Currently Empty: $0.00

When a company’s headquarters is attacked, everyone’s first thought is about software vulnerabilities.
This is in line with the idea that software is the brain of the device; taking control means total control over the device.
However, while the cost of ensuring software security is low, the situation is more complex in the area of hardware security.
What is Hardware Hacking?
Hardware hacking is a method of attack that exploits vulnerabilities in the physical components of a device. Unlike software hacking, hardware hacking requires the attacker to have physical and usually uninterrupted access to the target device. Such attacks can be carried out using hardware, software, or a combination of both, depending on the identification of the target.
Cybercriminals target hardware because it is generally less resilient than software. It’s also important to consider that a device model doesn’t change over the years; for example, Xbox consoles don’t get hardware upgrades after they are released.
Understanding Physical Vulnerabilities
Hardware vulnerabilities are digital gateways for cyber threat actors; flaws in the physical components of devices are exploited for attacks.
Hardware security patches do not occur as frequently as in software, which leads to vulnerabilities existing for longer periods of time.
The stringent security measures in the design and manufacture of devices can, over time, become ineffective in real-world scenarios. Fixed hardware architectures in particular can become more vulnerable to certain attack methods.
These vulnerabilities to physical components may not be tested in anticipated out of use scenarios – making them difficult for cybersecurity professionals to detect in advance and making risks harder to manage.
For more information on how to detect such physical vulnerabilities, see our article on How to Succeed in Forensic Expert Training.
Differences between Hardware and Software
Hardware represents the physical components of a computer; software represents the instructions executed by these components. Hardware is fixed and visible, while software is intangible and variable.
While software can be easily reconfigured to fix bugs and updated, replacing or upgrading hardware is more complex and often requires physical intervention. Software is frequently updated with security patches.
While software can be distributed and managed over a wide network, hardware security often relies on physical access. This distinction means that the nature of the threat vectors and the measures that need to be taken against attacks are also different.
While software attacks can be carried out remotely and often anonymously, hardware attacks are inherently riskier as they require physical access and direct interaction with the device. The attacker needs material means to bypass the security measures of the target hardware.
As a result, for the holistic security of a system, it is essential to keep the security levels of both hardware and software at a high level. The interaction between both components has a direct impact on the vulnerability of the system.
If you want to learn how software attacks are carried out, check out Cyber Attack Examples: Which Types are Dangerous?
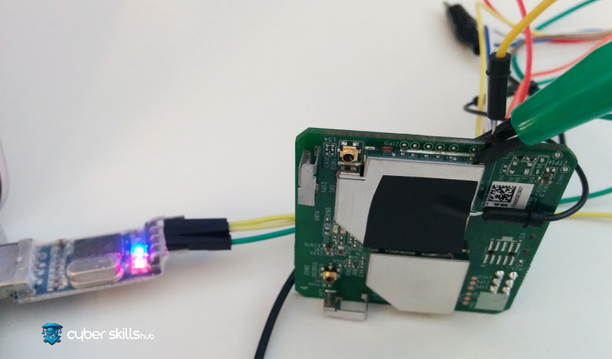
Hardware Hacking Methods
Attackers targeting hardware typically use a variety of methods to manipulate or damage physical components. However, other methods are often used to hack hardware, such as extracting memory remnants, patching the circuit board or JTAG ports, replacing components, recording and analyzing digital signals with logic analyzers, or side-channel attacks. By following the device’s behavior patterns, an attacker can discover vulnerabilities and gain access to sensitive data or abuse the functionality of the hardware.
Fault Injection Process
Fault injection is a method of introducing vulnerabilities by applying stress to hardware components. This triggers malfunctioning of the target device’s protective mechanisms and gives the attacker an opportunity for exploitation.
- CPU Overloading (Overclocking): Pushing a processor beyond its normal operating limits can cause errors in response time or data flow.
- DRAM Hammering: Continuous signaling of memory cells to leak data from memory.
- GPU Undervolting: Layers of security can be bypassed by reducing the graphics processor to an unstable state.
