Currently Empty: $0.00

In the cyber security world, Nessus is one of the most popular vulnerability scanners; so how does this tool work?
Nessus is a comprehensive software developed to detect possible security vulnerabilities by scanning devices on the network.
The correct configuration and use of the Nessus scanner are critical for organizations to move step by step towards increasing their cyber defense capacity.
Basics of Nessus
Nessus is a vulnerability scanning tool developed by Tenable Network Security and constantly updated. It can be considered an industry standard at the point of detecting various security vulnerabilities. Scanning operations are performed on servers, network devices, systems and applications, and thanks to these scans, a clear and clear security status report is provided to information security professionals.
With its ease of use and extensive database, Nessus has become one of the most preferred tools of cyber security experts. One of the strengths of the tool is that it can work on many different platforms and environments. For example, it can be easily used on Windows, Mac OS X and Linux operating systems. In addition, with thousands of private scan signatures developed using NESL (Nessus Scripting Language), security vulnerabilities are detected efficiently, and thus institutions are better prepared for possible security breaches.
History of Nessus
Nessus is an open source vulnerability scanning tool developed by Renaud Deraison in 1998.
Nessus has reached millions of downloads worldwide and has become one of the indispensable tools of the cybersecurity community.
Nessus, which became popular over time, was acquired by Tenable Network Security and commercialized as a closed source, which meant more extensive updates and support.
Despite being a closed-source commercial product, Nessus remains one of the most reliable vulnerability scanning tools on the market thanks to its constantly updated plugin structure and wide range of features.
Basic Features and Functions
Nessus is a wide ranging vulnerability detection tool and is used by countless institutions and individuals around the world for security scans.
- Vulnerability Scanning: Detects security vulnerabilities that exist on devices on the network.
- Malware Detection: Identifies potential malware in systems.
- Configuration Management: Controls the security configurations of the systems.
- Compliance Audit: Monitors compliance with various regulations and standards.
- Network Scanning: Exposes devices and services on the target network.
These scans play a critical role in helping organizations strengthen their cyber defenses.
Nessus has a flexible structure and can work effectively on different network structures and operating systems. It detects and reports security vulnerabilities in detail with thousands of private scan signatures it contains.
Installation and Settings
The installation of Nessus is a process that begins with the execution of the downloaded installation file and is usually guided through an interactive installation wizard. After the successful completion of the installation, the user name and password must be created to log in for the first time. In addition, the license key must also be entered into the system.
After installation, it’s important to configure the various components of Nessus. These settings include policies, scan settings, network discovery, as well as allowed IP ranges and targets to scan. During the configuration phase, you also define schedule settings, such as when and how often scans will occur. New policies can be created for specific scanning needs using predefined scan templates.
Another thing to pay attention to after completing the Nessus installation is regular software updates. Software updates allow new vulnerability signatures and features to be added to the system, thereby increasing the effectiveness and accuracy of Nessus.
In addition to Nessus, for more information about current cybersecurity threats CVE-2024-3094 Vulnerability and Linux Distro Effects you can take a look at our article titled.
Required System Requirements
In order to run Nessus smoothly, specific system requirements must be met. For optimal performance, attention should be paid to the recommended operating systems, hardware specifications, and network configurations. These are critical for screening efficiency and stability.
Operating system as such, an up to date version of one of the Windows, Mac OS or Linux distributions supported by Nessus should be preferred. The system must be compatible with the 64-bit architecture.
The Server, processor (CPU) performance and memory (RAM) capacity varies according to the size and complexity of the scanning process performed. A multi-core processor and sufficient amount of RAM are essential for high performance.
What is necessary for Nessus disk space, must have the capacity to store the scan results and database. Expandable storage solutions should be considered for large databases and long-term log records.
Network connection, must have uninterrupted and sufficient bandwidth to provide continuous and reliable access to the target systems. In addition, it is important to check whether the network segment in which Nessus will operate is compatible with the firewall and other network security solutions.
Finally, firewall and antivirus configurations, Nessus must be set up properly so that browsing traffic does not get stuck in unnecessary obstacles. These configurations are important to prevent false positives and possible communication barriers during screening.
