Currently Empty: $0.00
What is SSP: The Basics of Security Provider Packages

More than 80% of cyber attacks on our computer systems begin with the theft of credentials. At this point, SSP (Security Support Provider), a critical component of the security infrastructure of Windows operating systems, comes into play.
SSP, Windows sistemlerinde kimlik doğrulama ve şifreleme işlemlerini yöneten temel güvenlik bileşenidir. NTLM ve Kerberos gibi protokollerle çalışan bu sistem, Mimikatz gibi kötü amaçlı yazılımların hedefi haline gelebilir. Bu makalede, SSP’nin ne olduğunu, nasıl çalıştığını ve sistemlerimizi nasıl güvende tutabileceğimizi detaylı bir şekilde inceleyeceğiz.
Basic Structure and Components of SSP
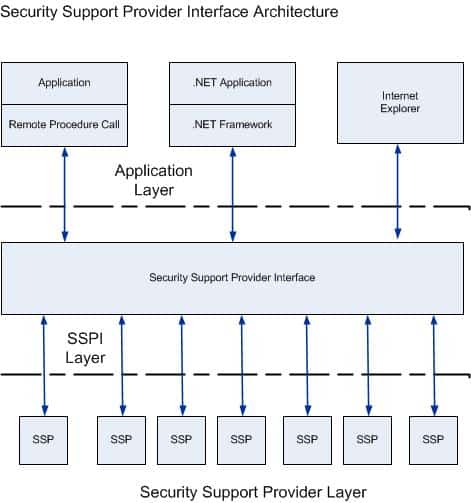
The Security Support Provider (SSP), which forms the basis of the Windows security architecture, is a dynamic link library that operates as a Win32 interface. This structure manages various security-related processes in our system and provides a common interface for multiple security providers. SSP interface architecture
The basic structure of SSP consists of the following components:
- Local Security Authority (LSA): A protected subsystem that manages user authentication and controls logon procedures.
- Security Support Provider Interface (SSPI): API that provides authentication, message integrity, and confidentiality services
- Security Packages: Modules containing authentication protocols such as Kerberos and NTLM
In Windows systems, SSP allows applications to use different security models. This allows an application to take advantage of various security models available on a computer or network without changing the security system interface.
To determine which SSPs are supported in our system and what capabilities these SSPs have, Windows Server uses the EnumerateSecurityPackages function. This structure allows for centralized selection and management of authentication protocols.
Windows Authentication Mechanisms
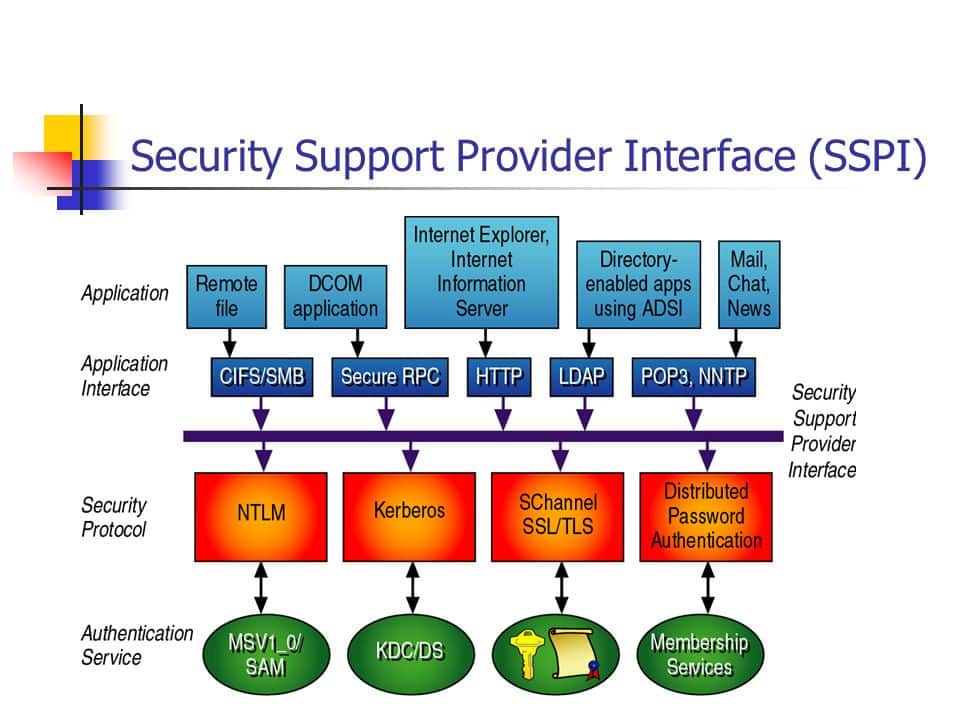
In Windows systems, authentication is managed through the Security Support Provider Interface (SSPI). SSPI is a set of Windows APIs that allow for the selection of a proxy and mutual authentication over any data transfer layer, such as TCP/IP sockets.