- Short Circuiting: Hardware failures are created by deliberately short-circuiting the device circuits and these situations are exploited. The device exposed to this attack remains unprotected for a certain period of time and becomes vulnerable to the attacker. Using this method, the attacker can trigger a system reset, bypass protocols or steal sensitive data.
Side Channel Attacks
Side-channel attacks exploit the processing characteristics of the hardware.
These attacks are based on indirect information arising from the physical operation of the device. For example, the amount of power consumed by the device when performing a certain operation can be evaluated through various indirect channels, such as the program’s execution time or acoustic feedback from faulty operations. By analyzing this data, the attacker tries to estimate the value or type of data the device is processing.
Attacks are carried out subtly and silently.
This involves analyzing the data generated during the normal functioning of the device, rather than physically damaging the hardware. Attackers can obtain critical information by monitoring power consumption, electromagnetic emissions or processor timings of target systems.
Side channel attacks require a high level of expertise and in-depth technical knowledge of devices. To combat such attacks, it is imperative that device designers and software developers integrate security measures at the hardware and firmware levels. Ultimately, increasing resilience to side-channel attacks is essential to create a secure hardware ecosystem.
Techniques to Overcome Hardware Security
Hardware compromise is the process of identifying and exploiting weaknesses in the physical components of devices. In this process, an attacker can exploit hardware design flaws, insecure components or flaws in protection mechanisms. In particular, techniques such as fault injection and side-channel attacks can cause devices to react in unexpected ways, which can be used as a vector to steal sensitive data.
The methods used to bypass the firewalls of a piece of hardware often require the attacker to gain direct physical access to the device. These methods, ranging from simple JTAG interface penetration to the use of a complex logic analyzer, allow access to user information, cryptographic keys or other critical data. Hardware compromise techniques not only exploit existing vulnerabilities, but also contribute to making future versions of devices more secure by finding these vulnerabilities and exposing security holes in systems.
If you’d like to learn how to bypass firewalls, check out our article Here’s What You Need to Know About Penetest.
Circuit Board Intervention
One of the processes of hardware hacking is to directly interfere with the circuit board. Attackers need to physically open the device and interact with the internal components.
- Opening the Device: The first step is to carefully open the device and access the circuit board without damaging it.
- Circuit Mapping: By analyzing and mapping the components and paths on the circuit board, suitable points for attack are identified.
- Connecting External Modules: External modules such as Raspberry Pi are connected to the specified points to control or communicate on the device.
- JTAG Port Access: Using the JTAG port, vulnerabilities are detected by making it possible to program or debug components such as the CPU on the circuit board. These methods of intervention are used to interfere with the original functioning of the device. Hardware hacking represents a critical area where physical intervention can lead to sensitive data leaks. Attackers often need sophisticated tools and deep technical knowledge to carry out these processes.

Hacking with Component Modification
Component replacement is a common and effective method of hardware compromise. This process involves replacing original components with counterfeit or generic ones. Such a modification can allow the device’s security protocols to be circumvented.
Unauthorized component modifications are usually done with the aim of penetrating the system by bypassing the dongle. This targets vulnerable points of the device.
Device manufacturers often develop systems compatible with custom firmware or hardware components. However, these systems can sometimes work with counterfeit components.
Deviation of hardware from factory settings can lead to unwanted interactions with the system and create security vulnerabilities. Hackers can exploit these vulnerabilities by using non-genuine components to find them.
For example, Nintendo Switch modifications can be accomplished through the use of counterfeit components. Such modifications expose security vulnerabilities.
Consequently, one of the ways to compromise the hardware security of the device is through unauthorized component modification. This method disrupts the original functioning of the device, allowing attackers to gain access to it.
In addition to physical vulnerabilities, you can learn about zero-day vulnerabilities in our article titled What is Zeroday and How Can You Be Protected?
Extracting Memory Dumps
Memory dump extraction is the process of copying data from the physical memory of hardware. Attackers copy the RAM contents of devices to create a snapshot of memory. This is usually accomplished using cold boot attacks or memory dump tools. Thus, passwords, encryption keys and other sensitive data can be compromised.
