Currently Empty: $0.00

Server-Side Request Forgery (SSRF) allows an attacker to misuse a server’s resources, as it can act like a locked room behind closed doors.
SSRF attacks can be likened to a Trojan horse scaling city walls as it attempts to control your systems from the inside out; they can be unexpected and devastating.
Overview of SSRF Vulnerability
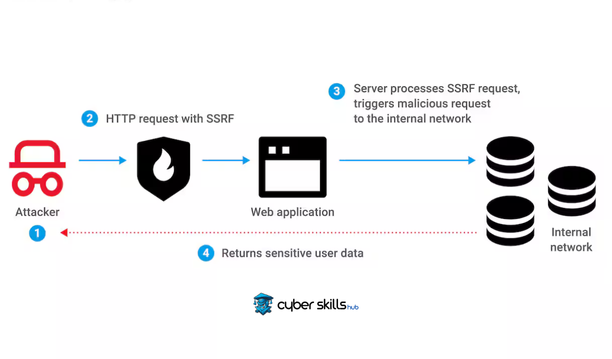
An SSRF vulnerability allows a malicious user to bypass security boundaries by causing the server to act as a client and connect to an internal network that is typically restricted. This can include access to systems and data on private networks, making the risk very high.
When an unauthorized client opens a path to access a service that it should not be able to access, SSRF attacks come into play. An attacker can send incorrect commands to the server via an improperly validated URL and attempt to redirect these commands to another system on the internal network. Using this method, sensitive data can be accessed or system commands that cause damage can be executed.
The most common SSRF attack vectors are web applications’ interactions with external systems. In particular, APIs used by web applications to retrieve or send data can become vulnerable to attack if they are not sufficiently secure, allowing attackers to infiltrate the system through these vulnerabilities.
To strengthen your web applications and protect them against potential security threats, you can read our article Programming Expert for Web Applications.
Definition of SSRF
Server Side Request Forgery (SSRF) is a specific type of security vulnerability that allows a server to be compromised by external sources.
SSRF attacks have the potential to infiltrate systems without access permissions, and this threat is significant.
Malicious actors can use the SSRF vulnerability to gain client-like access to the server’s internal networks or sensitive APIs. This leads to unauthorized data access and, consequently, significant security breaches.
SSRF defense strategies include security practices such as input validation, whitelisting, and awareness of common risks. These measures are aimed at increasing system security by minimizing attack vectors.
To better understand the potential impact of SSRF attacks on your system, you can check out our courses in the field of Cyber Security.
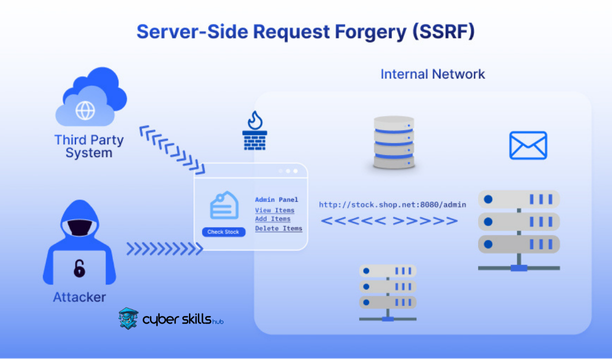
SSRF Attack Scenarios
A common scenario in SSRF attacks is that attackers send requests to different server services with the aim of accessing sensitive information. These requests are usually triggered by unverified user input.
Attackers typically detect these vulnerabilities using automated tools and act deliberately based on this information.
In an attack targeting internal networks, an attacker who discovers an SSRF vulnerability attempts to infiltrate the system as a client through services specific to the local network. In this case, sensitive data can be accessed through internal communication protocols and applications, even though this data is not supposed to be accessible from external networks.
In addition, SSRF can also be detected in attacks carried out via system commands used for remote code execution. If an application includes URLs that can be controlled by the user in system commands without filtering, this could give attackers the opportunity to execute arbitrary code on the server. Such scenarios are particularly possible with “magic URLs” that have permission to execute commands at a high privilege level on web servers.
If you want to learn about other types of dangerous cyber attacks in addition to SSRF attacks, you can check out our article Cyber Attack Examples: Which Types Are Dangerous?
Analysis of SSRF Attack Vectors
The analysis of SSRF attack vectors is performed by security experts to reduce the attack surface and close vulnerable points as much as possible. SSRF typically exploits poorly designed or incorrectly implemented remote resource requests in web applications. This gives the attacker control over services and interfaces within the target system, which can lead to information leaks or denial-of-service attacks.
