Currently Empty: $0.00
Encryption Techniques: Secure Your Data

Data breaches can cause millions of dollars in losses for companies.
An unprotected system becomes a target for hackers, causing both cost and reputational damage.
One of the most effective ways to protect your data is to use end-to-end encryption methods, which ensure that your sensitive information is only accessible to authorized users.
Encryption is the foundation of security.
What is Encryption?
Encryption is a security method used to protect all kinds of sensitive data from unauthorized access. The data in question is converted into an unreadable format using a specific algorithm and key. This process transforms the data into encrypted data that only authorized persons can access or decrypt, thus maintaining the confidentiality of the information.
From classical encryption approaches to modern cryptography systems, encryption techniques have evolved and developed over time. Among these, there are two main categories: symmetric and asymmetric encryption. Symmetric encryption uses the same key, while asymmetric encryption offers higher levels of security by using a pair of keys. These methods play a critical role in protecting data, especially for authentication, data integrity and confidentiality requirements.
Basic Encryption Concepts
Encryption is a critical technology for protecting sensitive data from unauthorized access. This technology secures data by making it unreadable. The encryption process consists of two basic components: the algorithm and the key.
An encryption algorithm is a collection of methods that transform data into encrypted form. The key is the unique information used to perform this transformation and decrypt the data. By using an algorithm and a key together, the security of the data is increased.
Encrypting data has been used since antiquity as a basic method of protecting information.
Encryption protects the confidentiality, integrity and availability of data. Confidentiality ensures that the message is readable only by authorized persons; integrity ensures that the data remains unchanged; and availability ensures that authorized users have accurate and timely access to your organization’s information.
Encryption Types
Encryption technology is divided into two basic types of encryption: symmetric and asymmetric. Both methods play an important role in protecting data, but their application areas and methodologies differ. Understanding this difference is critical for determining the appropriate encryption strategy.
Symmetric encryption refers to a method where the same key is used for encryption and decryption. While this is fast and efficient, it requires the key to be shared securely.
Asymmetric encryption is a method that uses two different keys (one secret and one public key) for encryption and decryption. Although slower, it is a more secure form of encryption where key management is more secure. The public key can be published to anyone, while the secret key must be kept only by the data owner.
Advanced techniques such as confusion-based encryption and diffusion-based encryption provide multi-layered security by making data difficult to analyze and decrypt. These techniques are the cornerstones of modern cryptography and have a particularly effective role in encrypting big data and multifaceted security protocols. Evolutionary algorithms and artificial intelligence-based systems play an important role in the development of such encryption techniques.
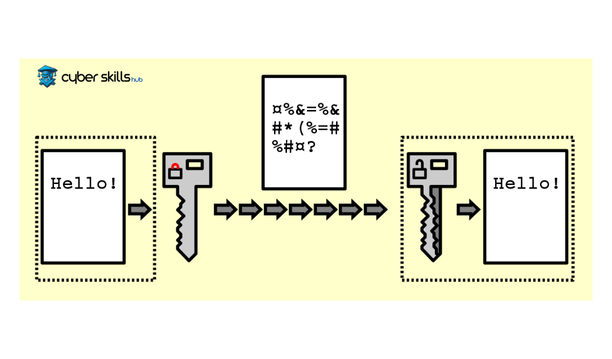
Modern Encryption Methods
In modern encryption methods, we observe the continuous development of cryptographic algorithms and protocols. For example, the AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) algorithms are now widely used cryptographic systems that provide high security. Such algorithms are designed to maximize the security of data and are the first choice for many industrial and commercial applications.
With the advent of quantum computers, interest in quantum-resistant encryption methods has increased. In this context, Post-quantum cryptography (Post-quantum cryptography) algorithms come to the forefront, and studies are being carried out on encryption systems that cannot be broken by classical computers and are developed with quantum computers in mind. For the future of security, research in this direction plays a critical role in the evolution of encryption technology.
Symmetric Key Encryption
Symmetric key encryption is a method where the same key is used for both encryption and decryption. It is one of the oldest cryptographic techniques developed to ensure data security and is highly efficient in terms of speed. However, it involves some risks as the key must be known by both parties.
