Currently Empty: $0.00
What Does Advanced Persistent Threat (APT) Mean?

APT, i.e. advanced persistent threats, unlike ordinary attacks, infiltrate their targets deeply and work covertly for a long time.
Advanced Persistent Threat (APT) Definition
Advanced persistent threats (APT) are sophisticated threats that aim to infiltrate target systems using complex attack techniques.
These threats carefully plan and execute each stage of an attack chain, encompassing both technologically advanced and social engineering tactics. Therefore, APTs can not only overcome technical defences, but also gain access to systems by exploiting human errors. They are usually carried out by state-sponsored or organised criminal groups.
They aim to remain undetected on their target systems for as long as possible and to capture sensitive data. During this time, they can perform actions such as gathering intelligence, stealing trade secrets, or manipulating incriminating sensitive information.
APT attacks are often concentrated in critical sectors such as the private sector, financial institutions, government departments and infrastructure providers. A successful APT attack can severely damage the target organisation’s reputation, operational continuity and economic status. Therefore, it is essential to take strong and proactive cyber security measures against APTs.
Key Features of APT
Advanced Persistent Threat (APT) attacks use complex structure and advanced techniques. These attacks, which threaten the security of critical infrastructure and data, are constantly evolving.
APT attacks aim to remain undetected on systems for long periods of time, which allows them to gather intelligence and steal sensitive data. They often involve a high degree of secrecy and complexity.
Such threats require specialised research and detailed planning for their targets. By carefully analysing the weaknesses of the target systems, they determine the entry routes and exploit these vulnerabilities.
Another key feature of APT attacks is that they also include social engineering tactics. Attackers manipulate users and gain access to systems using human errors.
These attacks, which persist in systems over the long term, are complex and well-organised threats that aim to harm their targets. Developing strong defence strategies against APTs is very important in reducing the effects of such threats.
What does APT mean?
APT stands for “Advanced Persistent Threat”.
This type of threat is different from ordinary cyber attacks. APT aims to gain long-term access to target systems and work undetected during this process. These attacks, which are aimed at a specific target, are at a level that can cause serious damage and should therefore be handled with care.
Uses advanced techniques.
He carefully analyses his goals and continuously improves himself. For this reason, APT attacks are very difficult to detect with traditional methods.
APTs usually target a specific organisation or sector. Their aim may be to steal critical information or disrupt the functioning of systems. Taking effective measures against such threats is an indispensable part of cyber security strategies. Developing strong defence strategies is vital to protect the future of organisations.
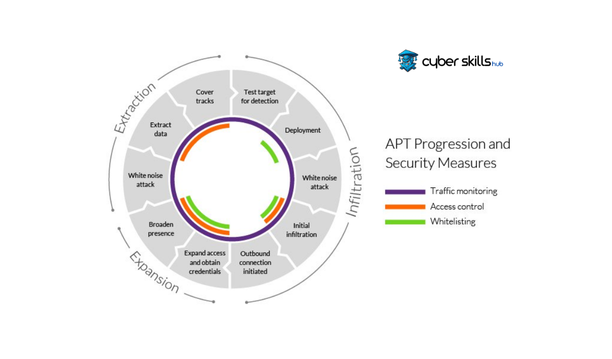
APT Attack Methods
APT attacks are carried out with the aim of capturing sensitive data, gaining financial gain or gaining strategic advantage. Cyber criminals use many methods to achieve these goals. They install malware by gaining the trust of users through social engineering attacks, and then provide continuous access to the system. They also manage to stay on target systems for a long time by using zero-day vulnerabilities and advanced malware. These methods make it difficult to detect and block APT attacks.
Phishing Attacks
Phishing attacks are carried out by cybercriminals who aim to obtain users’ sensitive information. These attacks are usually carried out via email or malicious websites.
A successful phishing attack can compromise the entire digital identity of the targeted person.
Organisations can minimise such threats by training employees against phishing attacks and using advanced security software. Strong password policies and two-factor authentication provide extra layers of security.
Being aware of these attacks and taking continuous security measures is the key to effectively combat cyber threats. Every individual and organisation can protect themselves against such threats by constantly updating their cyber security strategies.
Malware
Malicious software is programmes created to damage or gain unauthorised access to computer systems.
Such software can steal users’ data, degrade system performance and even render entire businesses inoperable. Malware includes viruses, worms, trojans, ransomware and spyware, each of which has a different way of functioning.
As part of advanced persistent threats (APT), malware can carry out long-lasting and targeted attacks. This is carefully planned to remain undetected on the victim’s system and cause maximum damage.
