more information about ransomware and other cyber threats, see ‘Ransomware: How to Protect Against Cyber Threats’ article.

How is it Exploited?
The Log4j vulnerability can be exploited by attackers as a remote code execution (RCE) vulnerability.
Malicious people can send malicious commands via JNDI and LDAP references.
This allows attackers to gain control of the target system.
Attackers can easily exploit the vulnerability by sending malicious payloads over common protocols, especially HTTP requests. This technique works through user logins, log files and other text fields to execute malicious JNDI references. In this way, malicious attacks can be carried out and data security can be compromised.
Safety Precautions
A number of proactive measures should be taken to protect systems against Log4j vulnerability. These measures are critical to minimise the risk of the vulnerability being exploited.
Firstly, it is necessary to regularly apply security patches and updates. In this way, existing vulnerabilities are closed and the entry points of attackers are minimised.
Furthermore, the protection of the system should be strengthened by using “network segmentation” and “fire walls”.
Updates and Patch Management
Updates and patch management are the cornerstone of cyber security. Especially when it comes to critical vulnerabilities such as Log4j, this issue becomes even more important.
For information about current cyber security standards and certifications, you can visit our ‘Best Cyber Security Certificates’ page.
The Apache Log4j vulnerability, known as cve-2021-44228, which emerged in 2021, has caused great repercussions around the world. Closing such vulnerabilities quickly plays a vital role in ensuring the security of systems. Applying security patches quickly eliminates threats at an early stage.
Updates and patches should be applied on a regular schedule. By using automatic updates and patch management tools, delays caused by human error can be minimised. This process should be supported by continuous monitoring and reporting.
When vulnerabilities such as Log4j occur, it is imperative that security patches released by manufacturers are integrated into systems without delay. It should also be noted that third-party software should be checked regularly and relevant updates should be applied.
Finally, in the framework of updates and patch management, tools that continuously scan for vulnerabilities should be used. This ensures that systems remain up-to-date and secure.
Monitoring and Detection Methods
Detecting vulnerabilities such as the Log4j vulnerability is possible by using powerful monitoring and detection methods. These methods are critical for detecting and preventing security vulnerabilities.
Security information and event management (SIEM) solutions play an active role in this process. It detects unusual activities by continuously monitoring log files.
Machine learning-based monitoring tools can also be used to identify anomalies. These tools detect deviations by learning normal behaviour patterns.
For more information on the tools used to automatically detect cyber threats, see ‘Threat Intelligence Tools: Best Tools and How to Use Them’ for more information.
In addition, suspicious network activities can be quickly detected with network traffic analysis (NTA). NTA analyses network traffic in depth.
Regular updating of vulnerability databases is also essential in the monitoring and detection process. This ensures protection by keeping system drivers and definitions up to date.
Finally, it is important to continuously check systems with vulnerability scanners. These scanners automatically detect and report known vulnerabilities.
Emergency Response
When emergency response is required, the capacity to respond quickly and effectively is critical. Having predefined procedures for the relevant security team minimises the impact of the vulnerability. When a vulnerability is identified, patches should be deployed immediately to limit the extent of damage and prevent wider attacks. In addition, a thorough investigation of the incident should be carried out and necessary remediation arrangements should be made to prevent similar threats in the future. This process will strengthen the overall information security posture of the organisation.
Immediate actions to be taken
When a Log4j vulnerability is detected, a rapid and systematic response is critical.
- Apply log4j updates: Install the latest Log4j version on all systems affected by the vulnerability.
- Review all systems: Analyse your network traffic and system logs to identify potentially affected systems.
- Update security patches: Close vulnerabilities by updating existing security patches immediately.
- Carry out cancellation and renewal processes: Revoke the permissions of the affected systems and perform the necessary renewals.
- Use security monitoring tools: Stay alert to new threats by continuously monitoring your systems.These steps will help minimise the impact of vulnerability and improve your system security.Ensure that procedures are followed correctly as each step is performed.These processes require an integrated approach where the entire organisation, not just the technical teams, work in concert.
Long Term Solutions
Long-term solutions are of great importance for strengthening the security infrastructure for organisations.
Firstly, the most common long-term solution is to implement a strict security management policy and software lifecycle management. In this context, regular review and implementation of security controls and software updates is critical.
Secondly, it is necessary to raise the awareness of personnel through regular cyber security trainings. These trainings enable employees to respond immediately to potential security threats, thus minimising the impact of vulnerabilities.
Finally, investments should be made in intrusion detection and prevention systems (IPS/IDS). These systems can proactively detect and prevent potential attacks, thus strengthening the security position of the organisation. In addition, continuous updating and management of these systems is essential to close security gaps.
For more information, you can visit the Apache Log4j Vulnerability Information page.
Frequently Asked Questions about Log4j
What does Log4j do?
Log4j is a logging library frequently used by those who develop software with Java programming language. It is used to keep a record of errors and events that occur in applications. With this library, software developers can more easily detect errors in their systems and produce solutions. Log4j is also very useful for analysing and improving the performance of the application. Thanks to the flexibility and configuration capabilities offered by Log4j, developers can keep log records in different formats and levels, and transfer these records to files, databases or remote servers when necessary. The library allows detailed error reports to be generated and analysed. In this way, potential problems that may occur in applications can be predicted and measures can be taken in advance, which increases the reliability of the software. For programmers, using Log4j makes development more efficient and manageable.
What is a LogJam vulnerability?
The LogJam vulnerability is a vulnerability in systems using the Diffie-Hellman key exchange protocol that allows attackers to compromise secure communications by forcing a weak cryptographic key negotiation. Diffie-Hellman key exchange is used to enable two parties to establish a secure key without a previously shared secret. However, this protocol works on a specific group basis and is vulnerable to security weaknesses when using weak group parameters. The LogJam attack targets this weakness. By forcing the 512-bit key exchanges used in the TLS/SSL protocol, the attacker can perform a Man-in-the-Middle (MitM) attack to break the key exchange. The 512-bit key is weak enough to be easily broken. This allows an attacker to eavesdrop on and modify seemingly secure communications. LogJam poses a major threat, especially for systems using key lengths less than 1024-bit. To address this vulnerability, it is recommended to use stronger key lengths of 2048-bit or higher. In addition, the vulnerability can be remediated by applying software updates and security patches.
When did Log4j come out?
Apache Log4j was first released in 1999. This software library is designed to facilitate logging in applications written in Java. Log4j is an open source project developed by the Apache Software Foundation. Since its first release, it has attracted great interest from developers and has been widely used. Over the years, it has been updated several times. Log4j, which attracts attention especially with its extensible and flexible structure, has been made even more powerful with important updates and improvements over time. It is still actively used and developed today. The vulnerability discovered in 2021 once again revealed the importance of Log4j. This vulnerability caused a great echo in the cyber security world and was tried to be closed with urgent updates. Apache is constantly releasing new versions and patches to address such security issues.
What is Log4j Exploit?
Log4j Exploit is a critical vulnerability in the Apache Log4j library. This vulnerability allows remote code execution (RCE) attacks. This vulnerability has emerged especially in 2.x versions of Log4j and has been rapidly exploited by hackers. This vulnerability in the system allows cyber attackers to execute commands on target systems. The effects of the Log4j Exploit will continue to be felt in the cyber security world for a long time.







