Currently Empty: $0.00

Imagine: a security researcher and hacker is swimming in a sea of possibilities, Shodan’s browser interface is open, on the verge of discovering an unexpected vulnerability.
This moment could turn into a groundbreaking discovery in the world of cybersecurity, as Shodan is like a flashlight that delves into the depths of internet-connected devices and services, bringing the unknown to light.
The Basics of Shodan
Shodan (Sentient Hyper-Optimised Data Access Network) is a search engine and security tool that scans internet-connected devices and systems to gather information. Users can analyze the status of these devices using parameters such as IP addresses, ports, and services.
Port numbers play a critical role in communication between devices on a network. Each port is a virtual point reserved for regulating a specific type of data flow in internet protocols. For example, web servers typically use port 80 for HTTP traffic and port 443 for HTTPS traffic. Thanks to Shodan’s port-based scanning capabilities, the status of services running on specific ports can be quickly analyzed, and potential security vulnerabilities can be identified.
This platform offers services specifically tailored to network security experts, cyber threat intelligence specialists, and individuals who conduct cyber attack tests such as pentesting. Advanced search filters can be used to quickly identify security vulnerabilities, misconfigurations, or unwanted open services in networks.
The search term ‘Shodan Dorking’ is an effective resource for finding specific information on the internet in a targeted manner. These dorks are used to discover open information sets within a specific network range or service.
Importance of Shodan in Cybersecurity
Shodan is a powerful search engine used to discover security vulnerabilities. It enables in-depth analysis of corporate networks and effective technology-based threat hunting. It is an indispensable resource for cybersecurity professionals.
Shodan’s comprehensive database plays a critical role in understanding network infrastructure and proactively identifying vulnerabilities. Its effective use is strategically important for protecting organizations against future attacks.
Shodan scans 500 million IP addresses every month.
As data leaks and cyber attacks continue to increase, Shodan plays a leading role in anticipating potential threats and developing cyber defense strategies. With its qualified information and databases, it helps security experts prevent service interruptions and costly breaches.
Shodan is indispensable for proactively detecting security vulnerabilities. For other important tools and their uses, check out our article on the Best Cybersecurity Tools.
Basic Research Conducted with Shodan
Research conducted through Shodan plays a fundamental role in identifying open devices and services on the internet. These devices range from virtual cameras to routers. Using Shodan, it is possible to understand how open your network is to the outside world.
Shodan dorks used to investigate vulnerabilities are configured with certain parameters. For example, the org:”target.com” command can collect information about all devices in an organization. In addition, the net:”” range can be used to investigate devices in a specific IP block.
Using dorks such as http.title:”” or ssl.cert.subject.cn:”” on Shodan, private data such as information in the sites’ SSL certificates, HTTP headers or cookie information can be accessed. When this information is evaluated in terms of security, it allows the detection of possible vulnerabilities.
In addition, various protocols with Shodan (ssl.alpn:””), specific web servers (http.favicon.hash:””), or devices that use a specific service (product:””) it is also possible to detect. This detected information increases the accuracy and depth of the security reviews conducted on the network.
However, dorks such as “Set-Cookie:phpMyAdmin” (lang=, PHPSESSID, webvpn, webvpnlogin=1, mongo-express=, user_id=, phpMyAdmin=, _gitlab_session) are commonly used by security professionals to determine access to potentially harmful administrative interfaces. Shodan actively participates in cybersecurity education and practices, contributing to the development of network security awareness and defense.
Shodan Dorking Operations
Shodan dorking is an effective search technique used to quickly identify devices connected to the Internet. With this technique, it is possible to perform customized searches thanks to the advanced query language of the search engine. With dorking, you can access detailed information about a specific IP address, network segment or service.
Search queries are enriched with special parameters and created in order to access a wide range of network information. For example, org:”target.com” devices belonging to a company targeted by the query,
- With http.title:”” you can quickly filter web pages with a specific title. Example titles include Grafana, Jenkins, MongoDB, JBoss, Django, Drupal, Joomla, Discourse, WordPress, Kibana, Elastic, Elasticsearch, Docker, Kubernetes, Redis, Citrix, Outlook, Owa, Index of /, DisallowedHost at /, InfluxDB, Apache Kafka, Apache Tomcat, Prometheus, Jira, Atlassian, Confluence, GraphQL, Gitlab, Git, Github, Postman, Swagger UI, nagios.
