Currently Empty: $0.00

Kafka stands out as an extraordinary data transfer platform; it provides seamless transmission, especially in big data workflows.
The use of Kafka in cybersecurity plays a major role in accelerating threat detection and incident response processes – providing a critical infrastructure for instant data analysis and distribution.
Kafka and Real-Time Threat Detection
Kafka is a vital tool for real-time threat detection because it requires continuous monitoring of cyber incidents and data flows across the network. When integrated with advanced analysis and protection mechanisms, Kafka provides the perfect data backbone for timely alerts and in-depth threat analysis. Especially given the ever expanding volumes and complexity of data, a properly configured Kafka deployment is critical for monitoring and managing cybersecurity incidents.
Detection of anomalies and suspicious activity is made possible by Kafka’s ability to quickly process large data streams. Furthermore, for threat hunting teams, the platform provides low latency and high accuracy alerts, reducing human intervention. A Kafka powered infrastructure becomes a centralized event processing hub where logs, event records and sensor data collected from different network layers are combined. This transparency and speed oriented structure offers significant advantages in deciphering complex cyber attack scenarios.
Monitoring Anomalies with Log Management
Kafka’s distributed processing capabilities make it possible to analyze large data sets in real time during log management.
Kafka’s capacity to manage high-volume data streams is a groundbreaking breakthrough in cybersecurity.
In this analysis process, logs from different system sources based on behavioral modeling are compared, which allows for quick detection of irregular activities and security breaches. A well-structured Kafka system supports instant information exchange for threat detection.
Finally, with Kafka’s effective log management, network security analysts better understand threats, correlate them with cross-examination and respond quickly to incidents, which strengthens the overall security posture.
Stream Processing for Security Events
For the detection and analysis of cyber security incidents, Kafka stands out as an efficient stream processing tool. Fast data ingestion, flexible scalability features and high processing speed make Kafka an ideal solution. It is critical for immediate detection of security breaches and rapid deployment of response strategies.
As a stream processing platform, Kafka integrates security events from heterogeneous data sources. This provides broad visibility across the entire protected infrastructure. Multidimensional analysis techniques are supported in the processing and interpretation of events, so that complex threat scenarios can be quickly deciphered and proactive protection can be provided.
With time series data processing and behavioral analytics, Kafka forms a fundamental building block for continuous security monitoring systems. The ability to detect anomalous behavior and analyze traffic coming through firewalls increases the effectiveness of security operations centers (SOCs). With the integration of machine learning and artificial intelligence algorithms, Kafka also becomes an indispensable tool for advanced threat hunting activities.
In security incident response processes, Kafka’s fast and reliable messaging capabilities enable coordinated information flow between different security solutions and team members. The integration of automated incident response mechanisms and orchestration tools enables timely and effective interventions. This approach also benefits post-incident analysis, providing a clearer understanding of the origin and scope of incidents.
A special feature of Kafka based systems is their role in the development of cyber security simulations and automated incident detection systems. Thanks to their real-time data transfer capabilities, Red Team activities and penetration test scenarios can be simulated using up to date threat data. This provides the opportunity to test defense mechanisms and continuously improve security posture.
In conclusion, Kafka is an indispensable tool for cybersecurity operations with its ability to process, integrate, and analyze the flow of security events in real time. Security infrastructures enhanced with Kafka deliver superior performance in terms of rapid adaptation to dynamic threat environments and management of complex threats.
For more information about flow processing platforms, please refer to our article titled “Cyber Security Training: Become an Expert in the Industry.”
Kafka and Network Security
Kafka plays a central role in network security monitoring and management. By efficiently processing high-volume data streams, it provides an ideal platform for threat detection and analysis.
The detection of malicious traffic patterns and anomalies is greatly enhanced by Kafka’s real-time data processing capabilities. This allows security analysts to analyze traffic and detect and respond to potential security breaches more quickly.
Kafka also offers cross-platform compatibility for network security integrations, enabling synchronization between different security solutions and the creation of an effective network defense ecosystem.
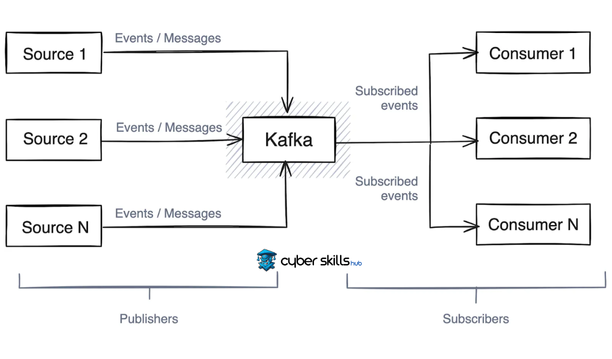
Traffic Analysis and Anomaly Detection
Kafka’s parallel data processing capability is critical in traffic analysis. It provides an ideal structure for real-time detection of anomalies.
