Currently Empty: $0.00
What is RDP? Basic Principles of Remote Desktop Connection

Today, remote working and access solutions are becoming increasingly important. At this point, RDP (Remote Desktop Protocol) technology stands out as a powerful tool that allows users to connect to remote computers. It is a remote desktop connection method built into Windows operating systems developed by Microsoft and works over the TCP/IP protocol.
In this article, we will discuss in detail what RDP is and how it works. We will also examine the advantages and usage areas of RDP. We will also touch on the security issue and discuss the possible risks associated with RDP and the precautions that can be taken against them. Finally, we will evaluate the place of RDP technology in today’s business world and its future potential.
What is it and how does it work?
Definition
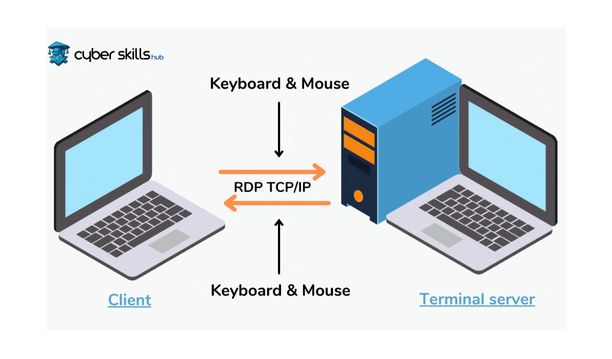
It stands for ‘Remote Desktop Protocol’ and is a secure network communication protocol developed by Microsoft. This protocol allows users to remotely access a computer’s desktop. Remote Desktop Protocol is built into Windows operating systems, and users can use Remote Desktop Protocol client software to access the desktop of a remote computer. Understanding how RDP works can also help when making comparisons with other protocols; at this point it is useful to learn about NTLM.
Working Principle of RDP
Remote Desktop Protocol offers the possibility to provide remote access on the same network or via the internet. This technology provides a secure remote access experience with features such as data encryption and security protocols. Two basic components are required for RDP connections to work: a Remote Desktop Protocol server and a Remote Desktop Protocol client. The Remote Desktop Protocol server is the Windows PC or server that is connected to and controlled. The client is the PC or mobile device with the Remote Desktop Protocol client application installed that is used to control the server.
Remote Desktop Protocol also supports features such as different screen resolutions, audio streaming, and sharing of devices such as keyboard/mouse. This allows users to use the remote computer as if it were in front of them. Important peripherals are shared with the remote machine so that users can control it as if they were in front of it.
Steps to Establish an RDP Connection
- Enabling Remote Desktop:Open the Windows Settings menu and go to ‘System’> < encoded_tag_closed > ‘Remote Desktop’. Switch the ‘Enable Remote Desktop’ option to ‘On’
- Security Settings: Limit access to Remote Desktop Protocol protocol connections to non-administrator accounts and limit attempts to enter passwords. Configure Remote Desktop Protocol protocol settings for maximum encryption.
- Finding Connection Information: If you are connecting to another PC on your local network, find the local IP address or host name. You can do this by following the steps in “Windows Settings > Network and Internet > View your network properties”.
- Making a Connection: Use the built-in Remote Desktop Connection tool in Windows. Enter the IP address or host name of the computer you want to connect to and press ‘Connect’.
RDP technology is used in many scenarios such as remote working, support and servicing. For example, telecommuters or travelling employees can access office computers, network administrators can troubleshoot remotely, and companies can provide access to their employees globally.
Advantages and Usage Areas
Remote Desktop Protocol technology plays an important role in today’s business world and information technologies. This protocol transforms the way companies and individuals work by offering many advantages in remote access and management. Here are the main advantages and usage areas of the Remote Desktop Protocol protocol:
Increasing Work Efficiency
Remote Desktop Protocol significantly increases work efficiency by enabling employees to work from outside the office. For example, an employee can access their office computer from home or while travelling and access all their files and applications as if they were in the office. This ensures business continuity and increases employee productivity.
In addition, companies can provide access to their employees on a global scale. This allows team members in different time zones and geographical locations to work on the same projects. Thus, business processes accelerate and companies become more flexible.
Providing Remote Support
It is an indispensable tool for IT professionals to provide remote support. Network administrators or support teams can solve problems quickly and effectively by connecting to users’ computers remotely. This saves time and cost, while increasing user satisfaction.