- http.html:”” şeklinde kullanarak, “anahtar kelime” ifadesini içeren web sayfalarını bulabilirsiniz. Örnek anahtar kelimeler arasında WordPress, Discourse, Grafana, Jenkins, MongoDB, JBoss, Drupal, Joomla, Kibana, Elastic, Elasticsearch, Docker, Kubernetes, Redis, Citrix, Outlook, Owa, Index of /, DisallowedHost at /, InfluxDB, Apache Kafka, Apache Tomcat, Prometheus, Logstash, Terraform, Jira, Atlassian, Confluence, GraphQL, Gitlab, Git, Github, Postman, Swagger UI, nagios bulunmaktadır.
- You can find web pages with a specific status code using http.status:””. Example status codes are included.
- http.status: “101” – Switching Protocols (for web socket hijacking control)
- http.status: “102” – WebDAV (For enabled WebDAV control)
- http.status:”200″ – OK
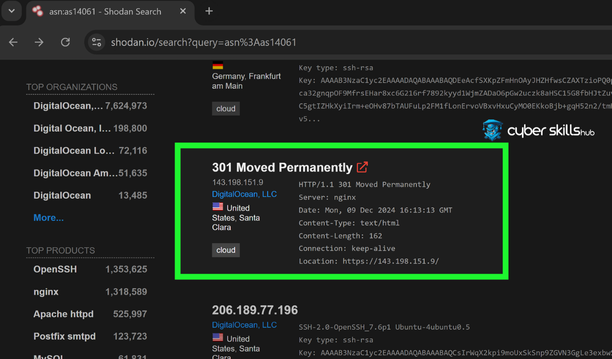
- http.status: “301” – Moved Permanently
- http.status: “302” – Temporarily Moved
- http.status: “307” – Temporary Redirection
- http.status: “308” – Permanent Orientation
- http.status: “401” – Unauthorized (for authorization bypass control)
- http.status: “403” – Banned (Forbidden for bypass control)
- http.status: “404” – Not found (For subdomain seizure control)
- http.status: “407” – Proxy Authentication is Required (For authentication bypass check)
- http.status: “426” – Upgrade Required (to control desync/smuggling attacks)
- http.status: “501” – Not applied (for desync/smuggling attacks control)
- port: using the form, you can find devices that have a specific port number. The sample port numbers are below.
- port: 21 “proftpd”: You can find devices that have a ProFTPD server.
- port:21“220” “230 Login successful.”: You can find devices that have an FTP server that contains 220 and 230 Login successful messages.
- port: 22 “OpenSSH”: You can find devices that have an OpenSSH server.
- port: 23 ”Telnet”: You can find devices that have a Telnet server.
- port: 25 “exim”: You can find devices that have an Exim server.
- port: 80 “Apache httpd”: You can find devices that have an Apache HTTP server.
- port: 445”SMB”: You can find devices that have an SMB (Server Message Block) server.
- port:1433 “Microsoft SQL Server”: You can find devices that have a Microsoft SQL Server server.
- port: 3306 “MySQL”: You can find devices that have a MySQL server.
- port:3389 “remote desktop”: You can find devices that allow remote desktop connection.
- port:6379 “authentication disabled”: You can find devices that have a Redis server with authentication disabled.
- port: 9200 “Elasticsearch”: You can find the devices that have the Elasticsearch server.
- port:27017 “MongoDB Server Information”: You can find devices that have a MongoDB server.
- http.favicon.hash: using the form, you can find devices that have a specific favicon hash value. Example favicon hash values are listed below.