Determining the scope of SSRF attacks is important in terms of identifying the likelihood of success and potential damage of the attack. The ability to bridge internal and external networks makes SSRF particularly dangerous. Although such attacks often require high levels of authorization, they have the potential to bypass security measures by gaining access to critical components such as local file access, database queries, and administrative tools. Therefore, each service and protocol should be thoroughly reviewed and risk assessed in terms of SSRF.
Impact of SSRF on Systems
Server Side Request Forgery (SSRF) attacks can cause serious damage to target systems. The extent of this damage varies depending on the structure of the system and the depth of the attack.
- Information Leakage: Risk of exposure of the targeted server’s internal network structure and sensitive information.
- Unauthorized Access: Allows the attacker to access certain unauthorized services on the target system.
- Denial of Service (DoS): Consuming system resources by sending heavy traffic or misusing targeted services.
- Malware Distribution: Placing malware on other servers within the internal network.
- Configuration Changes: Misleading or disabling the system as a result of changing or corrupting sensitive configurations.
These effects lead to a weakening of inter-system security boundaries and the potential for propagation to other services and systems within the internal network.
Especially in today’s world where cloud technologies are heavily used, the potential consequences of SSRF attacks can be catastrophic, and this attack vector is a security threat that is largely overlooked. For this reason, the importance and necessity of SSRF defense must be constantly emphasized.
Common SSRF Vulnerabilities
One of the common causes of SSRF vulnerabilities in web applications is the failure to properly validate user-entered URLs. This oversight leads to uncontrolled network requests and provides opportunities for attackers. Interaction with APIs and service infrastructures is among the potential risks for such vulnerabilities. Failure to filter untrusted inputs in server-to-server communication brings security vulnerabilities.
Open source software typically comes with predefined security settings. However, these settings can create security vulnerabilities when customized or misapplied. Weak inter system security boundaries, misconfigured network firewalls, and security lists can enable SSRF attacks.
Proxy servers and gateways are frequently targeted due to their lack of filtering and authentication mechanisms. Custom protocols and service endpoints can also lead to vulnerabilities if proper security measures are not taken. OAuth and other authentication mechanisms can be exploited to take advantage of security vulnerabilities.
Metadata services and cloud management tools are risk factors for information leakage and access control violations, especially in examples running in cloud environments. In cases where access controls are weak, attackers may exploit these vulnerabilities to gain deeper access to the system. Therefore, it is important to remember that the “least privilege” principle and regular security reviews are the most effective defense methods against SSRF vulnerabilities.
SSRF Detection and Prevention Methods
Various methods have been developed to detect SSRF attacks and protect against them. By using active and passive scanning tools and carefully examining the requests sent by servers, potential SSRF patterns can be identified. Using a modern WAF (Web Application Firewall) is critical for protecting systems from such exploits. Measures such as URL filtering, blocking malicious IP addresses and known dangerous protocols, and allowing access only to whitelisted services provide effective protection. Properly configuring the network to limit internal and external service calls, and ensuring developers adhere to secure coding principles, are important steps in preventing SSRF vulnerabilities. Additionally, the regular use of automated security scanners and code review tools enables the early detection of potential vulnerabilities.
To learn more about methods of protection against SSRF attacks and understand how firewalls work, please refer to our article What is a Firewall and How Does it Work?
Use of Vulnerability Scanning Tools
Vulnerability scanning tools are designed to automatically detect security vulnerabilities in systems. Regular and conscious use of these tools by users can be an effective method for detecting potential SSRF vulnerabilities.
- OWASP ZAP: An open source scanning tool, ZAP detects security vulnerabilities with its passive and active scanning capabilities.
- Burp Suite: The preferred choice of professional security experts, Burp Suite offers highly effective scanning performance with its wide range of modules.
- Nessus: Nessus, a tool used for enterprise-level vulnerability and compliance scans, stands out for its detailed reporting features.
- Acunetix: Used in security scans of web applications, it can detect a wide range of vulnerabilities, including SSRF.
These tools strengthen the security infrastructure by supporting defense layers such as firewalls and built-in security measures. Performing scanning processes on a regular basis plays a key role in enhancing security.
Despite the use of advanced scanning tools, fixing the vulnerabilities detected by these tools and correcting configuration errors in systems is an integral part of security efforts. After vulnerabilities are fixed, they must be verified by performing rescans.
Firewall and Server Settings
Firewalls monitor network traffic and prevent unwanted or harmful content from accessing the system. They are particularly important for protecting against SSRF attacks. In this process, firewalls must be configured appropriately. Determining which requests and responses will be accepted forms the basis of the configuration.
Network firewall rules should be examined in detail, and only requests from secure sources should be allowed. To prevent SSRF attacks, the structure and targets of incoming requests should be closely examined. For example, requests made to internal networks or management panels should be blocked or only allowed for specific users.
