Currently Empty: $0.00

What are CSRF (Cross Site Request Forgery) attacks and what types of attacks can they be associated with? This is comparable to an intruder breaking into your home without you realizing it and taking your cookie information. One of the effective solutions against this type of attack is the use of secure headers.CSRF Attacks
CSRF (Cross Site Request Forgery) is also known as XSRF.
These attacks usually aim to get a user to perform unauthorized actions. So, how can this be prevented? Remember the importance of strong session management, secure headers and a separate CSRF token for each session.
What is CSRF?
Cross-Site Request Forgery (CSRF) is an attack by malicious websites to perform unauthorized actions using users’ browsers. In this attack, usually your cookie values can be used for malicious purposes.
If you want to learn more about the basic principles of CSRF attacks, you can visit our Cybersecurity Fundamentals Training course.
CSRF attacks manipulate users’ credentials and allow unauthorized transactions, especially by exploiting session management and authentication vulnerabilities. These weaknesses often create vulnerabilities. Session management is the first line of defense against such attacks.
CSRF Definition
Cross-Site Request Forgery (CSRF) is a type of attack that allows a user to perform unauthorized actions through their browser. These attacks occur through requests made using the user’s authorized session.
The attacker sends an authorized request through the victim’s browser. This request is executed without the victim’s knowledge and often exploits vulnerabilities in web applications.
Misconfigured CORS policies can facilitate CSRF attacks.
These attacks can be difficult to detect because the requests may appear legitimate when sent through the victim’s browser. To guard against CSRF attacks, it is important to tighten security controls and strengthen authentication mechanisms. Defenses such as the SameSite cookie feature and token-based authentication methods can be used.
CSRF History
The first official reporting of the CSRF took place in the early 2000s. With the increase in web applications, security vulnerabilities started to attract attention.
- 2006: First large-scale CSRF attacks reported.
- 2008: OWASP first included CSRF among the most important web application vulnerabilities.
- 2013: Modern browsers started to introduce security mechanisms to protect against CSRF.
- 2017: Google Chrome released the “SameSite” cookie feature.
The history of CSRF attacks has led to increased awareness of web security and the development of protective measures.
Various security guidelines and protocols published during this period have contributed to the creation of more secure web applications.
With the evolution of technology and the diversification of security threats, there is a constant evolution in CSRF.
To learn more about the history of CSRF attacks and how they evolved, you can take a look at our Cyber Threat Intelligence Training page.
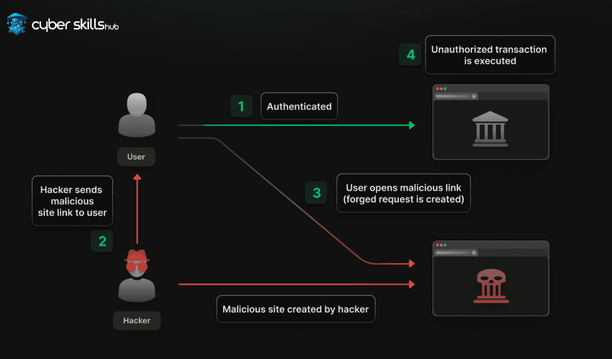
How CSRF Works?
CSRF is based on attacking a web application that a user is logged into in their browser through requests from an external source. In this type of attack, a malicious actor makes requests using the user’s credentials without their knowledge.
These attacks are usually simple, such as submitting a form or uploading an image. The attacker redirects the user’s browser to the target web application and performs unauthorized actions on its behalf. Another common method is to use special header configurations to hide attacks.
Attack Methods
CSRF attacks can be carried out in various ways.
One of the most common methods used in these attacks is to trick the user into clicking on a specific URL. For example, an email or social media message can be sent to redirect the user to a specific page. When the user clicks on this link, their browser automatically transmits session information and the actions requested by the attacker are performed.
Another method is the use of malicious JavaScript code.
Scripts embedded in JavaScript code are automatically executed when the page is loaded and send requests using the user’s login credentials in the background. This method becomes more effective especially when used in combination with XSS (Cross-Site Scripting) vulnerabilities.
Another common method is the hidden form submission technique. In this method, a small form embedded in a malicious web page is automatically submitted when the page is loaded and transactions are performed without the user knowing. Web applications without CSRF protection are very vulnerable to this type of attack. All of these methods require effective security measures to protect users and systems.
Example Scenarios
We can understand the effects of CSRF attacks more clearly through example scenarios. These attacks are usually carried out without the user’s knowledge and can have serious consequences.
For example, in 2016, a CSRF attack was carried out through a vulnerability detected in a banking application. Attackers sent a malicious link to users and captured their login credentials.
On one e-commerce site, attackers used users’ logins to place fraudulent orders. In this scenario, the attacker sends a malicious email, and when the user opens it, the transaction takes place.
Another scenario occurred on social media platforms. Automated messages were sent to users’ accounts, targeting other users on their friends lists.
Through these scenarios, we can better understand how dangerous CSRF attacks can be and the importance of security measures.
CSRF Blocking Methods
One of the most effective methods to protect against CSRF attacks is the use of CSRF tokens. CSRF tokens are a random value generated by the user’s client every time it sends a request to the server. Thanks to them, each session is made unique and attack attempts can be detected. In addition, the use of the SameSite cookie feature narrows the attack surface by ensuring that cookies are only sent on requests from the same site.