Installation Steps
The Nessus installation process begins with downloading the appropriate version of the software. Supported operating systems include Windows, macOS, and Linux. Downloads can be made through Tenable’s official website, and users can access the relevant installation files by creating an account.
When the downloaded installation file is executed, a set of installation preferences is received from the user. These preferences may include targeting, browser performance, and the configuration of plugins.
During installation, the Nessus user license agreement should be carefully read and accepted. Then, depending on the preferences of users, the network port assignment and other network configuration options are determined. This stage is of critical importance, which will directly affect the interaction of the scanning process on the network.
As a final step, Nessus needs to be updated after successful installation and the corresponding plugins (plugins) need to be downloaded. These plugins contain various vulnerabilities and system weaknesses and are regularly updated by Tenable. After the installation and update processes are completed, the system administrator can proceed to the process of creating and planning the necessary scanning policies. These policies should be organized according to the security needs and goals of the organization.
Basic Use of Nessus
Nessus is a comprehensive tool used in network security scanning and is basically used in three steps. First, while completing the installation and configuration phases, policies are determined for scans in accordance with the needs of the user and the organization.
In the next stage, target network segments, systems or devices are scanned according to the determined policies. During the scan, different controls are applied, such as activity, port scanning, detection of vulnerabilities and analysis of configuration errors. As a result of the scan, Nessus turns its findings into a report with their details.
In the last step, the user learns about the vulnerabilities by reviewing the report submitted by Nessus and starts to fix them by prioritizing. This report also serves as the basis for developing appropriate corrective strategies.
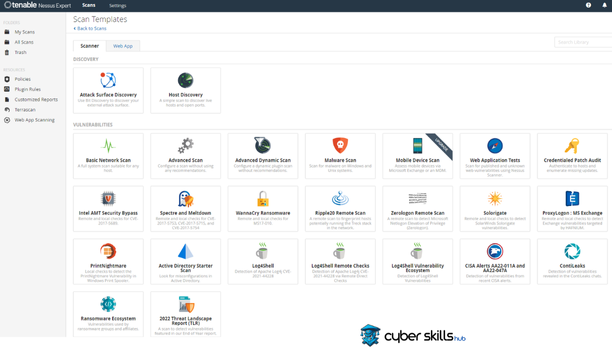
Creation of Screening Policies
Nessus provides customizable browsing policies.
In order to create an effective screening policy, first of all, the needs of your organization must be understood in depth. During this process, it is necessary to decide which network assets will be scanned, which types of vulnerabilities will be focused on, and how the frequency of scanning will be. In addition, the methods and options to be used during the scan should also be determined.
The policy skeleton is created and elaborated.
Various templates and recommended configurations are available for the creation of scanning policies. In this way, users can make their policies ready to detect the most up to date security vulnerabilities by using regularly updated threat databases.
The Nessus scanning policies determine the places where they need to be updated.
While your organization’s scanning policies are being established, it’s crucial to review and update them regularly. This is crucial for preparing for changes in the threat landscape and newly discovered vulnerabilities. By 2024, Nessus can effectively implement these updates by integrating with the most prevalent threat intelligence provided by the security community.
Network Vulnerability Scan
Network vulnerability scanning is performed to identify system weaknesses in accordance with established policies and configurations. In this way, the status of the system is evaluated against possible cyber threats.
- Determining the Network Topology: In order to increase the effectiveness of scanning, it is necessary to correctly understand the physical and logical structure of the network.
- Creation of a Screening Policy: It should be decided which services, which ports and protocols will be covered by the scan.
- Updating the Vulnerability Database: Keeping the vulnerability signatures that will be used during scanning constantly up to date provides better protection against threats.
- Steps to Follow During the Scan: Following a sequence while the scanning process is being planned contributes to making the process efficient and orderly.
- Evaluation and Reporting of Results: The analysis of the findings obtained and their reporting are important for the correction of security vulnerabilities.Nessus, a professional IP scanning tool, offers a wide range of possibilities for network vulnerability scanning and provides a complete scan with a regularly updated vulnerability database.
The results should be examined and processed in detail in order to strengthen the internal security policies of the organization and take the necessary measures. In this way, the process acquires a result oriented and action-oriented structure.