To protect against such threats, powerful antivirus software, constantly updated security applications and awareness training are critical. Complying with international security standards and implementing the latest technological solutions play a vital role in combating malware for individuals and organisations. Advanced security measures create a strong line of defence against cyber threats and minimise potential future attacks.
Vulnerability Exploits
Vulnerability exploits involve weak points targeted by malicious actors. Such attacks can leave systems and networks vulnerable.
APTs infiltrate victims’ systems by detecting and exploiting these vulnerabilities. This method gives them long-term access.
Automatic updating and strict security policies have a great impact on reducing the risk of exploitation. Software and operating systems should be kept up to date and employees should be made aware.
Against advanced security threats, companies should conduct regular cyber security assessments. These assessments identify vulnerabilities and determine the necessary measures. Security patches should be implemented quickly, and personnel should be raised awareness through continuous training. As a result, a solid line of defence against APT threats can be established by developing effective protection strategies.
Stages of APT
The phases of APT usually consist of five main steps: reconnaissance, infiltration, persistence, data collection and escape. Each phase aims to enable the attackers to gain further information and deeper penetration into target systems.
The first phase, reconnaissance, begins with a comprehensive mapping of the target. Attackers gather information about target systems and networks, identify vulnerabilities and potential entry routes. In the next stages, infiltration takes place and attackers gain access to the target system using various methods. In the persistence phase, they can establish a permanent access point and maintain a long-term presence in the target network. Finally, comes the data collection and escape phases, where the collected sensitive information is extracted and various methods are used to hide the traces of the attack.
Information Collection
The information gathering phase is critical in the APT process. Attackers adopt a strategic approach to obtain maximum information from the target.
A detailed analysis of the target’s network infrastructure forms the basis of this phase. This analysis identifies network weaknesses.
In order to succeed in the information gathering phase, certain tools and techniques are used, as well as social engineering methods. Attackers optimise their strategies by systematically evaluating the data they obtain.
This process, carried out with creative and sophisticated methods, allows attackers to better understand target systems and use weak points more effectively. The accuracy and scope of the data obtained during the information gathering phase directly affects the success rate of the attack. Therefore, those who establish a line of defence should develop strong protection mechanisms against information gathering techniques.
Infiltration
Infiltration is a critical phase of APT.
At this stage, attackers use various methods to enter the target’s system. Malware, malicious attachments and specially designed attack techniques are often used to infiltrate target networks. Once the attackers have successfully accomplished the infiltration, they establish their control over the system and strengthen their position as advanced threat actors. At this point, it becomes difficult to detect and respond to the infiltration.
Confidentiality is of paramount importance during the infiltration phase.
Attackers carefully plan all their activities to avoid attracting attention. This allows the attack to remain undetected for longer once the defence mechanisms have been bypassed. It also allows attackers to establish deeper and more pervasive control over their target systems.
In case of detection of infiltration, fast and effective intervention is important. Such infiltrations into systems can have serious impacts on the reputation and financial status of businesses and organisations. Therefore, security protocols and proactive measures should be developed to make infiltration difficult. Continuous improvements in technology and threat detection systems are the key to building resistance to such attacks.
Persistence
One of the most fundamental characteristics of APT attacks is their ability to stay on target systems for a long time. So, how do they achieve this persistence?
These attacks start with in-depth analyses and information gathering processes that find and exploit the weak points of the target systems. Attackers explore every corner of the systems and determine where they can benefit from.
Persistence is based on the ability of attackers to persist on targeted systems for long periods of time. Once they have consolidated their control over the system, attackers can continue to steal more data and cause more damage undetected.
In this process, it is of great importance that attackers disguise themselves using various techniques and tools. Rootkits, hidden network connections and other hiding methods provide protection against external interference.
Another critical element of ensuring persistence is the need to continuously circumvent security systems. Attackers must adapt and update themselves against constantly changing threat detection mechanisms.
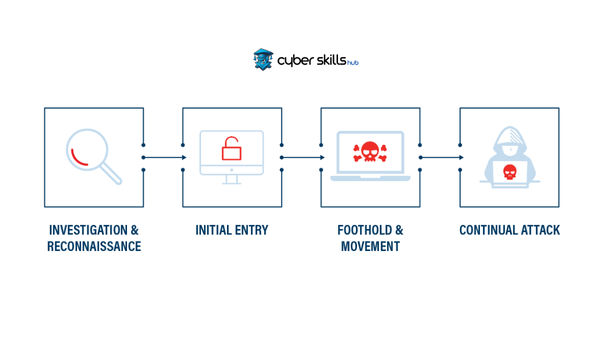
Protections Against APT
Advanced persistent threats (APTs) use sophisticated and strategic methods to compromise systems. It is therefore critical for organisations to protect themselves.