- http.favicon.hash:”743365239″ – Atlassian
- http.favicon.hash:”628535358″ – Atlassian
- http.favicon.hash:”705143395″ – Atlassian
- http.favicon.hash:”981867722″ – Atlassian – JIRA
- http.favicon.hash:”552727997″ – Atlassian – JIRA
- http.favicon.hash:”-1581907337″ – Atlassian – JIRA
- http.favicon.hash:”-305179312″ – Atlassian – Confluence
- http.favicon.hash:”-1642532491″ – Atlassian – Confluence
- http.favicon.hash:”-1379982221″ – Atlassian – Bamboo
- http.favicon.hash:”1772087922″ – ASP.NET
- http.favicon.hash:”-1544605732″ – Amazon PHP Application – AWS Elastic Beanstalk
- http.favicon.hash:”-297069493″ – Apache Tomcat
- http.favicon.hash:”1382324298″ – Apple
- http.favicon.hash:”1232159009″ – Apple
- http.favicon.hash:”-1498185948″ – Apple
- http.favicon.hash:”-335242539″ – f5 Big IP
- http.favicon.hash:”878647854″ – BIG-IP
- http.favicon.hash:”1993518473″ – cPanel
- http.favicon.hash:”1544230796″ – cPanel Login
- http.favicon.hash:”-1153950306″ – Dell
- http.favicon.hash:”-167656799″ – Drupal
- http.favicon.hash:”1174841451″ – Drupal
- http.favicon.hash:”1611729805″ – Elastic (Database)
- http.favicon.hash:”1552860581″ – Elastic (Database)
- http.favicon.hash:”708578229″ – Google
- http.favicon.hash:”-1067420240″ – GraphQL Playground
- http.favicon.hash:”2124459909″ – HFS (HTTP File Server)
- http.favicon.hash:”731374291″ – HFS (HTTP File Server)
- http.favicon.hash:”1726027799″ – IBM Server
- http.favicon.hash:”81586312″ – Jenkins
- http.favicon.hash:”855273746″ – JIRA
- http.favicon.hash:”1627330242″ – Joomla
- http.favicon.hash:”-1950415971″ – Joomla
- http.favicon.hash:”366524387″ – Joomla
- http.favicon.hash:”-759754862″ – Kibana
- http.favicon.hash:”-1200737715″ – Kibana
- http.favicon.hash:”-267431135″ – Kibana
- http.favicon.hash:”1668183286″ – Kibana3
- http.favicon.hash:”75230260″ – Kibana4
- http.favicon.hash:”-1414475558″ – Microsoft IIS
- http.favicon.hash:”-1249852061″ – Microsoft Outlook
- http.favicon.hash:”442749392″ – Microsoft OWA
- http.favicon.hash:”-38580010″ – Magento
- http.favicon.hash:”902521196″ – Netflix
- http.favicon.hash:”396533629″ – OpenVPN
- http.favicon.hash:”-318947884″ – Palo Alto Networks
- http.favicon.hash:”602431586″ – Palo Alto Login Portal
- http.favicon.hash:”-476231906″ – phpMyAdmin
- http.favicon.hash:”-1010568750″ – phpMyAdmin
- http.favicon.hash:”1768726119″ – Outlook Web Application
- http.favicon.hash:”1356662359″ – Outlook Web Application
- http.favicon.hash:”-1616115760″ – ownCloud
- http.favicon.hash:”-1967743928″ – SAP ID Service: Log On
- http.favicon.hash:”1347937389″ – SAP Conversational AI
- http.favicon.hash:”-266008933″ – SAP Netweaver
- http.favicon.hash:”1642701741″ – Vmware Secure File Transfer
- http.favicon.hash:”1895360511″ – VMware Horizon
- http.favicon.hash:”-1255992602″ – VMware Horizon
- http.favicon.hash:”-991123252″ – VMware Horizon
- http.favicon.hash:”191654058″ – WordPress Under Construction Icon
- http.favicon.hash:”-1038557304″ – Webmin
- http.favicon.hash:”1453890729″ – Webmin
- http.favicon.hash:”1280907310″ – Webmin
- http.favicon.hash:”479413330″ – Webmin
- http.component we use the query to understand the technologies that a website uses (e.g. jQuery, Apache, WordPress, etc.) you can use it to detect. Sample technology and vulnerabilities that need to be searched for are listed below.
- To find the Template Injection:
- http.component:”AngularJS”
- http.component:”Ruby”
- http.component:”Ruby on Rails”
- http.component:”Python”
- To find PHP vulnerabilities:
- http.component:”PHP”
- To find SAP XSS CVE vulnerabilities:
- http.component:”SAP”
- To find log4j vulnerabilities:
- http.component:”Java”
- To find vulnerable databases:
- http.component:”MongoDB”
- http.component:”MySQL”
- To find Misconfigurations in the Admin Dashboard:
- http.component:”Python”
- http.component:”Django”
- To find API misconfigurations:
- http.component:”Open Graph”
- http.component:”Sentry”
- http.component:”Google Maps”
- To find the prototype pollution:
- http.component:”JQuery”
- http.component:”Node.js”
- http.component:”Loadash”
- To find caching problems:
- http.component:”Cloudflare”
- http.component:”Cloudfront”
- http.component:”Amazon Cloudfront”
- http.component:”cdnjs”
- http.component:”jsDelivr”
- http.component:”CreateJS”
- http.component:”Akamai”
- http.component:”JQuery CDN”
- http.component:”Varnish”
- http.component:”Netlify”
- http.component:”WP Rocket”
- To find Subdomain Takeovers:
- http.component:”Amazon S3″
- http.component:”GitHub Pages”
- To find deserialization vulnerabilities:
- http.component:”Microsoft ASP.NET”
- To find OAuth squatting:
- http.component:”Google Sign-in”
- http.component:”Apple Sign-in”
- http.component:”Facebook Sign-in”
- To find CMS related vulnerabilities:
- http.component:”WordPress”
- http.component:”Contentful”
- http.component:”Discourse”
- http.component:”Joomla”
- http.component:”Drupal”
- http.component:”WooCommerce”
- http.component:”Wix”
- http.component:”Shopify”
- http.component:”Magento”
- http.component:”Contentful”
- http.component:”Django CMS”
- http.component:”Craft CMS”
- To find the Template Injection:
- http.component_category with the query, you can find devices and systems that use components belonging to a specific technology category. Sample technology categories are listed below.