The rapid detection of malicious network activity and anomalies is made possible by Kafka’s fast data processing and analysis capabilities. Advanced algorithms and machine learning models can work effectively on this platform.
In anomaly detection processes, Kafka’s flexible scalability and high throughput capacity are very important. Data from large network infrastructures is easily processed by Kafka and prepared for analysis.
Stream processing, supported by Kafka, enables real-time network traffic analysis and identification of potential threat vectors. This allows for in-depth traffic analysis even in short time intervals.
Kafka enables complex queries and long-term trend analysis on large data sets by integrating with SIEM systems. This integrated approach also makes threat hunting more effective.
Real Time Detection of DDoS Attacks
DDoS attacks can be detected instantly with Kafka.
Thanks to Kafka’s real-time data processing capabilities, DDoS attacks can be detected and analyzed at extraordinary speeds. Continuous monitoring of high-volume data streams enables rapid detection of traffic patterns that deviate from normal. This critical data is immediately communicated to security systems, enabling fast and effective intervention.
DDoS patterns are quickly detected and isolated.
Kafka’s scalability makes it easy to coordinate heavy data flows in large network structures. With its high-speed data routing and aggregation capabilities, it is possible to isolate and analyze abnormal traffic directed to the network during a DDoS attack.
The attack process is examined in detail.
Real-time traffic analysis can be sustained seamlessly thanks to Kafka. The Kafka platform tracks changes in traffic flow down to the smallest detail from the moment a DDoS attack begins, feeding this information into security protocols that take action. This minimizes the impact of attacks.
Kafka’s Role in Data Protection
When discussing Kafka’s role in early warning systems against security breaches, it is important to note that while latency in internal communication is minimized, the ability to analyze large data sets is also enhanced. These features enable the construction of advanced, dynamic, and responsive data protection mechanisms. In a high-volume and widespread network structure, Kafka contributes to the rapid detection of abnormal behavior by managing continuous data flow, thereby enabling the prevention of critical security incidents such as data leaks.
Kafka’s real-time stream processing capability optimizes the protection of sensitive data and the monitoring of suspicious behavior. Working in tandem with big data analytics, Kafka instantly detects security incidents and coordinates appropriate actions, providing a powerful infrastructure that reinforces organizations’ proactive security posture. This infrastructure not only helps detect data leaks at an early stage, but also reduces response times to potential data breaches.
Encryption and Tokenization of Sensitive Data
Sensitive data is one of the most important assets that must be protected in cybersecurity. Kafka plays a vital role in effectively protecting this data. Ensuring that data is encrypted while in transit is one of Kafka’s data security protocols.
Kafka’s distributed architecture and high performance enable the encryption and tokenization of sensitive data. During the data flow process, encryption and tokenization are performed in real time. This ensures that confidentiality is maintained during the data journey and creates an effective line of defense against unauthorized access. Encryption and tokenization not only ensure data integrity and confidentiality, but also meet compliance requirements.
Tokenization of sensitive data elements is particularly important for compliance with regulations such as PCI DSS. Kafka facilitates compliance with these regulations by replacing critical data such as card details with tokens and storing the actual data securely. Tokenization reduces security risks at every stage of data processing and minimizes the likelihood of data breaches.
By leveraging Kafka’s stream processing capabilities, sensitive data can be encrypted using continuously updated encryption algorithms. This provides a significant advantage in today’s world, which requires a dynamic security strategy. Innovative encryption and tokenization methods, when integrated with Kafka, provide proactive protection against current threats while also accelerating adaptation to prepare for future cybersecurity needs.
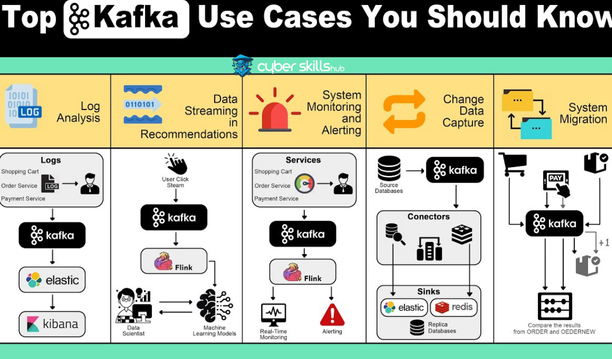
Centralized Analysis of Access Logs
Access logs play a critical role in understanding network security, application performance, and user behavior. Kafka enables these logs to be collected in a central location. This allows security analysts to easily process and interpret data from a wide variety of sources.
When creating a unified log management system, Kafka’s ability to process large amounts of data quickly and reliably comes to the fore. In addition, its scalable architecture allows it to seamlessly manage increasing log volumes in the system. Kafka’s ability to process logs from different network layers as a single stream makes it easy to analyze intense data flows.