The first step is to develop a strong cyber security strategy. This strategy includes continuous monitoring, immediate detection of vulnerabilities and rapid response; it also includes user training and awareness raising.
Secondly, the “depth of defence” approach is important. Redundant layers of security provide broader protection against the different tools of attackers.
Firewalls and IDS/IPS Systems
Firewalls prevent unauthorised access by monitoring and controlling network traffic. In this way, they help prevent malicious activities.
IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems) detect suspicious activities on the network and take necessary measures. These systems form a critical line of defence for network security.
For an organisation to be resistant to APT attacks, firewalls and IDS/IPS systems must be effectively configured and continuously updated. Trained personnel and regular audits increase the effectiveness of these systems.
Through the proper use of current technologies, significant steps can be taken in dealing with advanced persistent threats. Thus, the security of organisations is ensured at the highest level.
Training and Awareness Raising
Training and awareness of advanced persistent threat (APT) plays a critical role in increasing the security of organisations.
- Awareness Trainings: Continuously informing the personnel about APT symptoms and ways of protection
- Simulations: Teaching how employees should react in real situations by simulating possible APT attacks
- Regular Debriefing: Sharing and discussing current threats and attack methods
- Policies and Procedures: Clear determination of organisational security policies and procedures
Regular training of personnel increases the level of awareness of APTs.
Thanks to these trainings, employees become more aware and prepared for potential threats. For more information, you can review our Cyber Threat Intelligence Training programme.
APT Examples
APTs can cause great damage by targeting many organisations around the world.
One of the most well-known examples is the Russia-based APT28 group. This group has organised attacks on state institutions of many countries for cyber espionage and information leakage. Another example is the China-based APT1 group; this group has carried out various attacks, especially for economic and industrial espionage.
Another notable APT example is the Iran-based APT33. This group targeted companies operating in the energy sector and carried out data theft.
Finally, we should not forget the North Korea-based Lazarus (APT38) group. This group is known for cyber-attacks against financial institutions and media companies around the world. These remarkable examples demonstrate how destructive and sophisticated APTs can be. Organisers must be prepared for such threats and implement constantly evolving defence strategies.
Sectoral Impacts of APT
Advanced Persistent Threats (APTs) can have large-scale impacts in various sectors. So, what are the sectoral impacts of APT?
In the financial sector, APT attacks can cause great damage to banks and financial institutions. Information leakage and money theft can damage the reputation of organisations and undermine customer confidence.
In the healthcare sector, hospitals and healthcare providers can also be targets of APTs. Sensitive patient information can be stolen for the purpose of identity theft, which can seriously threaten the privacy of patients.
When we look at the energy sector, APTs’ attacks on energy infrastructure can lead to major economic losses and interruption of energy supply. Such attacks can also pose great risks to national security.
As a result, APTs can affect many sectors and cause serious problems in different areas. All sectors need to be prepared for such threats.
Frequently Asked Questions About APT
What is an Advanced Persistent Threat (APT)?
Advanced persistent threats (APT) are one of the most sophisticated categories of cyber threats today. These threats are characterised by long-lasting and planned attacks, usually against a specific target. APTs are intended to gain access to an organisation’s information systems on a continuous basis. Their aim is to steal, damage or destroy information. These threats are executed by specialised teams to achieve their goals using advanced techniques and tactics. Attacks can be so complex that they can often go undetected for months or even years.
How do APT attacks differ from typical cyberattacks?
APTs are highly targeted, persistent, and use complex techniques (including social engineering) to remain hidden for extended periods, unlike more common, opportunistic attacks aiming for quick gains.
What are the typical stages of an APT attack?
APT attacks usually involve several stages: reconnaissance (information gathering), infiltration (gaining access), persistence (maintaining access), data collection (gathering target data), and exfiltration (extracting data) and obfuscation (hiding tracks).
What methods do APT attackers use?
Common methods include sophisticated phishing attacks, exploiting zero-day vulnerabilities, deploying advanced malware, and leveraging social engineering to exploit human error.
How can organizations protect themselves against APTs?
Effective protection involves a multi-layered security strategy including robust firewalls and IDS/IPS, regular security assessments, timely patching, strong access controls, and crucial employee training and awareness programs.