In addition to Nessus scans, What is a Proxy? Ways to Hide Your IP Address you can find more information on IP security and anonymity in our article.
Practical Tips and Best Practices
Determining the frequency of scanning is vital in the constantly changing cyber threat environment. By conducting regular Nessus scans on a weekly or monthly basis, you can take precautions against newly discovered vulnerabilities. In addition, increasing the frequency of scanning, especially for critical systems, and dynamically updating measures such as firewall rules will maximize your level of protection.
It is also especially important to correctly determine the scope of the screening. For example, creating different scanning profiles for separate segments, such as production networks and management networks, provides the possibility of vulnerability detection according to the specific risks and needs of each network segment.
To strengthen cyber security practices Cyber Security For Small Businesses you can take a look at the suggestions contained in our article.
Interpretation of the Scan Results
The reports obtained as a result of Nessus scans require a detailed analysis and evaluation process. This process involves sorting the detected vulnerabilities according to their severity and impact areas.
The findings in the reports can sometimes cover hundreds of vulnerabilities. Each of them should be prioritized.
In addition to these vulnerabilities, to get detailed information about security vulnerabilities Examples of Cyber Attacks: Which Types are Dangerous? you can review our article.
The priority order of vulnerabilities is determined depending on the potential impact of these vulnerabilities on the business and the likelihood of their exploitation. Priority vulnerabilities are quickly fixed, while others can be ranked as less critical. In this process, the distinction between false positives (false positives) and false negatives (false negatives) is also of great importance.
On the other hand, the correct interpretation of the scan results requires a strategic approach to strengthen the organization’s cybersecurity posture. After the identified vulnerabilities are examined in detail, improvement works are planned and implemented. Instead of seeing the scan results as just a “checklist”, consider them as an opportunity to deeply understand and improve your security structure. This allows security teams to take a proactive approach and create an effective defense structure against cyber threats.
Prioritization of Vulnerabilities
It is vital that the vulnerabilities detected in the cyber security infrastructure of an organization are properly prioritized. The main criteria that should be taken into account when prioritizing vulnerabilities are:
- The Level of Exploitability: Whether the vulnerability is being actively exploited.
- Accessibility: The ease with which the attacker can access the vulnerability.
- Impact Area: The breadth of potential damage that the vulnerability could cause to the system.
- Correction Cost: The resources and time necessary to correct the vulnerability.
- Impact on Business Processes: Potential effects of the vulnerability on transactions and data integrity.
With the right prioritization, it is possible to quickly address the most critical vulnerabilities.
This prioritization process is the cornerstone of vulnerability management processes and is especially mandatory in large-scale networks. There may be many vulnerabilities in a system; classifying them in this way allows security teams to use their resources in the most effective way.
Frequently Asked Questions About Nessus
What is Nessus?
Nessus is a vulnerability scanning tool developed by Tenable Network Security and constantly updated. It is used to detect security vulnerabilities and is considered an industry standard.
How Does Nessus Work?
Nessus detects security vulnerabilities by scanning devices on the network in accordance with predefined policies. It provides security status reports by performing detailed scans on servers, network devices, systems and applications.
How is the Installation of Nessus Done?
The installation of Nessus starts with the execution of the downloaded installation file and is usually routed through an installation wizard. After the user name and password are created, the license key must be entered.
What are the Necessary System Requirements for Nessus?
System requirements for Nessus to run properly include a compatible operating system (Windows, Mac OS, Linux), sufficient CPU performance and RAM, ample disk space, and a stable network connection.
How are Nessus Scans Performed?
Nessus scans are performed in accordance with the established policies. During the scan, devices and services on the network are scanned, vulnerabilities and configuration errors are identified, and the findings are presented in detailed reports.
How are the Nessus Scan Results Interpreted?
The scan results are analyzed in detail so that prioritization can be made. The findings are sorted by considering the impact area of the vulnerability, the level of exploitability and the potential effects on business processes.
How are Nessus Vulnerabilities Prioritized?
The prioritization of vulnerabilities is carried out according to criteria such as the level of exploitability, accessibility, domain, cost of correction and impact on business processes. This process forms the basis of vulnerability management strategies.







