Currently Empty: $0.00
What is Meterpreter? High Level Payload Guide

Meterpreter, as a cybersecurity tool, is of great interest among security experts and ethical hackers. This powerful payload works under the Metasploit framework, providing comprehensive control over target systems and enabling post-exploitation activities. Meterpreter can be used on both Windows and Linux operating systems, making it a versatile tool.
In this article, we will examine the basic working principles and usage areas of Meterpreter. We will also discuss the commands and post-exploitation techniques offered by Meterpreter. We will share the necessary information for security experts to use this tool effectively and emphasise the importance of Meterpreter in the cyber security world.
What is Meterpreter and How Does It Work?
Definition and Properties
It is one of the most advanced and effective payloads of the Metasploit Framework. This powerful tool is frequently used by cyber security experts and ethical hackers. Meterpreter is a type of payload that runs dynamically on target systems and uses the in-memory DLL injection technique. One of its main features is that it does not write anything to the disc, which reduces the risk of detection.
The main features of Meterpreter are:
- In-memory operation
- Dynamic extensibility
- Channel-based communication system
- Possibility to add new features at runtime
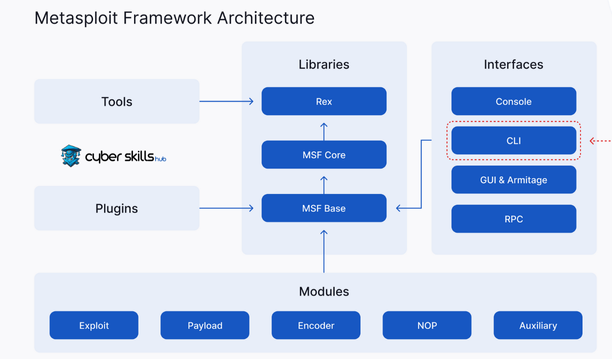
Working Principle of Meterpreter
It is used in the post-infiltration phase of the target system. It works as follows:
- The attacker creates the Meterpreter payload via Metasploit Framework.
- The payload is sent to the target system and executed.
- The payload hides itself in memory by DLL injection.
- Meterpreter communicates with the attacker’s computer using staged payloads and sockets over the network.
It injects itself into a running process on the target system and can easily switch to other running processes. This feature makes it stay in the system longer and harder to detect.
Advantages of Meterpreter
It provides many advantages to cyber security experts:
- Wide range of commands: Various operations such as downloading/uploading files, taking screenshots, keyboard recording can be performed.
- Flexibility: Can be used on different operating systems (Windows, Linux).
- Low risk of detection: Since it runs in memory, it is difficult to detect by antivirus software.
- Extensibility: New features and extensions can be added.
Meterpreter provides comprehensive control over remote systems. Users can see all available commands and their descriptions with the ‘help’ command. For example, the ‘sysinfo’ command provides information about the target system, while the ‘hashdump’ command displays encrypted passwords.
As a result, its powerful features and flexible structure make it an indispensable tool in the field of cyber security. However, it is of great importance to use this tool within ethical and legal limits.
Meterpreter Commands and Uses
Basic Meterpreter Commands
It provides cyber security experts with a wide range of commands. These commands are used to perform various operations on the target system. Here are some of the most basic Meterpreter commands:
- help: Lists all available commands and their descriptions.
- background: Throws the current session into the background and returns to the msf prompt.
- exit and quit: Ends your session.
- run: Runs a custom script.

File System Commands
It allows you to perform various operations on the target system’s file system. Here are the most commonly used file system commands:
| Command | Description |
|---|---|
| cat | Reads file contents |
| cd | Switches between directories |
| download | Downloads files from the destination |
| edit | File edits |
| ls | Lists files |
| mkdir | Creates new directory |
| rm | Deletes file |
| upload | Uploads file to destination |
System Information Commands
The commands used to get detailed information about the target system are as follows:
- getuid: Indicates the user ID it works with.
- sysinfo Provides detailed information about the target system.
- ps: Lists the running processes.
- idle time Indicates the idle time of the user.
Network Commands
It allows you to perform various network-related operations:
- ipconfig: Shows the network interfaces and IP addresses on the target system.
- portfwd: Performs port forwarding operations.
- route Displays and modifies the routing table of the target system.
One of its powerful features is the ability to add new functions at runtime. This is achieved through extensions. Extensions are downloaded as DLLs to the target system, loaded into memory and initialised. This process is transparent and takes about 1 second.
The privacy feature is also noteworthy. All operations take place in memory and nothing is written to the disc. It also uses encrypted communication by default. These features limit forensic evidence and reduce the impact on the target machine.
Post-Exploitation Techniques with Meterpreter
As a powerful tool for penetration testers, it is used to implement various post-exploitation techniques on target systems. These techniques increase the attackers’ control over the system and allow them to obtain more information.
Privilege Escalation
Privilege escalation allows attackers to move from limited privileges to higher privileges. It offers various methods to facilitate this process:
- Unquoted Service Paths: When starting services in Windows, if executable file paths are not properly configured, attackers can inject their malware into the system.
- DLL Sideloading: DLL files used when starting applications can be replaced with malicious DLLs to infiltrate the system.
Lateral Movement
Lateral movement allows attackers to access other systems within the network. Meterpreter offers several methods for this purpose:
- PsExec: PsExec, a trusted Microsoft tool, can run arbitrary files on the target system.
- SCShell: This tool can run a fileless payload by modifying the binary path of an existing service.
- WMI: Windows Management Instrumentation can be used to modify existing services.
Data Exfiltration
Data exfiltration involves extracting sensitive information from the target system. Meterpreter offers various commands to facilitate this process:
| Command | Description |
|---|---|
| download | Downloads files from the destination |
| upload | Uploads file to destination |
| cat | Reads file contents |
| search | Searches for specific files |
Persistence
Persistence makes it possible for attackers to gain continuous access to the system. Some persistence methods that can be implemented with Meterpreter are as follows:
- Registry Editor: By adding certain keys in the Windows registry, the malware can be made to run at system startup.
- Scheduled Task: By creating scheduled tasks, malware can be run at certain intervals.
- Startup Folder: By placing malicious files in the startup folder, they can be automatically executed at system startup.
These post-exploitation techniques allow attackers to gain more control over the target system and move within the network. However, it is of great importance that these techniques are used within ethical and legal boundaries. Security professionals should understand these techniques and take the necessary precautions to protect their systems against such attacks.
Conclusion
Meterpreter stands out as a powerful tool in the world of cyber security. The in-memory nature of this payload, its wide range of commands and the possibilities it offers for post-exploitation techniques make it indispensable for ethical hackers and security experts. The fact that Meterpreter can be used on Windows and Linux systems shows its versatile nature and allows it to be used effectively in different scenarios.
However, the fact that Meterpreter is so powerful makes it even more important to use it within ethical and legal boundaries. It is crucial that security professionals understand this tool and take the necessary precautions to protect their systems. In conclusion, Meterpreter has had a major impact on cyber security and will continue to drive developments in this field in the future.
Frequently Asked Questions About Meterpreter
What does a payload do?
In computer security, a payload functions as a piece of malicious software. This can include malware such as worms or viruses that perform actions such as deleting data, sending spam or encrypting data.
What is a Metasploit session?
Metasploit session is a process that takes place within the Metasploit framework that allows security professionals to identify vulnerabilities and use these vulnerabilities to test and secure systems.







