Currently Empty: $0.00

Business Logic Vulnerability refers to unique flaws in the design of applications and systems. These vulnerabilities can be exploited by allowing attackers to perform unauthorized operations.
These vulnerabilities are often undetectable by automated tools.
It should be at the heart of proactive defense strategies, as penetration tests and automated scanning tools can easily miss such vulnerabilities.
What is Business Logic?
Business logic describes the basic functions and workflows of an application or systems. This refers to how users interact within the system to achieve a specific goal.
From customer registration to purchasing, data validation to access controls, every application has unique business logic. If the business logic is not designed correctly, it can lead to security vulnerabilities and unintended consequences, so the security of systems must be built on this logic.
Business logic not only refers to technical operations, but also includes the user experience and workflow, which are shaped by the goals and policies of the business.
You can visit our ‘Cyber Security Fundamentals Training’ course to better understand the business logic and create secure systems.
Basis for Business Logic Vulnerability
Business logic vulnerability describes situations where the expected behavior of an application or system can be exploited in malicious ways. These exploits have consequences that are contrary to the system’s purpose. These vulnerabilities are an important part of security measures and require a deep understanding of workflows. Any manipulation to circumvent business procedures can be an example of a business logic vulnerability.
Attackers identify and exploit vulnerabilities by analyzing the business logic in systems. A business logic vulnerability is caused by the misuse of certain functions and, unlike classical security vulnerabilities, involves the misuse of normal operations within the system.
Business logic vulnerabilities mean that systems are open to the most clever and creative exploits.
Identifying business logic vulnerabilities is often not possible with automated tools and requires expert observation. Since such vulnerabilities are specific to unique business procedures, they may not be detected by standard security tests. Understanding and preventing business logic vulnerabilities has become essential to protect systems.
Types of Business Logic Vulnerability
Business logic vulnerabilities are vulnerabilities that typically target specific business processes as well as the underlying rules for which systems are designed. These vulnerabilities involve system-specific risks and can be illustrated with specific examples due to their diversity.
- Authentication Bridges: Vulnerabilities that allow users to bypass authentication steps.
- Session Management Violations: Problems caused by the misuse of session tokens or cookies.
- Parameter Manipulation: Manipulation of user input or URL parameters to create unwanted effects on the system.
- Escalation: Vulnerabilities that allow unauthorized users to enter the system and perform authorized operations.
- Workflow Bypass: Finding ways to bypass or shortcut processes that would normally require a series of steps and validations.
- Side Channel Attacks: Attempting to access sensitive information by monitoring system performance changes.
To develop effective strategies against business logic vulnerabilities, read ‘Red Teaming: The Power of Red Teaming‘ to develop effective strategies against business logic vulnerabilities.
Such vulnerabilities arise through the abuse of the resilience of systems, enabling users to exploit abnormal behavior.
Effectively managing business logic vulnerabilities requires in-depth process analysis and thorough auditing of the software’s functional flows. For information security professionals, identifying and remediating these vulnerabilities is a constant challenge and an important part of their specialty.
Causes of Business Logic Vulnerabilities
Business logic vulnerabilities are often caused by a lack of understanding of how applications work and the business processes used. During the design of complex systems that focus on unique workflows, developers’ assumptions about business logic and unrecognized scenarios can create vulnerabilities. In addition, automated testing processes that do not consider non-standard behavior when testing software can lead to such vulnerabilities being overlooked. By recognizing these shortcomings, attackers can discover methods to exploit systems. Insufficiently comprehensive security tests and failures in monitoring processes facilitate the emergence of business logic vulnerabilities. On the other hand, rapidly evolving technologies and ever-changing business requirements can lead to vulnerabilities in security strategies that are not constantly updated.
Development Errors
Business logic vulnerabilities are the result of mistakes made during application development.
- Lack of critical control mechanisms: Inadequate or missing security controls.
- Inadequate data validation processes: Failure to properly validate input data can lead to harmful or erroneous transactions.
- Faulty authentication mechanisms: Poorly designed session management sets the stage for attacks.
- Inadequate authorization controls: Improper implementation or disregard of authorization mechanisms.