This method poses a critical threat, especially on devices that store encrypted data. Attackers can intercept the encrypted data in the device memory in unencrypted form, rendering firewalls meaningless. This poses a serious risk to data security.
Using the JTAG Port
The JTAG port is an interface used for hardware debugging and programming. It is commonly found in computer systems and other electronic devices. This port is designed for direct control of chipsets and circuits, so it is critical in hardware debugging efforts.
Attackers can use the JTAG port to dump the firmware of the device. This means radical analysis of security and can give attackers serious advantages.
The JTAG port, which is used especially during the testing and programming of integrated circuits, provides an opportunity for an attacker to gain deep access to the inner workings of the device. Although the security of these interfaces has improved with advancing technology, experienced attackers can use these ports for malicious purposes. For example, they can bypass security measures, steal debugging information, or gain root access.
Attacks using JTAG are highly technical and sophisticated operations. By enabling the device’s debug mode, attackers create the conditions for data dumping from memory. Once such access is gained, the attacker can extract the device’s firmware, identify potential vulnerabilities and exploit them to gain full control over the device. When such an attack is successful, the security measures of the device manufacturers are overridden and full access to the full functionality of these devices is gained.
Monitoring with Logic Analyzer
Logic analyzers are tools that record and analyze digital signals. They are particularly effective in identifying errors in their operation. Therefore, they also play an important role in hardware hacking processes.
These tools allow attackers to connect to the debugging interface of the target device and monitor the data being transmitted. During the tracing process, it is possible to monitor the flow of data through the circuit elements through which the signals travel. System elements such as the bootloader or kernel logs that become accessible can then be analyzed.
Monitoring with Logic Analyzer provides attackers with the opportunity to detect vulnerabilities in device firmware and gain backdoor access through these vulnerabilities. This access can then be used for unauthorized software installations or the theft of sensitive data.
For a hacker, attacks using a Logic Analyzer are relatively uncommon but highly effective. This method is particularly dangerous in systems with less complex security measures, such as IoT devices.
The fact that hardware security is so sensitive makes the use of tools such as Logic Analyzers even more important. Security professionals should therefore be informed on how to make their device security more resilient to such attacks.
If you want in-depth information and training on other cyber security topics, you can visit our CyberSkillsHub Cyber Security Courses page to review our courses.
Frequently Asked Questions About Hardware Hacking
What is hardware hacking?
Hardware hacking is the process of discovering and exploiting vulnerabilities by physically accessing the physical components of a device. Such attacks exploit weaknesses in hardware and software.
Why is it harder to secure hardware than software?
Hardware security is complex and difficult because it requires physical access and hardware patching is not as frequent as software. It is also more difficult to close vulnerabilities because hardware components are often used unchanged for long periods of time.
What is Fault Injection?
Fault injection is the process of creating security vulnerabilities by intentionally introducing errors or stresses into hardware components. This process allows attackers to exploit the device’s protective mechanisms.
How do side channel attacks work?
Side-channel attacks exploit the physical processing characteristics of the hardware to indirectly exfiltrate information. Attackers can access sensitive information by analyzing characteristics of the device such as power consumption, processing time, etc.
What are the common ways to bypass hardware security?
Hardware compromise methods include JTAG port access, circuit board tampering, component modification and the use of logic analyzers. These methods require direct interference with the physical components of the device.
How to extract memory dumps?
Memory dumping is performed by copying data from the hardware’s physical memory, usually using cold boot attacks or specialized memory dumping tools. This process provides access to sensitive data.
What are the risks of using the JTAG port?
Although the JTAG port is used for programming and debugging hardware, attackers can abuse this interface to gain complete control over the device and exploit vulnerabilities.
How to monitor with a logic analyzer?
Logic analyzers connect to the device’s debug interface to record and analyze the transmitted digital signals. This allows attackers to examine elements of the system and identify potential vulnerabilities.







