Currently Empty: $0.00
What is DDoS? Information on DDoS Attacks in Turkey

As the importance of Internet infrastructure in our lives increases day by day, how much of a threat do DDoS attacks pose?
The definition and modus operandi of the attack is a frequent topic of conversation among experts.
DDoS incidents in Turkey reflect global trends and pose specific risks to local infrastructures.
Fundamentals of DDoS Attacks
DDoS, or Distributed Denial of Service attack, occurs when a large number of computers send data to a targeted server simultaneously. This intense data flow consumes the server’s resources and causes it to struggle to provide service. The aim of the attack is to disrupt, slow down or completely stop the service.
In a DDoS attack, attackers often use a network called a botnet. A botnet contains many infected computers that have been compromised and controlled by malware. These infected devices are used to generate coordinated traffic against the targeted system, making the attack appear to come from multiple points rather than a single source.
How resilient the targeted system’s existing security mechanisms are against such attacks is one of the most important factors determining the impact of the attack. An effective defense strategy is a critical issue that experts in the field of cyber security emphasize.
What is a DDoS Attack?
A DDoS attack is a type of cyber-attack that aims to put systems that provide services over the internet out of service by malicious actors. These attacks overload the system’s resources, causing the service to slow down or stop completely.
The way the attack takes place is that controlled computers in a botnet network, often referred to as zombie computers, send simultaneous and massive amounts of spoofed traffic to the target server. This flood of controlled traffic exceeds the processing capacity of the target system and prevents normal users from receiving service.
76% of internet users in Turkey state that they are not aware of DDoS attacks.
One of the most important factors determining the impact of DDoS attacks is the security measures the targeted system has in place. Defense mechanisms such as Greek firewalls, load balancers and DDoS protection services provide significant protection against attacks. However, in the face of constantly evolving attack methods, the system’s defense infrastructure needs to be dynamically updated.
Basic DDoS Types
DDoS (Distributed Denial of Service) attacks generally fall into three main categories: volume-based, protocol-based and application layer attacks. Each uses different methods to consume system resources.
Volume-based flood attacks maximize the amount of data transmitted per second (bit-rate). For example, they use UDP flooding, ICMP flooding, etc. to flood the bandwidth of the target network, making it temporarily unreachable. These require sophisticated network monitoring and analysis tools to detect and filter the attack, and a common indicator of this type of attack is an excessive increase in network traffic.
Protocol-based attacks target the network or transport layer protocols of the target system with tactics such as SYN flood, PING of Death and Smurf Attack. These attacks consume the processing capacity of the server or intermediate network equipment, making it difficult or impossible to process normal traffic.
Application layer attacks target the application-level resources of the target web server with tactics such as HTTP flooding or slowloris. These methods can be effective using very small amounts of network traffic and are often more difficult to detect because they may exhibit behavior similar to legitimate user traffic. Therefore, in-depth packet inspection and careful analysis of application layer data are necessary to counter these attacks.
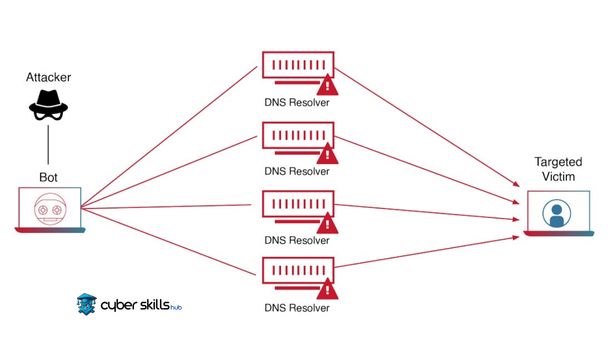
Mechanism of Attacks
DDoS attacks are based on overloading the target system or server with large amounts of fake network traffic. This fake traffic consumes system resources and prevents legitimate users from accessing services, so that the system can be crippled or rendered inaccessible.
Attacks are often coordinated through botnets. A botnet is a network of zombie computers controlled by cybercriminals.
These zombie computers participate in sending synchronized and automated traffic to the target. The attack overwhelms the target by sending large amounts of data quickly and continuously.
The methods used include a wide variety of attack vectors such as SYN flood, UDP flood, ICMP flood and HTTP flood. Each method targets a specific aspect of the target network or server, clogging network connections or overloading processing capacity.
A successful DDoS attack can not only cause financial damage to the targeted organization, but also undermine user confidence and damage brand reputation. Organizations should therefore take preventive measures against such attacks.