- Coding and logic errors: Logic errors in the design phase and deficiencies in coding.
- Misleading security assumptions: Assumptions made during the development process that are assumed to be secure, but are vulnerable to attack.
These errors are often the result of skipping detailed testing and audits.
Conducting thorough and detailed security testing is of paramount importance in preventing such vulnerabilities.
Shortcomings of Test Processes
Deficiencies in testing processes lead to business logic vulnerabilities not being detected. Failure to perform thorough testing can result in vulnerabilities being missed. Business logic vulnerabilities are often complex problems that are difficult to detect by typical security controls. This implies that focusing testing processes solely on technical security controls may be insufficient. Customized and layered testing methods are essential for effective detection of such vulnerabilities.
In ever-changing technological environments, security testing processes need to be constantly updated. Regularly assessing whether existing test processes are effective against current threats is a fundamental part of an agile security approach. Business logic vulnerabilities can create new security vulnerabilities in an ever-evolving threat landscape, and therefore it is critical to keep testing processes up to date.
Although automation in testing processes saves time and resources, it may be insufficient to detect some vulnerabilities. In particular, detecting business logic vulnerabilities requires human-centered analysis that automation cannot detect. Extensive manual testing is imperative to understand complex business processes and uncover potential vulnerabilities.
Not only is the scope of the tests broad, but it is also vital to dig deeper. Instead of just identifying vulnerabilities on the surface, it is necessary to perform in-depth analysis of how the application works. Understanding business logic vulnerabilities is possible not only from a technical perspective, but also with a holistic understanding of business processes.
Thus, the shortcomings of testing processes may not only be due to the use of inadequate tools, but also to a lack of security culture and complexity of the processes. Security testing should be treated not only as a technical activity, but also as a continuous process and understanding development activity. In this context, identifying business logic vulnerabilities is an important part of a holistic security approach.
Identifying Business Logic Vulnerabilities
The process of detecting business logic vulnerabilities requires a series of detailed analysis and extensive manual testing. Beyond advanced automated scanning tools, security professionals need to systematically examine the application’s business logic, as well as workflows and user behavior. This includes both the simulation of unpredictable user scenarios and the evaluation of unexpected input combinations. The preparation of customized test cases is essential to illuminate vulnerabilities in specific business processes, and such vulnerabilities can only be detected through a thorough analysis of the entire business process.
Manual Inspection Techniques
Identifying business logic vulnerabilities is a process that requires insight and needs to be handled with care.
- Process Flow Analysis: Identifying potential vulnerabilities by following the logical steps of workflows.
- User Behavior Scenarios: Straining the system by simulating real-world user behavior.
- Input/Output Analysis: Testing different types of inputs in unexpected and edge cases.
- Authorization Verification Tests: Testing security controls by attempting to bypass users’ permission levels.
- Fault Detection Tests: Testing abnormal or borderline cases to find logic errors.
These techniques allow to examine each aspect of the practice from the inside out.
A structured and methodical approach facilitates in-depth understanding and tracking of vulnerabilities.
Use of Automated Screening Tools
Business logic vulnerabilities are specific.
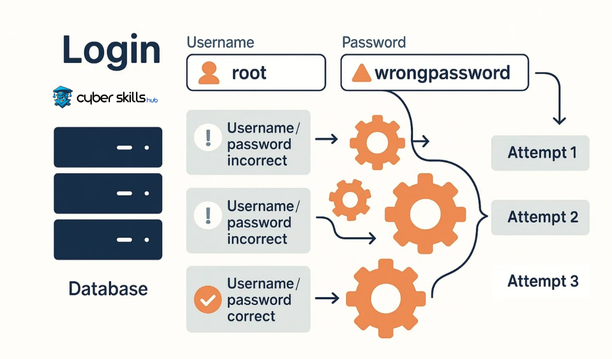
Automated scanning tools are useful for general vulnerabilities. However, such tools are often insufficient for business logic vulnerabilities. The detection of business logic vulnerabilities is specific to unique business processes that require complex and specialized controls. Standard automated scanning tools are therefore limited in their detection capabilities.
This is where manual analysis comes in.
