Currently Empty: $0.00

A powerful tool for making DNS queries, the dig command is an indispensable resource for system administrators and network professionals. This command is used to obtain information from DNS servers, resolve IP addresses, and examine DNS records. Available for Windows and Linux systems, dig is also useful for diagnosing DNS problems and verifying network configurations.
In this article, we will cover the basic use of the dig dns command and show you how you can query specific DNS record types. You will also learn how to use the full potential of this tool by exploring the advanced dig command options. Finally, we will also cover related topics such as DNS caching and reverse DNS (rdns), highlighting the importance of the dig command in network management and troubleshooting.
Basic Use of dig Command
The dig command is a powerful tool used to perform DNS (Domain Name System) queries. This command is used to query DNS and IDN (Internationalised Domain Name) records on Linux and Windows operating systems. Developed as part of BIND, dig provides more detail and flexibility than nslookup. If you want to better understand DNS configurations and gain in-depth knowledge about network security, Cyber Security Basics Training will give you a comprehensive start.
Syntax and Parameters
The basic structure of the dig command is as follows:
dig [server] [name] [type]- [server]: Server or IP address where the query will be made
- [name]: Domain name to be queried
- [type]: Öğrenilmek istenen DNS kaydının türü (belirtilmezse varsayılan olarak A kaydı sorgulanır)
Some commonly used parameters are:
- -t: Specifies the DNS query type (for example, A, MX, CNAME)
- -x: Used to make a reverse DNS query
- +short: Shows only the IP address
- +noall +answer: Shows only the ANSWER SECTION
Simple DNS Query Example
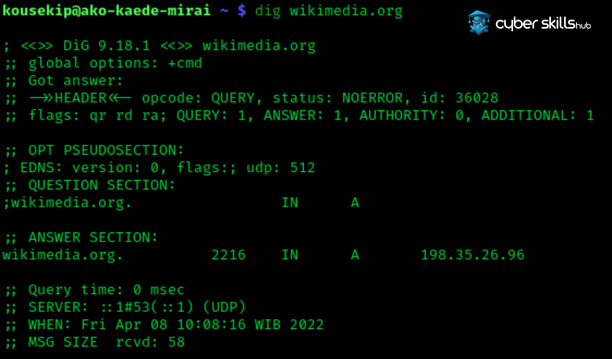
You can use the following command to make a basic DNS query:
dig example.comThis command displays the A records for the domain name example.com. In the output, you can find the relevant information under the heading ‘ANSWER SECTION’. For a shorter result:
dig example.com +shortThis command will show only the IP address.
You can use the -t parameter to query different DNS record types:
dig example.com -t MX # MX kayıtları için
dig example.com -t NS # NS kayıtları için
dig example.com -t TXT # TXT kayıtları içinThe dig command is very useful for diagnosing DNS problems and verifying network configurations. System administrators and network experts can use this tool to obtain information from DNS servers, analyse IP addresses, and examine DNS records.
Querying Special DNS Record Types

The dig command is a very useful tool for querying different DNS record types. In this section, we will examine how to query the most common specialised DNS record types.
MX Records Enquiry
MX (Mail Exchanger) records determine to which servers mail from e-mail accounts connected to a domain name is forwarded. You can use the dig command to query these records as follows:
dig example.com -t MXMX records can be multiple and are indicated by their priority values. For example, MX records for Expert Mail are as follows:
- mx1.mailserver.com (priority value: 10)
- mx2.mailserver.com (priority value: 10)
Equal priority values ensure that incoming mail is distributed evenly between the two servers.
NS Records Enquiry
NS (Name Server) records specify the authorised name servers for a domain name. These servers maintain and manage DNS information for the domain name. To query NS records:
dig example.com -t NSNS records are used to identify the IP addresses of the servers from which the domain name is broadcast. This information is important for domain name management and troubleshooting.
TXT Records Enquiry
TXT records are text-based records that can contain various information about the domain name. These records are often used for purposes such as email verification, spam prevention, or domain name ownership verification. To query TXT records:
dig example.com -t TXTThis command will list all TXT records for the domain name.
Querying specific DNS record types is critical for network administration and troubleshooting. The dig command allows you to query these records quickly and efficiently. MX, NS, and TXT records provide valuable information about a domain’s e-mail configuration, name servers, and various validation mechanisms. Using this information, you can optimise your DNS configurations and identify and resolve potential problems.
Advanced dig Command Options
The dig command is a powerful tool for performing DNS queries. In this section, we will examine more advanced usage options for the dig command.
+short Parameter
The +short parameter limits the output of the dig command to only the ‘ANSWER’ section returned from the query. This is useful for obtaining more concise results. For example:
dig example.com +shortThis command will briefly display the IP address of the example.com domain.
+noall and +answer Parameters
The +noall and +answer parameters, when used together, make the output of the dig command more detailed.
- +noall: Hides comments, authorisation, additional sections and statistics.
- +answer: Shows the answer field (ANSWER SECTION).
Example use:
dig example.com +noall +answerThis command will display the DNS records for the domain name example.com in detail.
Using a Private DNS Server
The dig command uses the system DNS server by default. However, it is also possible to query through a special DNS server. For this, the @ parameter is used. For example
dig example.com @8.8.8.8This command queries the domain name example.com using Google’s DNS server (8.8.8.8.8).
In addition, the following format can be used to query a specific record type through a specific DNS server:
dig example.com -t MX @ns1.uzakdnssunucusu.comThis command queries the MX records of the domain name example.com via remotednserver.com.
Other advanced options of the dig command include the following:
- -x: Used to make a reverse DNS query.
- -f: Reads queries from a file and returns the results.
- -c: Determines how many times the specified query will be executed.
- -p: Specifies the port used when making DNS queries.
- -y: Used with the HMAC-MD5 key and password to authenticate DNS queries.
These advanced options provide system administrators and network professionals with powerful tools to diagnose DNS problems, verify network configurations, and examine DNS records in detail.
Conclusion
It is clear that the dig command is a powerful tool for making DNS queries. It provides system administrators and network professionals with an efficient way to retrieve information from DNS servers, resolve IP addresses, and examine various DNS records. dig offers a wide range of features, from basic to advanced options, making it an indispensable resource for network administration and troubleshooting.
As a result, the dig command is an invaluable tool for optimising DNS configurations and detecting and resolving potential problems. Querying specific DNS record types such as MX, NS, and TXT provides important information about email configuration, name servers, and various validation mechanisms. Using this information, network administrators can more effectively manage their DNS infrastructure and improve its performance.
Frequently Asked Questions About Dig
When and how is the DIG command used?
When the DIG command is used to learn the IP address, the +short parameter is added. Also, +noall and +answer parameters can be used together to see only the answer part of the output.
What is the function of the Dig Tool and on which systems is it used?
The DIG tool is used to query DNS and Internationalised Domain Names (IDN) on Linux and Windows operating systems. Developed as part of the BIND software, DIG offers more detailed information and flexibility than the nslookup tool.