Remote support is of great importance, especially for companies spread over large geographical areas. IT teams can solve many problems instantly without having to physically travel to different locations. This increases the operational efficiency of companies and reduces the workload of IT departments.

RDP technology provides a great advantage especially in remote management and support processes of SOC teams. For more information, you can take a look at the SOC L1 training.
Resource Optimisation
It helps companies to use their computing resources more effectively. For example, by connecting to a powerful server via RDP, complex operations can be performed even with low-performance computers. This reduces hardware costs and enables more efficient use of resources.
In addition, Remote Desktop Protocol enables companies to manage applications and data via a central server. This facilitates software updates and data backups, but also increases data security. Thus, IT management becomes simpler and more effective.
These advantages of Remote Desktop Protocol significantly improve remote working, support and management processes in the modern business world. By using this technology, companies can achieve a more flexible, efficient and competitive structure.
RDP Security Risks and Precautions
Although Remote Desktop Protocol is a vital tool for remote working and access, it carries significant security risks. In recent years, Remote Desktop Protocol attacks have increased significantly and have become a serious threat to many organisations. In this section, we will examine the security risks of RDP and the precautions that can be taken against them. To gain in-depth knowledge about the security risks of RDP and to take effective measures, it may be useful to receive cyber threat intelligence training. You may benefit from cyber threat intelligence training to gain in-depth knowledge about the security risks of RDP and to take effective measures.
Common RDP Vulnerabilities
The Remote Desktop Protocol protocol uses port 3389 by default. This port has become a known target for attackers. Open RDP ports create a potential entry point for network penetration attempts. Attackers try to find out how to infiltrate the network by scanning these open ports.
Insufficient authentication is one of the most important vulnerabilities of RDP. Single-factor authentication based only on username and password is vulnerable to brute-force attacks. Weak or guessable passwords increase this risk even more.
Lack of encryption makes RDP connections vulnerable to eavesdropping attacks. Unencrypted Remote Desktop Protocol sessions can expose sensitive data to third parties.
Safe RDP Usage Tips
The following measures can be taken to improve safety:
- Port Switching: Changing the default port 3389 can block automated scanning tools and random attacks.
- Firewall Restrictions: Allow RDP access only to permitted servers by applying IP and port restrictions.
- Up-to-date Security Applications: Ensure that all security applications and Remote Desktop Protocol software are up-to-date.
- Network Level Authentication (NLA): Enable NLA to ensure that only authorised users can connect.
- Strong Password Policies: Use passwords that are complex and difficult to guess. Require regular password changes.
- Using RDP as Needed: Enable RDP only when needed and disable it when not in use.
- Event Log Tracking: Detect suspicious login attempts by regularly checking security event logs.
Two-Factor Authentication
Two-factor authentication (2FA) is a measure that significantly increases RDP security. 2FA requires users to use something they have (OTP, security key) or a biometric feature (fingerprint, face scan) in addition to something they know (password).
The implementation of 2FA provides effective protection against brute-force attacks and significantly reduces the risk of unauthorised access. The use of 2FA for RDP connections is critical, especially in systems that provide access to sensitive data.
Implementing these security measures will make the use of RDP more secure and protect against potential attacks. However, it is important to remember that security is a continuous process and to keep security strategies up to date by conducting regular risk assessments.
Conclusion
Remote Desktop Protocol technology has an important place in remote working and access solutions. This protocol offers great benefits in areas such as increasing work efficiency, providing remote support and resource optimisation. However, security risks should not be ignored. Companies and individuals should not neglect to take precautions such as strong passwords, two-factor authentication and up-to-date security applications when using Remote Desktop Protocol.
In conclusion, RDP has the potential to revolutionise the business world. While this technology makes remote working and management processes more flexible and efficient, it also requires careful attention to security. While taking advantage of the benefits of RDP, businesses should assess the potential risks and take the necessary precautions. In this way, RDP technology can be used as a safe and effective tool in the modern business world.
Frequently Asked Questions About RDP
For what purposes is Remote Desktop Connection used?
Remote Desktop Connection is used to access files and applications on one computer or mobile device from another computer, specifically through Chrome Remote Desktop. To access remotely from your mobile device, you need to download the Chrome Remote Desktop application.
How to set up Remote Desktop Connection RDP?
To set up Remote Desktop Connection, first click ‘Allow an application’ on the Windows firewall. After selecting the ‘change settings’ option in the window that opens, complete the process by activating the remote desktop option.