In this technique, the length of the key used to increase security is critical. The longer the key, the harder it is to break.
Symmetric encryption methods can be realized with algorithms such as AES, DES (Data Encryption Standard) and 3DES (Triple DES). These algorithms use static (fixed) keys and operate on blocks of data, enabling high-speed data encryption. However, while these methods offer strong and fast solutions, they also present key management challenges.
The complexity of key management and the need to share keys securely can pose challenges that limit the use of symmetric key encryption. This is especially important in large-scale corporate networks or when exchanging information over the Internet, where the key must be shared through a secure channel. In this context, in addition to symmetric key management, additional processes and layers are added to establish additional protocols and session keys to guarantee the authenticity and integrity of encrypted data.
Asymmetric Key Encryption
Asymmetric key encryption is an encryption method that uses two different keys: one public key and one secret key. This method forms the backbone of many modern security systems and is often used in digital signatures, SSL certificates and VPN technologies. Asymmetric encryption creates a secure communication channel by securing both endpoints of the communication taking place in data security.
In this system, the public key is publicly accessible and is typically used for sending data. The secret key, on the other hand, is private only to the recipient of the message and is accessible only to the recipient. Data encrypted with the secret key can only be decrypted by the owner of the matching public key. Public-key encryption is therefore particularly well suited for situations requiring secure data transfer over the internet.
One of the most well-known examples of asymmetric key encryption is the RSA (Rivest-Shamir-Adleman) algorithm. This algorithm provides security based on the difficulty of decomposing large numbers into their prime factors. RSA is widely used in online transactions and electronic commerce. Another example is ECC (Elliptic Curve Cryptography), which offers high levels of security while requiring less processing power.
Although asymmetric encryption offers a high level of security, it is generally slower than symmetric encryption. This slowness is due to the relatively more complex mathematical operations required. For this reason, hybrid systems that combine asymmetric and symmetric encryption methods are often preferred. Hybrid systems optimally combine the advantages of both methods.
The existence of public and private keys creates innovative solutions on public key infrastructures (PKI). These infrastructures facilitate the distribution and management of digital certificates, one of the cornerstones in cybersecurity. Thus, the correct application of asymmetric encryption techniques contributes to protecting the confidentiality and integrity of communications.
Encryption Tools and Applications
Encryption is essential for data protection and can be implemented with a variety of tools. BitLocker is a widely used tool for disk encryption on Windows operating systems. By providing effective disk encryption, it creates a protective shield against unauthorized access.
Apart from proprietary software, there are also open source solutions designed for developers and system administrators, such as OpenSSL. OpenSSL enables data encryption using various encryption algorithms, digital signature creation and secure communication channels using SSL/TLS protocols.
For mobile devices, the iOS and Android operating systems offer various encryption mechanisms built-in. These include device encryption and app data isolation.

Encryption in Daily Life
Encryption protects us in the activities we do on the internet on a daily basis, such as emailing and social media interactions. Encryption is especially vital when sharing sensitive information.
Encryption is also indispensable in financial transactions such as internet banking and mobile payments. It plays a critical role for a secure trade.
The secure transmission of credit card information during online shopping and private messages sent over messaging applications is thanks to the privacy and security provided by encryption. For example, the HTTPS protocol helps protect user data by encrypting web traffic.
On the other hand, encryption is a fundamental method to ensure personal data security and increase resistance to cyber-attacks by protecting individuals’ digital identities. Encryption techniques, which are at the core of our daily communication, are considered the bastion of cybersecurity at both individual and organizational levels and have therefore become part of our security.
Encryption Software
Encryption software is an essential tool for securely storing and transmitting your data. A variety of encryption software is available for both individuals and organizations.
- BitLocker: A Windows-based tool that can encrypt the entire hard disk or partitions.
- VeraCrypt: It is an alternative to BitLocker and has a wide range of uses with cross-platform support.
- OpenSSL: Includes a cryptographic library for secure communication on the network.
- GnuPG (GPG): Used to encrypt email and files using public key encryption.