Preventive measures include strategies such as network traffic monitoring, intrusion detection systems and using distributed resources. A good defense strategy should include multi-layered security measures that can neutralize potential DDoS attacks.
Dimensions of DDoS Threat in Turkey
Turkey has become an attractive target for DDoS attacks due to its strategic location and growing digital economy. This situation poses serious risks for both the private sector and public institutions.
Despite the development of cybersecurity infrastructure, many organizations in Turkey are not adequately prepared for DDoS attacks. As the size and frequency of attacks increase, concerns about the capacity to fend them off are deepening.
Disruptions caused by DDoS attacks can affect a wide range of industries, from e-commerce platforms to the financial sector, creating serious obstacles for Turkey’s digital transformation.
Turkey’s Cyber Security Situation
With the strengthening of the cyber security infrastructure in Turkey, the level of awareness of institutions has increased; however, the question is often asked whether these efforts are sufficient. With the rapid development of information technologies, it is a fact that malicious actors have improved their attack methods.
Organizations must constantly develop new defense mechanisms, especially to protect critical infrastructures. DDoS attacks are an important testing ground for these mechanisms.
Adopting a proactive approach to DDoS attacks and implementing continuously updated defense strategies is of critical importance in Turkey. It is necessary to apply effective network management and traffic analysis methods in order to react instantly to attacks and at the same time minimize the risks.
Adopting a national approach to cybersecurity and increasing the human resources trained in this area is of great importance for Turkey. Accelerating the cyber security investments included in the development plans, establishing integrated cyber defense systems and intensifying international cooperation will increase the country’s cyber security level and make it more effective in combating threats such as DDoS.
Featured DDoS Cases in Turkey
Turkey’s digital infrastructure has become an important target for DDoS attacks. In prominent cases in Turkey, the financial and telecommunications sectors have been targeted.
In parallel with the global increase, Turkey is also experiencing an increase in the frequency and severity of DDoS attacks. While malicious actors use large-scale botnets to launch denial-of-service attacks, organizations are forced to respond quickly and effectively to these attacks. In particular, e-commerce platforms, news portals and online services of public institutions are among the areas most affected by such attacks.
The need for increased cybersecurity awareness in the field of education has become clearer thanks to these attacks. In particular, universities and large educational institutions are conducting awareness-raising activities among students and staff to prevent DDoS attacks, which they frequently encounter.
DDoS attacks against the Turkish financial sector in recent years have raised national concern and necessitated serious measures to counter these threats. The scale of the attacks has led institutions to invest more in measures such as firewalls, DDoS protection services and continuous monitoring. Although this increases costs, it is seen as a factor that strengthens the sector’s resilience against cyber-attacks.
How to Detect and Prevent DDoS Attacks
A number of defense strategies and technologies are essential to detect and prevent DDoS attacks. First, suspected attacks can be identified at an early stage by detecting abnormal behavior patterns through traffic analysis. Organizations can protect resources targeted by cyber attackers by deploying solutions such as Content Delivery Networks (CDN) and DDoS protection services. They can also strengthen the resilience of the system through proactive steps such as increasing throughput capacity and constantly reviewing network configuration. Automated systems used for intrusion detection provide the opportunity to take quick action by detecting potential threats in advance, while the creation and implementation of contingency plans ensures timely interventions in the event of a crisis. In essence, the integration of advanced cybersecurity solutions such as cross-layer intrusion detection, behavioral-based detection systems and botnet detection mechanisms is vital to protect institutions and organizations in Turkey from the harmful effects of DDoS attacks.

Early Detection Signs
Early detection of DDoS attacks is made possible by sudden and inexplicable changes in network performance. In this context, alert should be raised when higher than normal traffic volumes are observed. Slowing or interrupted service can be an early warning sign.
Sudden delays in response times of some services or applications on the network should be taken into account. Because this may be an indication that a DDoS attack has started.
Abnormal traffic patterns are often a precursor to DDoS attacks. Especially when an increase in traffic density is observed towards a specific target, the likelihood of an attack is high.
Many of the requests to systems under attack come from spoofed or spoofed IP addresses. Log analysis can reveal such suspicious activity.
In addition to anomalies in network traffic, unusual port and protocol usage aimed at bypassing the firm’s cybersecurity systems are early warning signals. Such information can be detected through close monitoring of system logs.
Finally, if an abnormal load on a system’s resources or over-utilization of capacity is observed, this could be the beginning of a DDoS attack. Immediate measures should be taken to mitigate the effects of the attack.
Effective Protection Strategies
Effective protection against DDoS attacks requires a combination of proactive measures and dynamic defense strategies.