- http.component_category:”Programming languages”
- http.component_category:”Databases”
- http.component_category:”CDN”
- http.component_category:”Caching”
- http.component_category:”Javascript libraries”
- http.component_category:”Javascript frameworks”
- http.component_category:”Security”
- http.component_category:”Miscellaneous”
- http.component_category:”Maps”
- http.component_category:”CMS”
- http.component_category:”Message boards”
- http.component_category:”Web frameworks”
- http.component_category:”Authentication”
- http.component_category:”Web servers”
- http.component_category:”Payment processors”
- http.component_category:”WordPress plugins”
- http.component_category:”Blogs”
- http.waf you can send the query to a specific WAF product (e.g. ModSecurity, Cloudflare, AWS WAF, etc.) can be used to identify owned devices and servers. There are many techniques for bypassing WAF products. Usually, there may be vulnerabilities behind the WAF that can be easily bypassed. Sample WAF products are listed below.
- http.waf:”Cloudflare”
- http.waf:”Cloudfront”
- http.waf:”Akamai”
- http.waf:”AWS”
- http.waf:”Azure”
- http.waf:”Imperva”
- http.waf:”Nginx”
- http.waf:”Barracuda”
- http.waf:”F5″
- http.waf:”Sucuri”
- http.waf:”ModSecurity”
- http.waf:”Fastly”
- http.waf:”Citrix”
- http.waf:”FortiWeb”
- ssl.alpn the query can be used to find servers and services that support certain ALPN protocols. This Shodan dorku is especially used to control desync/smuggling attacks.
- ssl.alpn:”http/1.0″
- ssl.alpn:”http/1.1″
- ssl.alpn:”http/2″
- ssl.alpn:”http/2.0″
- ssl.alpn:”h2″
- ssl.alpn:”spdy/1″
- ssl.alpn:”spdy/2″
- ssl.alpn:”spdy/3″
- ssl.alpn:”http/0.9″
- ssl.alpn:”acme-tls/1″
- The query product:”” is a search parameter used to find devices or services associated with a specific product or software name.
- product:”Apache httpd”
- product:”OpenSSH”
- product:”ciscoSystems”
- product:”nginx”
- product:”BigIP”
- product:”Microsoft HTTPAPI httpd”
- product:”Apache Tomcat/Coyote JSP engine”
- product:”OpenResty”
- product:”Postfix smtpd”
- product:”MySQL”
- product:”Exim smtpd”
- product:”Kubernetes”
- product:”AkamaiGHost”
- product:”PostgreSQL”
- product:”MiniServ”
- product:”Grafana (Open Source)”
- product:”SQL Server Browser Service”
- product:”Apache Tomcat”
- product:”Node.js”
- product:”CouchDB”
- product:”MongoDB”
- product:”Memcached”
Such peaks play a critical role in the in-depth examination of network structures and the identification of potential vulnerabilities. Shodan dorking also functions as a source of cyber threat intelligence. Weak points that malicious actors can target, “Set Cookie: PHPSESSID” or “WWW-Authenticate”, “X-elastic-product: Elasticsearch”, “x-drupal-cache”, “access-control-allow-origin”, “X-Magento-Cache-Debug”, “kbn-name: kibana”, “X-App-Name: kibana”, “x-jenkins” it can be detected by using dorks like. The analysis of this information is considered as an essential element in the development of security measures and the taking of proactive measures against threats.