- Signal: A messaging app that offers end to end encryption.
In addition to protecting your data privacy, these tools also guarantee data integrity. They often use complex algorithms and protocols for this.
When encrypting your data, it is critical to choose the right encryption software for your needs. A good choice creates a solid line of defense against cyber threats.
Data Security Tips
In your data security strategy, don’t forget to enable strong passwords as well as two-factor authentication methods. These steps ensure that your data is protected against unauthorized access.
To make the right choice between various encryption algorithms, it is important to familiarize yourself with industry standards such as AES (Advanced Encryption Standard) and asymmetric encryption methods such as RSA and ECC (Elliptic Curve Cryptography). Make sure that the algorithms you use meet current security requirements.
Also, make sure you regularly update your software and devices to avoid any vulnerabilities. Up to date security patches significantly reduce the risk of cyber attacks.
Creating a Strong Password
Creating a strong password is one of the cornerstones of your data security. Length, complexity and unpredictability are important elements for strong passwords. To ensure that a password cannot be easily guessed and cracked, you should use complex structures by combining various types of characters.
Use both uppercase and lowercase letters in your password. This will make it harder for cyber attackers to crack your password.
Adding numbers and special characters increases the difficulty of your password. Such character combinations provide extra protection against brute-force attacks.
It is important to avoid the use of repeated or consecutive characters in data security. You should create passwords that are unique and difficult to guess.
Using a password manager you can create unique and complex passwords for different services. This ensures that you have separate and strong passwords for each account, and if one is cracked, your other accounts will remain safe.
However, the difficulty of memorizing a password should not be underestimated. By creating complex schemes that can be changed regularly and remembered, it is possible to balance security and convenience.
Two-Factor Authentication
Two-factor authentication (2FA) is a vital security measure to enhance your account security. This requires users to log in using not only something they have knowledge of (password), but also an item they physically possess (phone).
In fact, 2FA is one of the most fundamental layers of cybersecurity, protecting users against phishing, password cracking and other attacks aimed at stealing login credentials. Verifying a user’s access to information through two separate channels provides additional security against potential breaches. As a result of these efforts, user accounts are protected against remote attacks and unauthorized access, while system reliability is increased.
For example, when a user wants to log in to their e-mail account, they first enter their password. Then, a verification code is sent to their phone and they are expected to enter it into the system. This process ensures that the account is only accessible to the authorized user and protects the security of the account even if the password information is stolen.
A key advantage of 2FA is that it minimizes the damage in the event of a security breach. Even if a malicious person gets hold of your password, they will not be able to access your account without a second layer of verification. This creates an extra line of defense to protect your sensitive data. Furthermore, modern 2FA solutions are designed not to negatively impact the user experience and security can be achieved with a simple tap or confirmation.
Frequently Asked Questions about Encryption Techniques
What is encryption and how does it work?
Encryption is a security method that converts sensitive information into an unreadable form to protect data from unauthorized access. Encryption is performed using a specific algorithm and key, and only authorized users can decrypt it.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption, where the same key is used for both encryption and decryption, is fast and efficient, but the key must be shared securely. Asymmetric encryption uses two different keys (one public, one secret); although slower, key management is more secure.
What are modern encryption methods and how do they ensure security?
Modern encryption methods include algorithms such as AES and RSA. These methods are designed to securely encrypt data, and new technologies, especially quantum-resistant encryption, are being developed to meet future security needs.
How are encryption techniques used in everyday life?
Encryption techniques are used to secure data in everyday transactions such as emailing, social media interactions, internet banking and online shopping. In particular, the HTTPS protocol uses encryption for the secure transfer of information over the internet.
How to create a strong password?
To create a strong password, you should take an approach that includes length, complexity and unpredictability. By using upper and lower case letters, numbers and special characters, you should create passwords that are difficult to guess and crack.
What is two-factor authentication (2FA) and why is it important?
Two-factor authentication requires users to enter a password as well as a verification code via a physical device (usually a phone). This additional step increases account security, ensuring that accounts remain secure even if password information is stolen.