- Monitoring network infrastructure: Continuous monitoring allows to quickly detect anomalies in traffic.
- Bandwidth management: Sufficient bandwidth ensures resilience against unexpected traffic loads.
- Intrusion detection systems: It is essential to have systems that can detect attacks early and mobilize response mechanisms.
- Simultaneous attack mitigation solutions: Mitigation solutions that are automatically activated in the event of an attack, minimizing damage.
- Backup and re-route operations: Backing up critical data and services and rerouting traffic through alternative routes.
- Content delivery networks (CDN): The use of distributed servers reduces risk by spreading the traffic load.
Adopting multi-layered security approaches increases resilience to the threat of attack.
State-of-the-art tools, as well as trained and experienced cybersecurity professionals, play a critical role in the effective implementation of these strategies. For more information on how to detect and prevent DDoS attacks,see “Cybersecurity:How to Defend Against Technological Threats“.
Damage Control and Recovery Process After DDoS
A fast and effective damage control process is critical to detecting and mitigating the effects of a DDoS attack. The first step is to review the status of network resources and services at the onset of the attack. Activating the incident response team, isolating the affected systems and activating contingency plans are among the necessary actions to limit the damage. In addition, a detailed analysis of the size and type of attack should be conducted so that preventive strategies can be developed.
In the recovery and return to normalcy process, one of the main steps is to restart operational activities by utilizing backups of critical systems and data. At this stage, cybersecurity experts also make the necessary arrangements to restore the network to its former operational state and strengthen defenses against similar attacks in the future. The final remediation, especially after the attack has been detected, is aimed at ensuring the long-term health of the system.
Post Attack Steps
The first thing to do when a DDoS attack is detected is to take measures to minimize damage to the system. Fast action in this process significantly affects the extent of the damage.
- By analyzing traffic: Identifying the malicious traffic flow that carried out the attack.
- Considering to interrupt communication: Blocking or diverting suspicious traffic flow.
- Taking action to protect network resources: Protect important services by allocating sufficient resources to them.
- Activating backup systems: Redirecting transactions to backup systems.
- Ensuring that the attack is isolated: Preventing the spread of harm.
- Communicating with interested parties and customers: Informing about the situation and providing guidance on security protocols.
Communication channels should be kept open during such attacks and all stakeholders should be informed.
As soon as operations return to normal, a detailed analysis of the source of the attack and its techniques is essential to increase system security.
Long Term Security Planning
Long-term security planning requires a strategic approach to take precautions against future DDoS attacks. In this approach, continuous monitoring of systems and regular updates of existing security measures are essential.
Following the risk assessment, it is critical that appropriate security policies are established and adopted by the entire organization. Training programs and regular security drills should be planned to maintain the effectiveness of these policies.
Security audits should be conducted periodically to identify and remediate potential vulnerabilities of the network infrastructure. Such audits aim to reduce potential attack vectors and increase the resilience of systems.
Dynamic defense mechanisms are vital to adapt to the enemy’s tactics. Keeping pace with the development of cyber security technologies, it is imperative to exhibit proactive behavior against attack and to create the necessary infrastructure for this.
Ultimately, security planning is a process and should always be dynamic. With continuous training, development and updating, these plans should be kept alive and an effective defense mechanism should be created against threats. If you want to improve yourself in the field of cyber security, you can review our courses on our website. These courses will help you gain in-depth knowledge on the subject and improve your skills.
Frequently Asked Questions About DDoS
What is a DDoS attack?
A DDoS (Distributed Denial of Service) attack occurs when an excessive amount of spoofed traffic is sent to a targeted server from a large number of computers simultaneously. This consumes the server’s resources and disrupts normal services.
Why are DDoS attacks in Turkey on the rise?
Turkey’s strategic location and digitalized economy have made it an attractive target for DDoS attacks. Especially the financial and telecommunications sectors are frequently affected by such attacks.
How to detect DDoS attacks?
DDoS attacks can be detected by sudden changes in network performance. Higher than normal traffic volumes, interrupted or slowed services, and delays in response times are among the early signs of an attack.
How can organizations in Turkey be protected against DDoS attacks?
Organizations can protect themselves by continuously monitoring network traffic and installing intrusion detection systems. They can also protect target resources using content delivery networks (CDNs) and DDoS protection services.
How to contain the damage after a DDoS attack?
When an attack is detected, traffic analysis should be performed to identify malicious traffic flow and block suspicious traffic flow. It is also important to secure network resources and put redundant systems in place to prevent damage from spreading.