Effective Dorks and Their Uses
The effective use of dork in Shodan occupies an important place in tracking traces in network security. Using advanced dork, the examination of devices and configurations across a wide range of networks is critical in determining sensitive information. Dork customized with different criteria is also an indispensable tool for cyber security analysts’ threat hunting activities.
Encrypted traffic can be detected using a specific protocol, ssl.alpn:”” with. This allows early detection of security breach attempts in an intuitive sense. Dorks are a strategic tool for effectively controlling the security of critical information and services.
Narrowing down the results by service title, http.title:”” it is possible with the query. Header filtering is used in the classification of web applications and servers, as well as for reviews aimed at a specific target. This approach is suitable for surface area reduction and special purpose analysis.
Used to search for favicon hash values http.favicon.hash:””, allows matching via graphic icons specific to a specific website. Thanks to these types of dork, it becomes easier to distinguish institutions and services through web beacons.
Dorks such as net:”” (for example 104.16.100.52/32) are useful for distinguishing customized installations or management interfaces. It is used to identify specific network ranges and the services offered by devices in this range. It is effective in determining cyber threat areas through network architecture and accessible services.
In the limitation of corporate networks and the identification of the host names belonging to them hostname:””, asn:”” dork like stand out. This information helps to understand which service providers the network is configured under and which autonomous system it is connected to.
Detailed Scanning Methods with Special Filters
Scans performed on Shodan can be customized using filtering features. These scans can generate detailed information for specific targets or systems and provide valuable data for cybersecurity applications.
For example, ssl.cert.subject.cn :”” the filter can be used to analyze SSL certificates belonging to a specific domain. This analysis allows security professionals to track the duration of the certificate.
http.title:”” by searching the title information of web pages with the filter, it is possible to localize pages with specific titles. This method can play a critical role in the indentification of malicious or phishing pages.
asn:”” the filter allows to easily detect the devices of the relevant institution in the network by using an automation number. This information indicates the substructural structure of the network and its potential weak points.
Also, hostname:”” and ip:”” by using it, detailed information about a special host or IP address is accessed. This makes it possible to examine in detail the presence and services of an original device on the network.
In the complex and dynamic cyber security environment, these scanning techniques are vital for developing protection strategies against security threats. It offers great advantages especially in target-oriented analyses and risk assessments.
Shodan Command Line Tools
Besides the graphical user interface, Shodan offers command line tools (CLI) for advanced users. These tools are a powerful and fast method for querying the Shodan network via hand-written commands. For example, with the shodan host command, you can obtain service information for a specific IP address, and with the shodan stats –facets port:22 command, you can access the statistics of organizations using the SSH port. This allows critical information to be obtained in incident response or proactive security analysis.
Command-line tools are also valuable as part of automation and integrated systems. with the shodan alert create command, alerts for specific IP addresses or networks can be created and security events associated with them can be automatically tracked. In addition, batch data can be downloaded with the shodan download command and analyzed by filtering the outputs with shodan parse –fields. These capabilities provide in-depth data analysis and monitoring for cybersecurity professionals.
Quick Shodan Commands with CLI
Shodan provides CLI tools with a command-line interface so that security researchers can scan the large network database. These commands provide fast and effective solutions for network analysis and security monitoring.
- shodan host <IP> : It is used to get detailed information about a specific IP address.
- shodan stats -facets port: 22: Creates a warning for a specific IP address.
- shodan stats -facets org discourse: Displays the discourse statistics according to the org (organization) field.
- shodan domain <domain> : Displays devices with a specific domain name.
- shodan search “hostname:<domain>”: Investigates which services a domain name is associated with.
- shodan honeyscore<IP> : Displays the HoneyScore value of a specific IP address.
- shodan alert create “IP Alert<IP>” : Creates an alert for a specific IP address.
- shodan alert enable<alert_id> : Activates a specific alert.
- shodan alert CyberSkillsHub.com: CyberSkillsHub.com creates an alert for devices with a domain name.
- shodan download <dosya_adi> <sorgu> : Downloads the query results in bulk.
- shodan parse -fields<alanlar> -separator “,”<dosya_adi> : Displays the data in the downloaded file by filtering it. Thanks to these commands, operations can be automated and while saving time, speed is also gained in determinations.
- new_service, open_database, vulnerable, ssl_expired, internet_scanner, uncommon: Displays devices with certain features.
CLI, which has a high level of customizable features, plays a fundamental role in studies that require in-depth knowledge of cybersecurity. This efficiency of command-line use makes it possible for security professionals to devote their time to more important analysis.