There are three basic security packages in the Windows authentication architecture:
- Kerberos Protocol: The default authentication protocol since Windows 2000.
- NTLM (Windows NT LAN Manager): A backup protocol that kicks in when Kerberos cannot be used.
- Schannel: Protocol used for web-based server authentication
Windows authentication is the preferred method for SQL Server authentication, and authentication is performed using NTLM or Kerberos. In particular, the Kerberos protocol uses the Negotiation Security Support Provider, which performs mutual authentication between the client and the service.
Time synchronization is important in the system because Kerberos rejects authentication when the time difference exceeds a certain period. In addition, all servers and clients must be members of the domain for Kerberos to function properly.
Windows authentication mechanisms work seamlessly with Microsoft Entra’s single sign-on (SSO) feature. This feature allows users of devices connected to the corporate network to log in automatically.
SSP Security Measures and Best Practices
When configuring SSP security measures, we must first enable SSL usage. SSL provides secure communication, especially during the transfer of user names and passwords over the network.
We must take the following basic measures in our security configuration:
- Monitoring and Logging: We must enable event logging by adding it to the web.config file.
- Cache Management: We should use a .NET Framework MemoryCache-based cache mechanism for fast response times.
- Identity Verification: Windows Identity Verification should be configured by default and disabled in double-hop scenarios.
In our system, we can manage Active Directory groups from SharePoint permission screens and use these groups for authorization. By assigning permissions to groups or roles, we can add AD users or groups to this structure.
We must organize regular training sessions to raise security awareness. In particular, we must raise awareness of phishing tests and social engineering attacks. It is critical that training sessions be tailored to business processes and followed up on regularly.
When managing IIS running processes, we must select the instance and use the “End Task” option to clear the cache data. Simply restarting IIS will not be sufficient because the system tends to reuse the current process.
Conclusion

SSP systems are an integral part of the Windows security architecture, securely managing user authentication processes. In our article, we took a detailed look at the basic structure and components of SSP and Windows authentication mechanisms.
To summarize what we have learned:
- Core components of SSP, such as LSA, SSPI, and security packages
- The roles of Kerberos and NTLM protocols in authentication
- Security measures such as SSL usage, tracking, and cache management
- Active Directory integration and authorization configurations
It is crucial to configure these structures correctly and keep them up to date in order to ensure the security of our systems. Through regular security audits, staff training, and monitoring of the latest threat intelligence, we can continuously strengthen our SSP-based security infrastructure.
As the Windows security architecture continues to evolve, SSP technologies are constantly being updated to counter new threats. It is therefore critical that security professionals keep their knowledge of SSP up to date.
Frequently Asked Questions About SSP
What is SSP and what is its role in the Windows security architecture?
SSP (Security Provider Package) is the core security component that manages authentication and encryption processes in Windows systems. It forms the basis of the Windows security architecture and provides a common interface for multiple security providers.
Which protocols are used in Windows authentication mechanisms?
There are three basic security packages in the Windows authentication architecture: Kerberos Protocol (default), NTLM (backup protocol), and Schannel (for web-based server authentication).
What measures can be taken to improve SSP security?
To enhance SSP security, it is important to enable SSL usage, perform monitoring and logging, optimize cache management, and configure Windows Authentication correctly.
How are Active Directory groups used in SSP security?
Active Directory groups can be managed from SharePoint permissions screens and used for authorization. By assigning permissions to groups or roles, you can add AD users or groups to this structure.
Why is it important to keep your SSP-based security infrastructure up to date?
Keeping the SSP-based security infrastructure up to date is critical to protecting against new threats and continuously strengthening the security of the system. Regular updates, security audits, and staff training ensure that the system is effectively protected.