Access log analysis is critical for detecting suspicious behavior and creating early warning systems against network attacks. Kafka enables fast processing of these logs, integration of different data types, and real-time analysis. By using the Kafka Stream API, predefined patterns for security breaches are matched, shifting from a reactive approach to a proactive one in attack detection processes.
In these processes, Kafka centrally manages the collection, cleansing, transformation, and storage of logs from sources. Tools such as Kafka Connect and Kafka Streams make large volumes of data streams more meaningful by filtering them temporally or functionally. In addition, with its complex event processing (CEP) capabilities, Kafka enables more in-depth analysis of log data.
Ultimately, access log analysis systems built using Kafka help cybersecurity experts make data-driven decisions. They also significantly reduce adaptation and response times in the face of an ever-evolving threat landscape.
Kafka and Violation Detection Systems
Kafka’s high-performance and scalable architecture plays a vital role in intrusion detection systems. Its ability to process large amounts of security events and logs in real time is critical for early detection of security breaches and rapid sharing of threat intelligence. Especially in distributed systems, Kafka is used to normalize data from monitoring tools written in different languages and running on various platforms, and to create a central event monitoring point. This enables rapid response to events and effective management of complex security scenarios.
Intrusion Detection and Prevention
Kafka manages critical data flows for intrusion detection in cybersecurity infrastructures and provides a central event monitoring point. This structure enables security events to be detected in a timely manner.
Early detection of a cybersecurity breach prevents the threat from spreading. Kafka plays an important role in this process.
To detect and prevent leaks, Kafka’s real-time data processing capabilities and high-volume data integration enable security analysts to respond to incidents immediately. By combining data from heterogeneous systems, Kafka makes it possible to detect anomalies and potential threats at an early stage.
In intrusion prevention strategies, Kafka functions as a platform that collects and analyzes threat data from multiple sources, forming the backbone of the security infrastructure. Its real-time data processing capabilities enable the filtering of large data sets to extract important information, generate meaningful security alerts based on this information, and proactively prevent potential breaches. Additionally, this platform has the potential to detect even “zero day” attacks through integrated artificial intelligence and machine learning models.
Firewall and Antivirus Integration
Kafka enables centralized management of firewalls and antivirus systems. This facilitates the effective implementation of security policies.
Firewall logs and antivirus alerts are continuously collected via Kafka and stored in a central pool. This creates an ideal environment for consolidating and analyzing threat intelligence.
These collected data are processed in real time thanks to Kafka’s stream processing capability. This allows abnormal behavior and potential threats to be quickly detected and addressed.
This integration provided by Kafka accelerates incident response processes and enables faster decision-making in response to security threats. Threat hunting activities are also supported by the ability to analyze multiple incidents instantly.
As a result, Kafka enhances defense mechanisms against cyber threats by increasing the interaction between firewall and antivirus systems. This approach significantly improves the efficiency and effectiveness of security operations.
Frequently Asked Questions About Kafka
What is Kafka and how is it used in cybersecurity?
Kafka is a data transfer platform capable of managing high-volume data streams. It is used in cybersecurity to accelerate threat detection, log management, and incident response processes, thereby enabling real-time data analysis and distribution.
What is Kafka’s role in real-time threat detection?
Kafka provides real-time threat detection by continuously monitoring data streams. When integrated with advanced analysis and protection mechanisms, it provides timely alerts and in-depth threat analysis.
How does Kafka provide log management?
Thanks to Kafka’s distributed processing capabilities, it analyzes large data sets in real time. This enables rapid detection of security breaches and irregular activity.
What are the advantages of using Kafka in network security?
Kafka efficiently processes high-volume data streams to quickly detect malicious traffic patterns and anomalies. It also facilitates the integration of different security solutions by offering cross-platform compatibility.
How to detect DDoS attacks with Kafka?
Kafka’s real-time data processing capabilities enable DDoS attacks to be detected instantly. By continuously monitoring high-volume data streams, abnormal traffic patterns are quickly identified and immediately reported to security systems.
What is the importance of Kafka in data protection?
Kafka increases the effectiveness of early warning systems by enabling rapid analysis of large data sets. It works in conjunction with security protocols such as encryption and tokenization of sensitive data, thereby preventing data leaks.
What are the benefits of Kafka in analyzing access logs?
Kafka enables security analysts to quickly and effectively process this data by collecting access logs in a central location. This plays a critical role in creating early warning systems against network attacks.
What is Kafka’s function in violation detection systems?
Kafka enables early detection of security breaches by instantly processing large amounts of security events and logs. It normalizes data from various monitoring tools to create a centralized event monitoring point.
What is Kafka’s role in firewall and antivirus integration?
Kafka provides centralized management of firewall and antivirus systems, facilitating the effective implementation of security policies. It also provides an excellent environment for consolidating and analyzing threat intelligence.