Automated tools may ignore certain scenarios. Such scenarios – especially those that require human intervention – often need to be examined manually through various user scenarios and cleverly designed tests.
Where automated tools fall short, expert intervention is mandatory. For the detection of business logic vulnerabilities, manual comprehensive audits, mixed case testing and examination of logical user scenarios are much more effective than these tools and provide a detailed security assessment.
Ways to Avoid Vulnerabilities
The primary way to protect against business logic vulnerabilities is through a thorough review and control of every transaction process. Risk assessment procedures play a critical role in identifying potential vulnerabilities in advance. All user scenarios of the system should be thoroughly analyzed and all business logic flows within the application should be evaluated for security. Effective manual review methods in security testing processes and the practice of simulating logical scenarios are effective in preventing business logic vulnerabilities. In addition, the integration of security principles at every stage of the software development cycle and the implementation of continuously updated security policies with trained personnel provide proactive protection against business logic vulnerabilities.
To integrate security processes into the software development cycle, you can take a look at our article ‘Secure Development Process in Cybersecurity with DevSecOps’.
Secure Code Development Practices
Secure code development is vital to minimizing application vulnerabilities. Developers should carefully review security critical code fragments, using automated tools such as static code analysis and manual reviews.
Code review processes are of great value to improve security. Rigorous reviews by experienced developers help prevent bugs.
In particular, customized validation and sanitization mechanisms increase the resilience of applications against malicious inputs. They gain effectiveness both by controlling user input and by implementing data handling processes that comply with security standards.
Continuous training and knowledge sharing practices are also important at every development stage. Developers should be informed about current security trends and threats, and continuously trained on best practices.
Writing secure code requires following high order design principles. Secure architecture and design patterns help prevent unforeseen Business Logic Vulnerabilities, increasing the resilience of applications and their resistance to attacks.
Finally, the principle of reducing the attack surface plays a key role in security. By purging unnecessary code, features and components from the system, the number of potential vulnerability points is reduced, creating a solid foundation for successful defense.
Importance of Continuous Safety Training
Cybersecurity is a dynamic field that evolves rapidly.
Continuous security trainings are an inevitable requirement in this dynamic structure. Given the rapid developments in cyber security and the constant change in the threat environment, it is imperative that security professionals have up-to-date knowledge and skills. Trainings allow risk perception and awareness to be constantly refreshed, thus contributing to the continuous improvement of the effectiveness of information security processes.
Every new day brings a new security challenge.
Cyber security trainings play a critical role in renewing defense strategies. Up to date and in-depth knowledge is essential to effectively combat abstract and complex security threats, especially Business Logic Vulnerabilities. Such trainings make it easier to understand the tactics and techniques of cyber hackers and take proactive measures.
Security strategies should be continuously updatable.
Regular security trainings are vital to ensure business continuity and prevent Business Logic Vulnerabilities. Continuous monitoring of cybersecurity trends and the creation of security policies in line with these trends makes it possible to be prepared for the latest threat vectors. This is a critical investment for students in 2024 and beyond.
Frequently Asked Questions about Business Logic Vulnerability
What is the business logic weakness?
A business logic vulnerability refers to a unique flaw in the design of an application or system. These flaws allow attackers to exploit systems in unexpected ways.
How to identify business logic vulnerabilities?
Detecting business logic vulnerabilities is often not possible with automated tools and requires detailed manual investigations. Security experts identify potential vulnerabilities by carefully analyzing the application’s workflows and user behavior.
What methods can be applied to prevent business logic vulnerabilities?
To prevent business logic vulnerabilities, secure code development practices, detailed security testing and continuous security training are important. Every transaction process should be reviewed with risk assessment procedures and potential vulnerabilities should be identified in advance.
Can automated scanning tools detect business logic vulnerabilities?
No, automated scanning tools often fail to detect business logic vulnerabilities. Such vulnerabilities are inherent to complex and specialized business processes and require extensive manual audits and testing.
What is the most effective defense strategy against business logic vulnerabilities?
The most effective defense strategy against business logic vulnerabilities is to integrate security processes into the software development cycle, provide ongoing security training and update security testing with each new technology or workflow change.