Other effective methods include double submit checks and requiring the user to re-authenticate for certain actions. In web applications, attacks can be made more difficult by adding additional layers of security such as CAPTCHA and a firewall (WAF). Detailed logging and anomaly detection are also critical methods to monitor CSRF attacks and take quick action.
Finally, informing users about such attacks through security awareness trainings indirectly reduces attack effectiveness. The integration of these methods creates a more effective and holistic security policy against CSRF attacks.
We recommend that you review our SOC L1 Training course to develop effective defense strategies against CSRF attacks.
Token Usage
Tokenization is an effective protection mechanism against CSRF attacks. This technique is widely used in modern web applications and increases the security of cookie data.
A random and unique token is generated by the server at the start of each session. This token is validated by sending it to the server with each request made by the client. The tokens are unique and unpredictable, making it difficult for attackers to guess and use this value.
This method can be used for all critical requests, especially form-based transactions. In particular, the correct integration of tokens in session management and authentication processes is important. This way, the legitimacy of each request can be checked with 100% accuracy.
Limiting the validity period of tokens also increases security. Limited duration tokens reduce the possibility of malicious use as they become invalid after a certain period of time. It also prevents the reuse of tokens.
As a result, token usage plays a critical role in preventing CSRF. With strong and unique tokens, web applications become more secure.

Verification Techniques
Various authentication techniques are used to prevent CSRF attacks. These techniques aim to increase security between the user and the server.
- CAPTCHA: Used to verify that the user is human.
- Token Validation: A unique token is generated for each request.
- Referer Check: Verification of the source from which requests come is provided.
- Dual Server-Side Storage: Authentication is done on both client and server side.
Each has its advantages and disadvantages. Proper use provides effective protection against attacks.
Token Verification is often one of the most effective methods. By using unique and unpredictable tokens, strong security is ensured.
Security Applications
Security practices used to prevent Cross-Site Request Forgery (CSRF) attacks play a critical role in improving the security of web applications. These practices include various methods such as Token Authentication, CAPTCHA, Referer Checking and Double Server-Side Storage.
Each of these applications offers different layers of security against CSRF attacks, making it harder for attackers to perform unauthorized operations.
Best Apps
Implementing best practices to protect against CSRF attacks is key to securing your web applications.
First, you should generate unique and unpredictable tokens for each request using token validation. These tokens should be regenerated for each form transaction, ensuring that the tokens submitted by the client are validated on the server side.
In addition, a Referer header check should be performed to verify that requests come from trusted sources. This method, in combination with token verification, greatly improves security.
Finally, adding a CAPTCHA to distinguish between human and bot, and dual server-side storage methods to ensure that tokens are stored on both the client and server side will help you add an extra layer of protection against CSRF attacks. These practices make it harder for attackers to perform unauthorized transactions and raise your security standards.
Current Tools
There are many up-to-date tools and technologies available to protect against CSRF attacks. These tools offer optimal ways to strengthen your web applications and increase security.
In recent years, tools such as OWASP CSRFGuard have come to the fore. OWASP CSRFGuard integrates into your application, generates a special token for each HTTP request and checks the authenticity of these tokens.
Another popular tool, Django CSRF Middleware, provides CSRF protection in the Django framework. This tool provides developers with basic protection mechanisms such as automatic token generation and validation.
In addition, Spring Security‘s CSRF protection modules provide effective protection for Java-based web applications and offer developers a wide range of security configuration options.
Up to date tools provide protection without compromising the user experience and without compromising security. Therefore, it is important to use these tools in your projects.
There are various methods to prevent CSRF attacks. For more information, you can visit the OWASP CSRF Page and the article What is CSRF and How to Protect.
Frequently Asked Questions About CSRF
What is a CSRF error?
In the cyber world, CSRF (Cross-Site Request Forgery) flaw poses a serious threat to the security of web applications. A malicious attacker can perform unwanted actions by abusing the user’s privileges. CSRF attacks usually involve the user clicking on a malicious link while they are in an authenticated state. In this case, a fake request is sent using the credentials of the valid user. For example, money can be transferred from bank accounts. In order for CSRF attacks to be successful, the attacker must have access to the user’s session. It is possible to perform these attacks by using session cookies and other authentication credentials. Therefore, CSRF attacks usually target older or inadequately secured web applications. In order to prevent CSRF attacks, it is recommended that developers use CSRF tokens. These tokens contain a unique value associated with the user session and are verified by the server on every request. It is also important to implement appropriate CORS (Cross-Origin Resource Sharing) and SameSite cookie policies.
What does CSRF stand for?
CSRF, or Cross-Site Request Forgery, is a common vulnerability in web applications. CSRF allows an attacker to send unsolicited commands through an authorized user’s browser. This type of attack poses serious risks, especially for web applications with session-based authentication mechanisms. Such attacks can be performed while the user is logged in.
What is CSRF?
CSRF is short for Cross-Site Request Forgery. This type of attack is based on performing unwanted actions on a web application that the user is logged into without their knowledge. A malicious attacker can trick the user into performing an action using their authorization. For example, they can transfer money without the user’s knowledge.
What is CSRF in Java?
Cross-Site Request Forgery (CSRF) is a type of attack that involves a malicious user sending malicious requests to web applications. This attack is carried out by using existing session information in the user’s browser. In Java web applications, defense mechanisms against CSRF attacks are important. Successful CSRF attacks can lead to data theft and account takeover. A common method to protect against such attacks is to use CSRF tokens. CSRF tokens are secret keys added to user forms and contain a unique value for each request. In this way, only authorized requests are accepted and the risk of attack is minimized.