It is also possible to prevent SSRF vulnerabilities by implementing strict controls and restrictions in server configuration files. Requests to servers should be checked to ensure they come from expected addresses, and access restrictions should be imposed for suspicious or unknown endpoints. Such access restrictions can prevent the server from being exposed to malicious or manipulated requests.
In addition, access to server services via local network and loopback addresses should be blocked. This makes it nearly impossible to access internal server configurations through SSRF attacks. Creating separate network access policies for each service and isolating services within these policies maximizes server security.
Finally, firewall and server configurations must be reviewed and tested whenever changes are made. The continued security benefits of these configurations are verified through these steps. Improvements and regular reviews are critical to protecting against sophisticated attack vectors such as SSRF.
Best Practice Recommendations and Resources
To prevent SSRF attacks, application firewalls (WAF) must be configured effectively. Defining rules that are specifically sensitive to SSRF attack vectors enables attack attempts to be detected and blocked at an early stage. In addition, secure coding practices and strengthening input validation mechanisms play a vital role in closing potential vulnerabilities.
As a source, security standards and guidelines such as OWASP’s Server Side Request Forgery Prevention Cheat Sheet should be used as a basis. In addition, MITRE’s Common Attack Pattern Enumeration and Classification (CAPEC) and Common Vulnerabilities and Exposures (CVE) databases are useful sources of information on current threats.
Security Network Configuration
Firewalls protect the boundaries of the network by controlling all incoming and outgoing traffic. In addition, SSRF prevention strategies are also critical in this configuration. Firewall rule sets should be updated regularly to identify unexpected requests and take action against them.
Network segmentation allows sensitive systems to be isolated. With this method, interaction between development, testing, and production environments is kept under control.
Deep packet inspection (DPI) can detect SSRF attack attempts by analyzing the content of network traffic. DPI solutions are used to identify and stop malicious data flows coming through network traffic; this approach provides an extra layer of security at the network layer.
In addition, an effective boundary must be established between the reliable and unreliable components of the network. This boundary should be reinforced with penetration tests and regular monitoring, and each new update to the network configuration should be carefully evaluated for potential vulnerabilities. In this way, a consolidated defense strategy can be established against SSRF threats using the principles of “least privilege” and “defense in depth.”
Current Security Updates and Training
It is essential to take a proactive approach to SSRF threats.
Due to the constantly evolving nature of the cybersecurity environment, it is vital to stay up to date with security updates and be educated on how to deal with SSRF attacks. Regularly reviewing current security policies enables rapid adaptation to new threat vectors and the ability to neutralize them. In particular, it is important to remain vigilant against sophisticated attacks such as SSRF and to quickly integrate innovations that strengthen the defense of the infrastructure.
Preventing SSRF attacks is possible through training.
Comprehensive training aims to raise awareness of emerging threats and, more importantly, encourage security professionals to continuously develop their knowledge and skills. This is a critical step in keeping pace with changes in the cybersecurity landscape and effectively mitigating complex vulnerabilities such as SSRF.
Combating SSRF attacks is a constantly evolving process.
Therefore, security professionals’ commitment to a continuous learning and application process remains valid even in 2024. In this context, keeping up with new security tools, defense techniques, and training programs is essential for maintaining an innovative approach and strengthening one’s position in cybersecurity.
Frequently Asked Questions About SSRF
What is SSRF?
Server-Side Request Forgery (SSRF) is a security vulnerability that allows an attacker to manipulate another server to gain access to closed networks or restricted resources. Attacks are typically carried out using misvalidated or unfiltered inputs.
How Do SSRF Attacks Occur?
SSRF attacks begin with malicious URLs being sent to a web application or API. These URLs cause the server to make a request to a resource controlled by the attacker, which can lead to data leakage or denial of service.
What measures can be taken to prevent SSRF?
To prevent SSRF, methods such as input validation, tightening firewall settings, and accepting only requests from secure sources can be implemented. In addition, adopting a whitelist approach and training developers on secure coding techniques will also be effective.
What Tools Are Used for SSRF Detection?
Security scanning tools such as OWASP ZAP, Burp Suite, Nessus, and Acunetix can be used to detect SSRF vulnerabilities. These tools help strengthen security posture by automatically identifying vulnerabilities in the system.
What is the best way to protect against SSRF attacks?
The best way to protect against SSRF attacks is to adopt a multi-layered security approach. This should be supported by URL filtering, IP address blocking, firewalls, and WAF (Web Application Firewall) usage. In addition, regular security updates and training are vital for protection against attacks.
How Should a Firewall Be Configured Against SSRF?
The firewall against SSRF attacks should be configured to allow access only to specific services and addresses. Requests to sensitive targets such as internal networks or management panels should be specifically restricted or completely blocked.