You can check out the following resource for writing Shodan scripts with Python: Python Training Specialization Guide
Generated Alerts and Tracking
Shodan makes it possible to create warning systems according to certain criteria. These alerts are used to track changes related to the specified target.
The generated alerts serve to track activities in predefined targets, such as IP addresses or domain names. You will receive notifications for changes such as the status of a service, newly opened ports, or system updates.
The warning mechanism eliminates the need for security specialists to constantly check targets manually. This automatic tracking system allows for the early detection of potential threats or vulnerabilities.
Warnings are of great importance in the proactive management of cyber dangers. The capacity to intervene quickly in the face of sudden events is essential to protect the cyber health of institutions.
Thanks to the warnings created, threat hunting activities become more strategic. Security teams can be prepared in advance for cyber incidents through alerts.
Vulnerabilities and Penetration Testing
The process of identifying and assessing vulnerabilities plays a critical role in cybersecurity. Shodan is an important part of this process and provides penetration testers with detailed information about potential vulnerabilities in target systems. User-generated dorks (search queries) can reveal vulnerabilities in a specific IP range, domain names, or specific application footprints. Penetration testers can use this information to perform risk analysis and develop defensive strategies. The detailed datasets provided by Shodan are an effective tool for identifying vulnerabilities and taking precautions against cyber-attack scenarios.
Shodan and Vulnerability Detection
Shodan is used for risk assessment by scanning the vulnerabilities of devices connected to the Internet. In this way, it becomes possible to quickly identify networked systems and detect security vulnerabilities in advance.
For security professionals, Shodan provides the opportunity to analyze a wide range of devices such as servers, routers, webcams and other IoT devices. By using different query parameters, critical information such as network structures, open ports, software used and their versions can be accessed. This information plays an important role in isolating points vulnerable to exploitation by cyber hackers and closing security vulnerabilities.
Shodan dorks are used to investigate vulnerabilities in a more targeted manner. For example, it is possible to Decipher systems that use a specific software and host a known vulnerability with just a few search queries. In this way, companies and organizations can make an inventory of devices with security vulnerabilities and take action quickly.
A well-organized Shodan dork list strengthens the security posture against potential cyber attacks. These lists allow for more advanced analysis than regular system scans and provide customized threat intelligence. The detailed information provided by Shodan to create a complete security ecosystem is also among the indispensable tools of threat hunting and incident response teams.
Measures Against Potential Threats
A cybersecurity strategy requires a proactive approach, and the use of Shodan is also part of this strategy.
- Be aware of newly published security vulnerabilities by keeping your information up to date constantly.
- Open source intelligence (OSINT) scan your own network regularly with tools.
- In particular, regularly check your publicly accessible services and conduct vulnerability scans.
- Implement network segmentation and service restrictions that will minimize your attack surface.
- Use defense layers such as firewalls and access control lists effectively.
- Use defense layers such as firewalls and access control lists effectively.
- Minimize human-caused errors by creating an educated and informed user base.
The use of Shodan tools and dorks is also important for testing your defense mechanisms.
Cyber security training strengthens the security culture of your organization by increasing the level of knowledge of your staff.
Frequently Asked Questions About Shodan
What can be done with Shodan?
Shodan is a search engine that helps you search for devices and services on the internet. You can do many different things using Shodan. First, you can find public devices using Shodan. This includes devices ranging from webcams to industrial control systems. Finding these devices allows you to identify vulnerabilities and take necessary precautions. You can also use Shodan to assess the security status of devices. For example, by targeting an IP address or a country, you can find open ports, vulnerabilities, and even phishing attempts in that region. This information is useful for network security professionals, system administrators, and students studying cybersecurity.
For what purpose is the Shodan search engine used?
Shodan search engine is a search engine used to find and analyze devices on the internet. This search engine is used especially in the field of Cyber Security. Shodan is used to scan information about various internet-connected devices such as security cameras, servers, IoT devices. In this way, it is possible to find the IP addresses of these devices, open ports, security vulnerabilities, and sometimes even sensitive information such as username and password. Shodan also has many advanced features such as search filters, Advanced search features, and API integration.
What is Shodan eye?
Shodan Eye is an essential tool for cybersecurity researchers. Shodan is a service that has the ability to scan and analyze devices on the internet. Shodan Eye is an interface that visualizes the data provided by Shodan.







